Web Single Sign-On and STS
In this scenario, a web service client that resides as part of a web application within an enterprise tries to access services from other web service providers of the same enterprise. A user named Alice accesses to the web application through a browser and needs single sign-on access to other applications.
The following diagram illustrates this scenario:
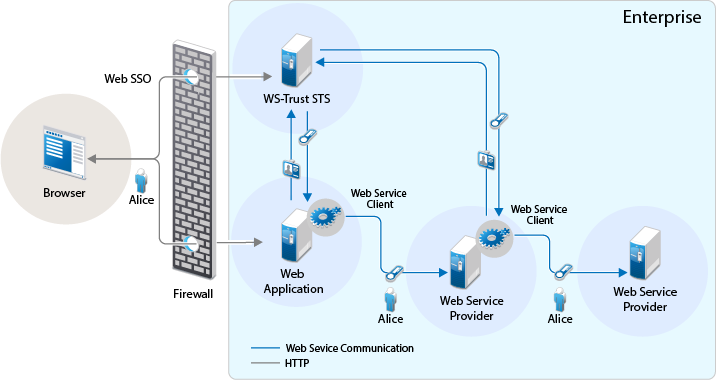
-
A web application sends a single sign-on authentication request to WS-Trust STS on behalf of Alice.
The web application is residing within the enterprise.
-
The web application passes the credentials corresponding to the single sign-on session to the web service client.
-
The web service client requests for security token by using the passed on credentials.
-
WS-Trust STS verifies the credentials. After checking the credentials, it verifies if the web service provider for which the token has been requested for is a trusted service provider. Then it issues a security token consumable by the service provider.
-
The web service client residing within the web application presents the token to the web service provider. The web service client caches the security token and then uses it in multiple requests to the web service provider.
-
The web service provider validates the token and sends the response to the web service client residing within the web application.
The tokens are included in SOAP messages.