Configuring Global Settings for the Fortify Jenkins Plugin
Note: These instructions describe a third-party product and might not match the specific, supported version you are using. See your product documentation for the instructions for your version.
To configure your Jenkins server so that it can analyze your project and upload results to Fortify Software Security Center using the Fortify Jenkins Plugin:
- Open a browser window and navigate to the Jenkins server URL.
- From the Jenkins menu, select Jenkins > Manage Jenkins > Configure System.
-
To analyze (translate or scan) your project locally with Fortify Static Code Analyzer
 A set of software security analyzers that scan source code for violations of security-specific coding rules and guidelines for a variety of languages. The rich data provided by the language technology enables the analyzers to pinpoint and prioritize violations so that fixes can be fast and accurate., create a Jenkins environment variable
A set of software security analyzers that scan source code for violations of security-specific coding rules and guidelines for a variety of languages. The rich data provided by the language technology enables the analyzers to pinpoint and prioritize violations so that fixes can be fast and accurate., create a Jenkins environment variable Building blocks for performance indicators; storage for measurement values that count issues, conditions, and similar categories of numeric data. to specify the location of the Fortify Static Code Analyzer executables. In Global properties, create the following environment variable:
Building blocks for performance indicators; storage for measurement values that count issues, conditions, and similar categories of numeric data. to specify the location of the Fortify Static Code Analyzer executables. In Global properties, create the following environment variable:- Name:
FORTIFY_HOME -
Value:
<sca_install_dir>where
<sca_install_dir>is the path where Fortify Static Code Analyzer is installed. For example, the default location on Windows isC:\Program Files\Fortify\Fortify_SCA_and_Apps_20.1.0.
- Name:
-
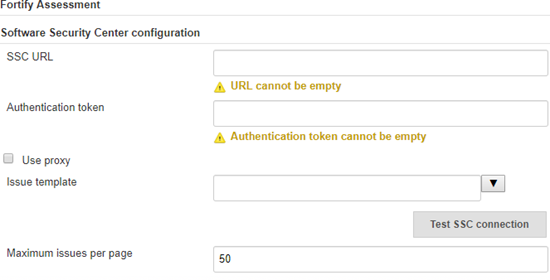
To upload results from a local analysis to Fortify Software Security Center, scroll down to the Fortify Assessment section, and then do the following in the Software Security Center configuration section:
-
In the SSC URL box, type the Fortify Software Security Center server URL.
The correct format for the Fortify Software Security Center URL is:
<protocol>://<ssc_host>:<port>/ssc(for example:http://my.domain.com:8080/ssc). -
In the Authentication token box, type the authentication token
 Unique keys that enable users to automate actions within Fortify Software Security Center without using passwords. The user requests a token, authenticates to the Fortify Software Security Center server, and receives back a string that is permissioned for a small set of time-limited actions. Fortify Scan Analytics also generates authentication tokens that are required to configure a connection between Scan Analytics and Fortify Software Security Center. of type CIToken generated for the Fortify Software Security Center server.
Unique keys that enable users to automate actions within Fortify Software Security Center without using passwords. The user requests a token, authenticates to the Fortify Software Security Center server, and receives back a string that is permissioned for a small set of time-limited actions. Fortify Scan Analytics also generates authentication tokens that are required to configure a connection between Scan Analytics and Fortify Software Security Center. of type CIToken generated for the Fortify Software Security Center server.See Preparing Fortify Software Security Center to Work with the Fortify Jenkins Plugin.
-
To connect to Fortify Software Security Center with a proxy server
 A computer that serves as an intermediary between a workstation user and the Internet. Requests for Internet services made by the client (the workstation) must pass through the proxy server, as also do the web server responses. You can use a proxy server to increase network security, provide adequate caching space, and regulate administrative control., select Use proxy, and then specify the proxy information.
A computer that serves as an intermediary between a workstation user and the Internet. Requests for Internet services made by the client (the workstation) must pass through the proxy server, as also do the web server responses. You can use a proxy server to increase network security, provide adequate caching space, and regulate administrative control., select Use proxy, and then specify the proxy information. -
From the Issue template list, select the appropriate issue template
 A template that determines how Fortify Software products prioritize issues. Prioritizing issues of a category or type helps guide the security team's audit and remediation activities. Fortify Software Security Center provides some standard templates. Users can employ them as is, modify them, and/or create additional templates. for your projects.
A template that determines how Fortify Software products prioritize issues. Prioritizing issues of a category or type helps guide the security team's audit and remediation activities. Fortify Software Security Center provides some standard templates. Users can employ them as is, modify them, and/or create additional templates. for your projects. Fortify Software Security Center uses the selected issue template when it creates new applications. The issue template optimizes the categorization, summary, and reporting of the application version
 A particular iteration of the analysis of a codebase as it applies to Fortify Software Security Center. An application always begins with a first version. An administrator adds new versions, as needed. data.
A particular iteration of the analysis of a codebase as it applies to Fortify Software Security Center. An application always begins with a first version. An administrator adds new versions, as needed. data. - To test the connection to Fortify Software Security Center, click Test SSC connection.
-
To specify the maximum number of issues to display per page in the results breakdown table, type a number in the Maximum issues per page box.
Note: You are not required to specify a value in the Maximum issues per page box at this time. You can change this setting later. This setting controls the Issue Breakdown table view. The default is 50 issues per page.
-
-
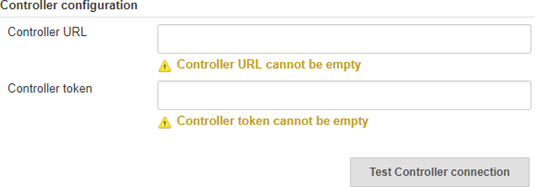
To perform a Fortify Static Code Analyzer analysis on a remote system, do the following in the Controller configuration section:
-
In the Controller URL box, type the ScanCentral Controller
 Server that receives a Fortify Static Code Analyzer mobile build session (MBS) and scan instructions from ScanCentral clients and routes the information to the ScanCentral sensors. URL.
Server that receives a Fortify Static Code Analyzer mobile build session (MBS) and scan instructions from ScanCentral clients and routes the information to the ScanCentral sensors. URL. Note: If you specify a URL in the Software Security Center configuration section (SSC URL), then the Fortify Jenkins Plugin automatically determines the ScanCentral Controller URL from Fortify Software Security Center and you do not need to provide a ScanCentral Controller URL.
The correct format for the ScanCentral Controller URL is:
<protocol>://<controller_host>:<port>/scancentral-ctrl(for example:https://myControllerHost.com:8443/scancentral-ctrl). -
In the Controller token box, type the Controller authentication
 Identity verification, typically with passwords. Authentication precedes authorization. token of type ScanCentralCtrlToken.
Identity verification, typically with passwords. Authentication precedes authorization. token of type ScanCentralCtrlToken. See Preparing Fortify Software Security Center to Work with the Fortify Jenkins Plugin for instructions.
-
- Click Save.