5.3 Kerberos Authentication
Kerberos is an authentication method that allows users to log in to an Active Directory domain. This authentication method provides a token. You can configure Identity Server to use this token as a contract. This provides single sign-on for the user between Active Directory and Identity Server.
Kerberos authentication is achieved using SPNEGO with GSS-API (JGSS). SPNEGO (RFC 2478 - Simple and Protected GSSAPI Negotiation implementation in Microsoft Windows 2000/XP/2k3/2k8) is a GSSAPI mechanism for extending a Kerberos single-sign-on environment to web transactions and services. It enables peers determine which GSSAPI mechanisms are shared and enables them select one and establish a security context with it. SPNEGO's most visible use is in Microsoft's HTTP Negotiate authentication mechanism.
The Kerberos module for Access Manager is implemented to securely negotiate and authenticate HTTP requests for protected resources. This enables seamless authentication (single sign-on) to Identity Server from enterprise-wide Microsoft Windows Domain Logon.
This section explains how to configure Active Directory, Identity Server, and Access Gateway for Kerberos authentication to a protected web server.
Figure 5-3 Example Kerberos Configuration
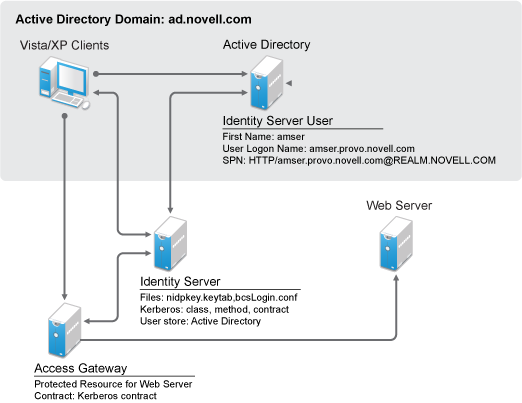
-
A user logs in to the computer.
-
The client computer gets a ticket granting ticket.
-
The user sends a request to the protected resource.
-
Access Gateway redirects the request to Identity Server for authentication.
-
The client sends a request to Identity Server.
-
Identity Server sends the 401 unauthorized response.
-
The client sends a request with the Kerberos service ticket.
-
Identity server decrypts the Kerberos ticket using the key tab file and then it performs an LDAP search with user principal name.
-
Identity Server receives the success status for the LDAP search, and then the user authentication is completed successfully.
-
Identity Server redirects the response to Access Gateway.
-
The user gets access to the protected resource.
Perform the following tasks to configure Kerberos authentication:
-
Configure Active Directory. See Configuring Active Directory.
-
Configure Identity Server. See Configuring Identity Server.
-
Configure clients. See Configuring the Clients.
-
Configure Access Gateway. See Configuring Access Gateway for Kerberos Authentication.