5.9.1 How It Works
When a user logs in the first time, the user needs to provide an additional authentication. After the first successful authentication, Identity Server calculates the fingerprint for a device by using various user and device attributes, and registers the device. In subsequent login attempts by the same user, Identity Server validates the device by using the stored fingerprint.
You can configure to store the fingerprint in any of the following locations:
-
Browser: You can use this option in both risk-based pre-authentication scenarios and risk-based post-authentication scenarios. The fingerprint is valid for the duration specified in the rule. Each device has a single and unique fingerprint. So, this option does not work if a device is shared among more than one user and the fingerprint is configured to use the user DN parameter.
-
Server: You can use this option only in risk-based post-authentication scenarios. The user can use many devices to log in, such as desktop, laptop, and various hand-held devices. You can save up to 20 device fingerprints for a user.
Device Fingerprinting in Pre-Authentication Scenario
The following diagram illustrates how device fingerprinting works in pre-authentication scenarios:
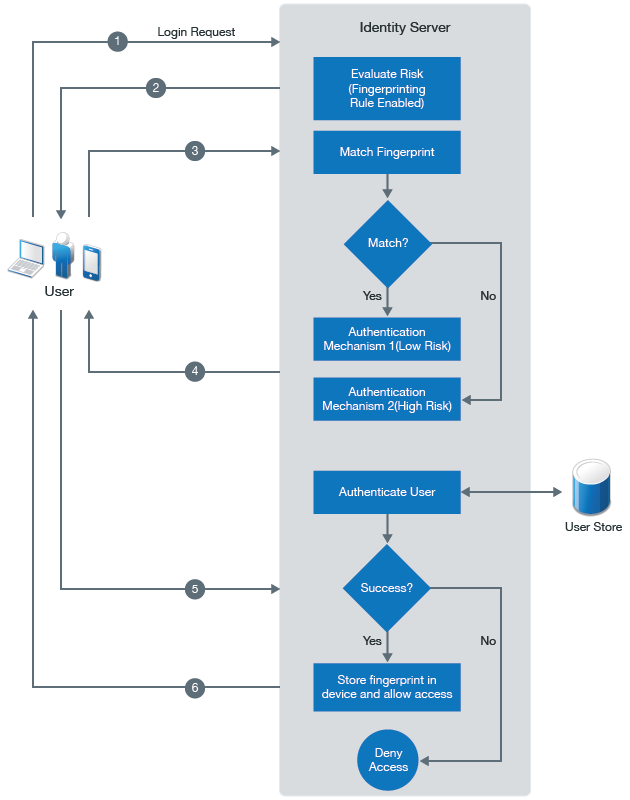
-
A user tries to log in.
-
Identity Server calculates the fingerprint of the device being used in the login attempt.
-
Identity Server matches this device fingerprint with the existing device fingerprint if any exists.
-
If the device fingerprint matches, the user is prompted to authenticate with an authentication mechanism configured for a low-risk login attempt. If the device fingerprint does not match, the user is prompted to authenticate with an authentication mechanism configured for a high-risk login attempt.
-
Identity Server authenticates the user.
-
If the authentication is successful, Identity Server saves the fingerprint in the device and redirects the user to the service provider. If the authentication fails, Identity Server denies the user request.
Device Fingerprinting in Post-authentication Scenario
The following diagram illustrates how device fingerprinting works in post-authentication scenarios:
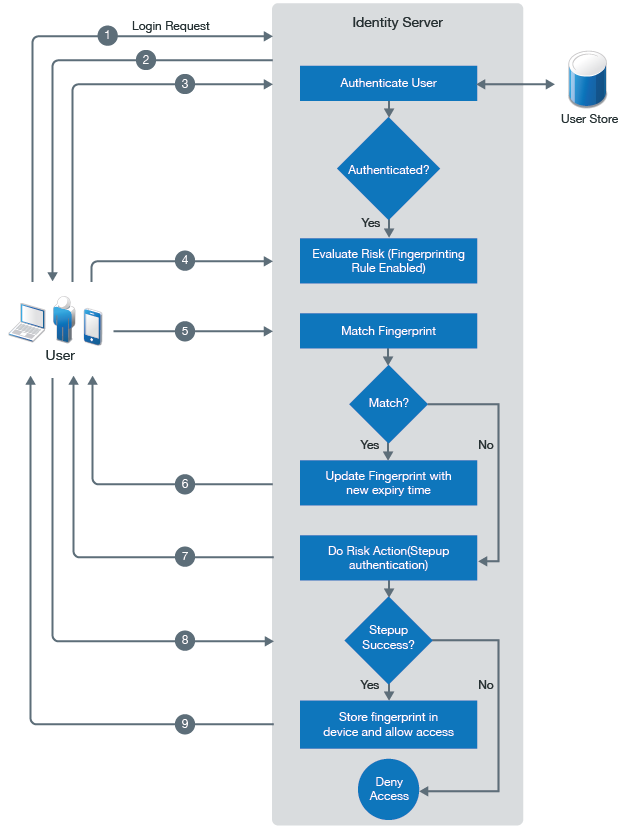
-
A user tries to log in.
-
The user specifies login credentials.
-
Identity Server authenticates the user.
-
After a successful authentication, Identity Server calculates the fingerprint of the device that the user has used for logging in.
-
Identity Server matches this device fingerprint with the existing device fingerprint if any exists.
-
If the device fingerprint matches, Identity server updates the expiry time of the existing device fingerprint and redirects the user to the service provider.
-
If the device fingerprint does not match, a risk is added to the session. The user is prompted for an additional authentication.
-
If the additional authentication is successful, Identity Server saves this device fingerprint and allows access to the resource.
-
If the additional authentication fails, Identity Server denies the user’s request.