Scenario 2
Company XYZ is a customer of Access Manger. The employees of this company get authenticated to Identity Server. Each employee's mail attribute is retrieved from the user store. XYZ wants only user name part of the email address to be displayed on the Home page after authentication. This can be achieved by using the External Attribute Source policy.
XYZ completes the following steps:
-
Write an External Attribute data extension class and use the mail attribute as the parameter to the class.
For more information about data extension class, see Adding Policy Extensions.
-
In the data extension class, read the email address and parse the name identifier in it and return as an attribute. For more information about data extension example code and example code for this scenario, see The Policy Extension API in the NetIQ Access Manager 5.0 SDK Guide.
-
Define a shared secret for the name field of the email address.
For more information, see Section 2.4.3, Adding Custom Attributes.
-
Create an External Attribute Source policy for the data extension.
For more information about how to import the data extension class and configure the External Attribute Source policy in Identity Server, see Section 6.6.2, Creating an External Attribute Source Policy.
-
Create an Identity Injection policy.
For more information, see Section 6.4, Identity Injection Policies and Section 6.4.4, Configuring a Custom Header Policy.
-
Identity Server sends the user ID part of email address to Access Gateway.
In turn, Access Gateway or service provider sends this attribute to the configured web server. For example, John is an employee of XYZ. He provides his email address, john@mail-domain.com, as his user name. After authentication, only John will be displayed on the Home page.
The following diagram illustrates this scenario:
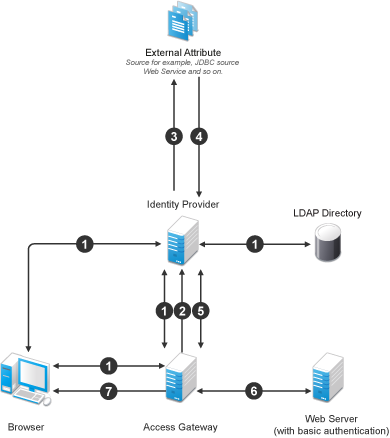
Workflow:
-
A user requests for a resource. Access Gateway redirects the request to Identity Server for authentication. Identity Server authenticates with LDAP servers and provides the assertion details to Access Gateway. In turn, Access Gateway verifies the assertion details.
-
The Home page in the resource is configured to display the user ID that has to be retrieved from Identity Server.
-
Identity Server determines whether the attributes can be retrieved from an external source. Identity Server sends the required details to the external source (in this example, an email address).
-
The external source returns the data. In this example, user ID part of the email address.
-
Identity Server sends the data that it has obtained from the external source to Access Gateway.
-
Access Gateway sends the data to the web server.
-
The web server returns the resource.