5.14.4 OIDC Front-Channel Logout
Access Manager supports OIDC front-channel logout and is implemented as per OIDC specification. This feature enables the following two forms of logout request:
-
Identity Provider initiated logout request: Allows a user to log out from all the client applications when the user logs out at Identity Server.
-
Relying Party (client application) initiated logout request: When a user initiates logout from one client application, the user can authorize to log out from Identify Server and other logged-in applications. For more information, see OIDC RP-Initiated Logout.
Consider a scenario where multiple employees share a single device. A user named Alice logs in to the User Portal, and then accesses five client applications. At the end of her shift, she needs to log out of these applications so that Bob, another employee, can use the same device. Instead of logging out from each application individually, she can log out from the user portal. This logs her out from all five applications.
Alternatively, when she initiates logout from one client application, the client application initiates logout from Identity Server. Identity Server then triggers logout for the remaining four applications. A consent message is displayed to verify if she wants to log out from all applications. When she authorizes, she is logged out of Identify Server and the active applications.
The consent message is displayed when you enable the Require Logout Consent option in Global Settings. By default, this option is enabled. For more information, see Defining Global Settings.
To customize or localize a consent message, modify oauth2LogoutConsent.jsp using Advanced File Configurator.
The client application developer must register the logout_redirect_uri parameter for OIDC logout to enable this feature. The developer must also have the details of the following endpoints. Click Devices > Identity Servers > Edit > OAuth & OpenID Connect > EndPoint Summary to view the details of the endpoints.
-
Logout EndPoint
-
OpenID Metadata EndPoint
To configure the front-channel logout option, see Step 5 of Managing OAuth Client Applications.
To enable logout from multiple browsers, you must enable the Allow multiple browser session logout option under Devices > Identity Servers > Edit > General > Configuration > Limits.
You can also revoke refresh tokens issued during the front-channel logout for the user session using the Logout to revoke tokens option. By default, this option is disabled. For more information, see Defining Global Settings.
Figure 5-18 Identity Provider Initiated Logout Request
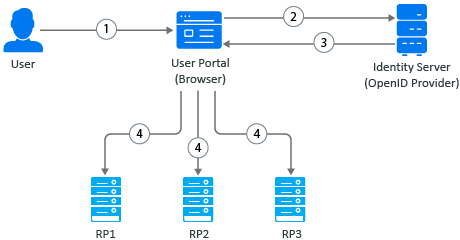
-
A user initiates logout at the Identity Server User portal.
-
The user agent sends the logout request to Identity Server.
-
Identity Server returns the logout response. The response contains iframes (logout URLs) for each relying party (RP1, RP2, and RP3). The relying party can be OAuth 2.0 or OIDC client application or SAML2 client application.
-
The browser agent generates responses and makes calls to each relying party’s logout URL.
Figure 5-19 Workflow of a Relying Party (client application) Initiated Logout Request
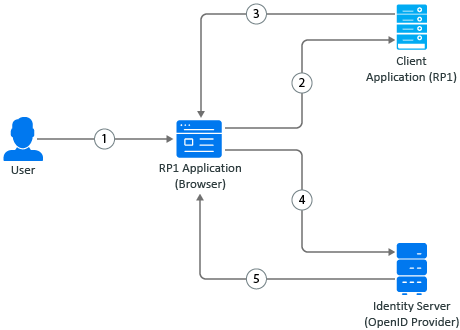
-
A user initiates logout at the client application.
-
The user agent sends the logout request to the client application.
-
The client application redirects the user’s browser agent for Identity Server logout.
-
The browser agent sends the logout request to Identity Server.
-
After the user grants consent, Identity Server terminates the user session, sends logout requests to other client applications (OAuth 2.0 or OIDC client application or SAML2 client application), and optionally redirects to the client application’s post-logout page.
Request Parameters
You can include the following parameters in the query string of a request:
|
Parameter |
Description |
Type |
Required |
|---|---|---|---|
|
id_token_hint |
A valid ID token issued for the user by Identity Server. |
String |
No |
|
post_logout_redirect_uri |
The redirect URI where the user is redirected after Identity Server logs the user out. This URI must match with the value provided during client registration. The id_token_hint parameter is required to redirect the user to this URI. If the logout request is sent without the id_token_hint parameter, the user is not redirected to post_logout_redirect_uri. |
String |
No |
|
state |
An optional value. This value is returned as a query parameter when the user is redirected to post_logout_redirect_uri. |
String |
No |
NOTE:
-
When a user session expires or does not exist in Identity Server, and the logout request does not contain the post_logout_redirect_uri parameter, the user is redirected to the Identity Provider's login page.
-
When a user session expires and a registered post_logout_redirect_uri parameter is specified in the logout request, the user is redirected to the configured post-logout page.
-
The logout request contains the id_token_hint parameter with a valid value, and the subject matches the current user session. However, the token is expired. The user session is then logged out at Identity Server and it redirects the user's browser agent to the configured post-logout page.
Sample Request 1
The client application initiates a logout without the post_logout_redirect_uri parameter. After logout, the user is redirected to the Access Manager's login page. The end_session endpoint supports both HTTP GET and POST methods.
GET/POST https://<idpcluster>:<port>/nidp/oauth/v1/nam/end_session
Sample Request 2
The client application initiates a logout. After logout, the user is redirected to the registered post_logout_redirect_uri.
GET https://<idpcluster>:<port>/nidp/oauth/v1/nam/end_session?
id_token_hint=${id_token}&
post_logout_redirect_uri=${post_logout_redirect_uri}&
state=${state}
For example:
GET https://<idpcluster>:<port>/nidp/oauth/v1/nam/end_session? id_token_hint=eyJhbGciOiJBMTI4S1ciLCJlbmMiOiJBMTI4R0NNIiw…..& post_logout_redirect_uri=https://client.example.org/logoutRedirect& state=JaysvoMyK71YfVG5
Sample Response
HTTP 302 Found
Location: https://{post_logout_redirect_uri}&state=${state}
For example:
HTTP 302 Found Location: The user will be redirect to the URI https://client.example.org/logoutRequest&state= JaysvoMyK71YfVG5
Error Conditions
-
If the id_token_hint parameter contains either invalid or encrypted ID Token, a 401 HTTP error response is returned with the Invalid ID Token error message.
-
If the post_logout_redirect_uri parameter value does not match with the registered client application, a 401 error response is generated.