Configuring SSL Authentication
When running your applications through AcuToWeb, you can embed Secure Socket Layer (SSL) support into your applications by specifying a matching private key and digital certificate file on the Gateway Services tab of the AcuToWeb Control Panel: select the service properties, then configure the SSL section.
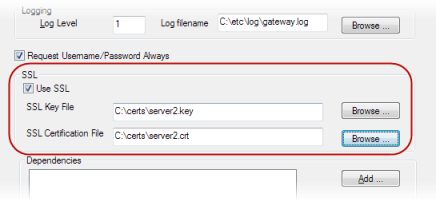
In order to create the digital certificate file, you require a private key and a certificate signing request; both of which can be generated using the following commands if you have the OpenSSL toolkit installed:
openssl genrsa -des3 -passout pass:xxxx -out server.pass.key 2048 openssl rsa -passin pass:xxxx -in server.pass.key -out server.key openssl req -new -key server.key -out server.csr
Once you have these two files, you must submit them to a Certificate Authority (CA), who can issue you with a genuine digital certificate. Visit the following web site for information about creating and using SSL certificates: https://www.digitalocean.com/community/tutorials/openssl-essentials-working-with-ssl-certificates-private-keys-and-csrs
For testing purposes
For testing purposes, you can instead use a self-signed digital certificate that does not require submission to a CA.
For more information about creating and using self-signed certificates, visit: http://www.akadia.com/services/ssh_test_certificate
To create a self-signed certificate from the private key and certificate signing request files created above:
openssl x509 -req -sha256 -days 365 -in server.csr -signkey server.key -out server.crt
When you are prompted for a challenge password, you can leave it blank; this password is used by the CA to authenticate the certificate owner when they want to revoke their certificate. As you are creating a self-signed certificate, it will never be revoked via the Certificate Revocation List.
Self-signed SSL certificates are not officially supported due to browser security limitations when using a secure WebSocket protocol. As this certificate is only designed for non-production applications, you can avoid the security limitations by lowering the browser's security settings; for example, if you are using Chrome, you can run it using the following command, which ignores certificate checking errors:
chrome.exe --ignore-certificate-errors
Although the certificate implements full encryption, you will receive a warning indicating that the certificate should not be trusted, which is why you should only use it on non-production applications.