Encrypting the Token with the Resource server Key
If you want the resource server to decrypt and validate the OAuth token, you can encrypt the token by using resource server key.
You can encrypt an OAuth token by using the resource server’s key available on resource server’s JWKS (JSON Web Key Set) or a specific URL. To use resource server key, you must specify the resource server key or key set in Identity Server. When the access token is consumed, the resource server validates the token by decrypting the token. This gives the resource server the ability to decrypt the token without having to go to the authorization server (Identity Server) to decrypt or validate the token.
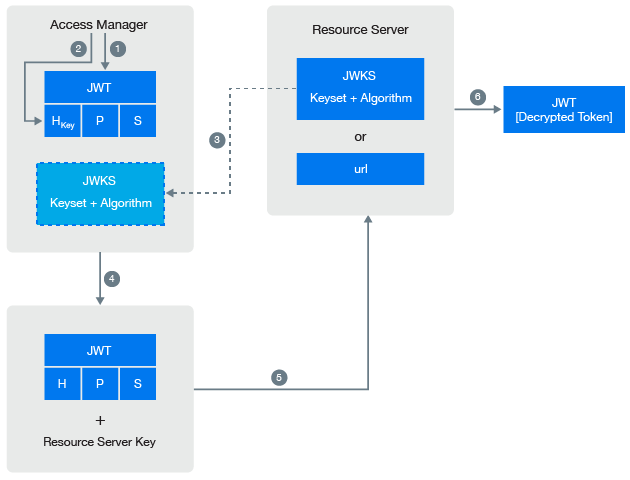
The following diagram illustrates how Access Manager leverages the resource server to decrypt a token:
-
Access Manager generates an unencrypted JWT token that includes Header, Payload, and Signature.
-
The token encryption algorithm specified in the resource server’s JSON Web Key Set is used for generating random symmetric key to encrypt this token.
This encrypted token contains the random key information in plain text.
-
Retrieve the JWKS information from the resource server.
-
Access Manager uses resource server public key that is defined in resource server’s JWKS to encrypt the random key information that is in plain text.
To view the Access Manager signing public key details in Administration Console, click OAuth & OpenID Connect > EndPoint Summary.
-
The resource server consumes the encrypted token.
-
The resource server uses its corresponding private key to decrypt the random key information.
The resource server uses the random key to decrypt the token. For more information about sample Java code to decrypt the token and validating token signature, see the Access Manager API guide.