5.14.3 Implementing OAuth in Access Manager
Access Manager uses variable length access tokens and authorization codes. Client applications and web servers must not assume any fixed size of tokens and codes, and must allocate necessary memory to handle the token. The token size depends on the size of scope names. Some servers have size limitations on query strings and HTTP headers. Ensure that an application uses only necessary scopes to avoid any issue.
Implementation flow of OAuth in Access Manager
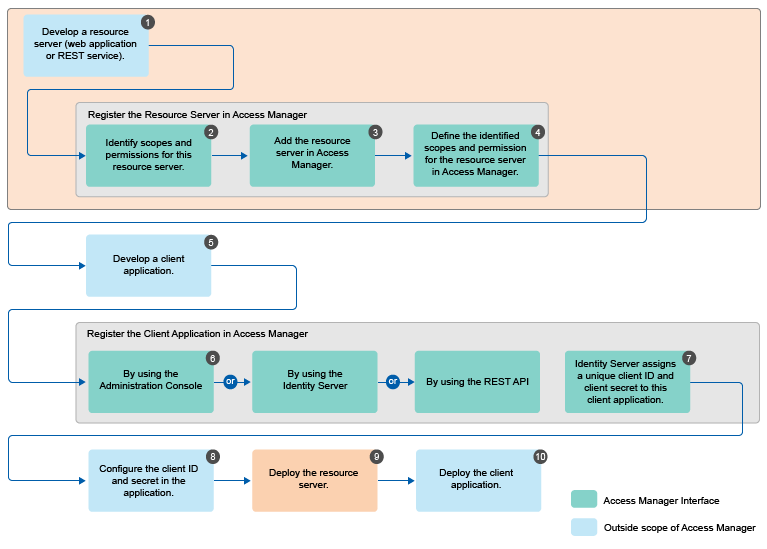
-
Develop a resource server (web application or REST service). (Application Developer)
-
Identify scopes and permissions for this resource server. (Application Developer or Administrator)
-
Add the resource server in Access Manager. See Adding a Resource Server. (Application Developer or Administrator)
-
Define the identified scopes and permissions for the resource server in Access Manager. See Defining Scopes for a Resource Server. (Application Developer or Administrator)
-
Develop a client application. (Client Application Developer)
-
Register the client application in Access Manager. You can register a client by using Administration Console (Administrator), Identity Server (Client Application Developer or Administrator), or REST API (Client Application Developer or Administrator). For information about registering a client application on Administration Console, see Managing OAuth Client Applications.
-
Identity Server assigns a unique client ID and client secret to this client application.
-
Configure the client ID and secret in the client application. (Client Application Developer or Administrator)
-
Deploy the resource server. (Application Developer)
-
Deploy the client application. (Client Application Developer)
For information about scenarios where you can implement this configuration, see OAuth Scenarios.
For more information about how to enable and configure OAuth in Access Manager for this implementation flow, see Configuring OAuth and OpenID Connect.