Controlling Access with Multiple Conditions
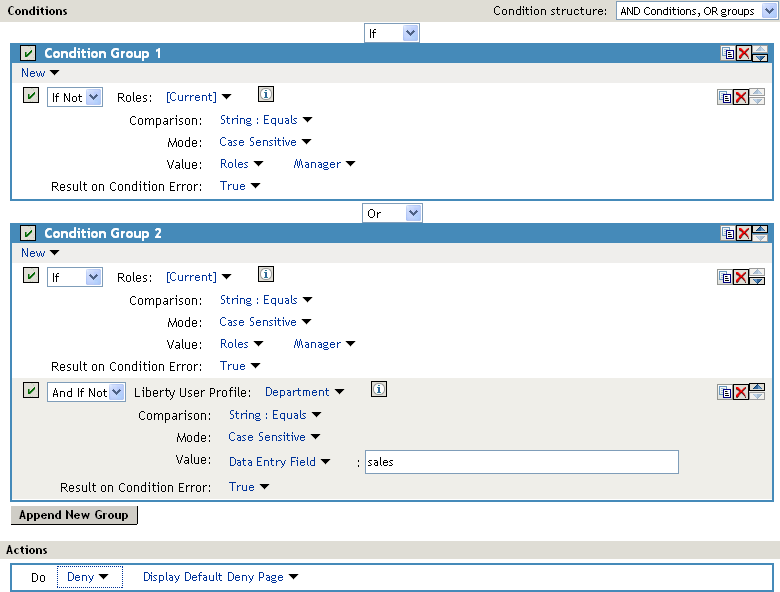
A policy requires multiple conditions when you have more than one condition for granting access. For example, you can identity your managers because they have been assigned the role of Manager, and you have a resource that only the sales managers must access. Such a policy requires two conditions for granting access: the Manager role and membership in the sales department. For a Deny rule, the rule needs two condition groups:
-
The first condition group matches all users who are not managers. This causes the Deny action to be applied.
-
The second condition group matches the users who are managers but don’t belong to the sales department. Because they match both conditions, the Deny action is applied. For these two condition groups to work with this logic, Condition structure is set to AND Conditions, OR groups.
The users who are managers and who belong to the sales department do not match either condition group. The Deny action is not applied, and they are allowed access.
Such a rule would look similar to the following:
This second condition group could be implemented as the second rule of the policy. If so, it must be set as a lower priority than the first rule. Because most systems would have more users than managers, the user rule would be used more frequently, so it must come first.