Using a Role to Create an Authorization
The simplest implementation of RBAC policies is to include roles as evaluated conditions when creating Authorization policies.
Suppose you belong to a company of 300 employees. 10 of them are managers. You can assign all employees to an Employee role and make it a condition of an Authorization policy with no restrictions. This policy permits access to web resources intended for all employees as shown in the following example:
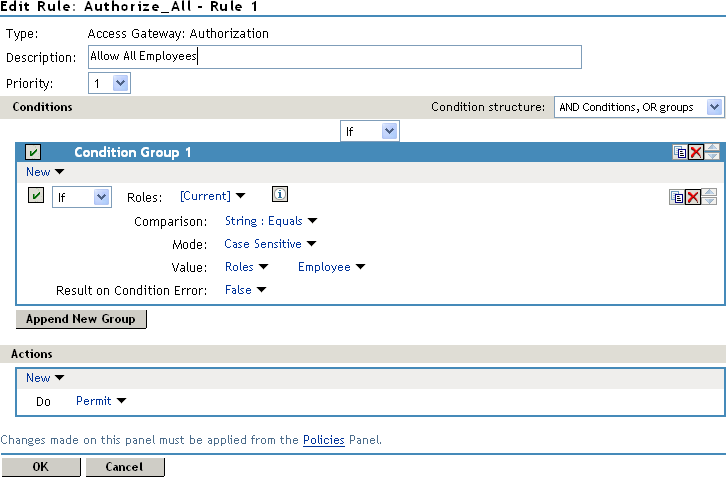
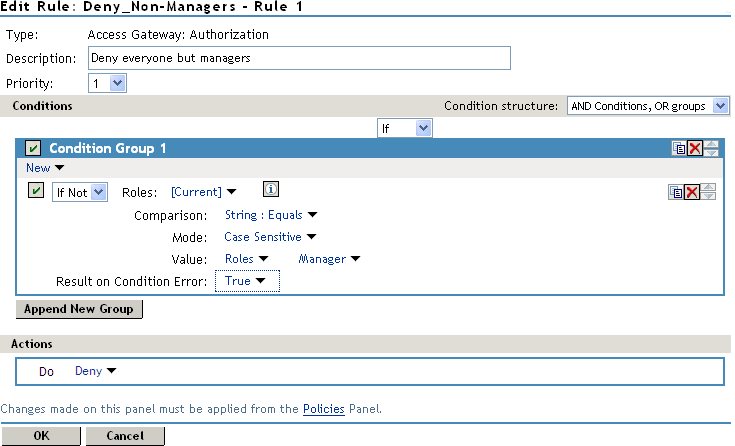
For web resources intended only for managers, create a role called Manager. (See Creating a Manager Role). Make the Manager role as a condition of an Authorization policy. This policy denies access to any employee that does not have the Manager role. The following example illustrates this. The operand for the governing condition logic is set to If Not.
After you create Authorization policies, assign the policies to the intended resources. See Assigning an Authorization Policy to a Protected Resource.