Fortify ScanCentral SAST Components
The following diagram illustrates a Fortify ScanCentral SAST environment.
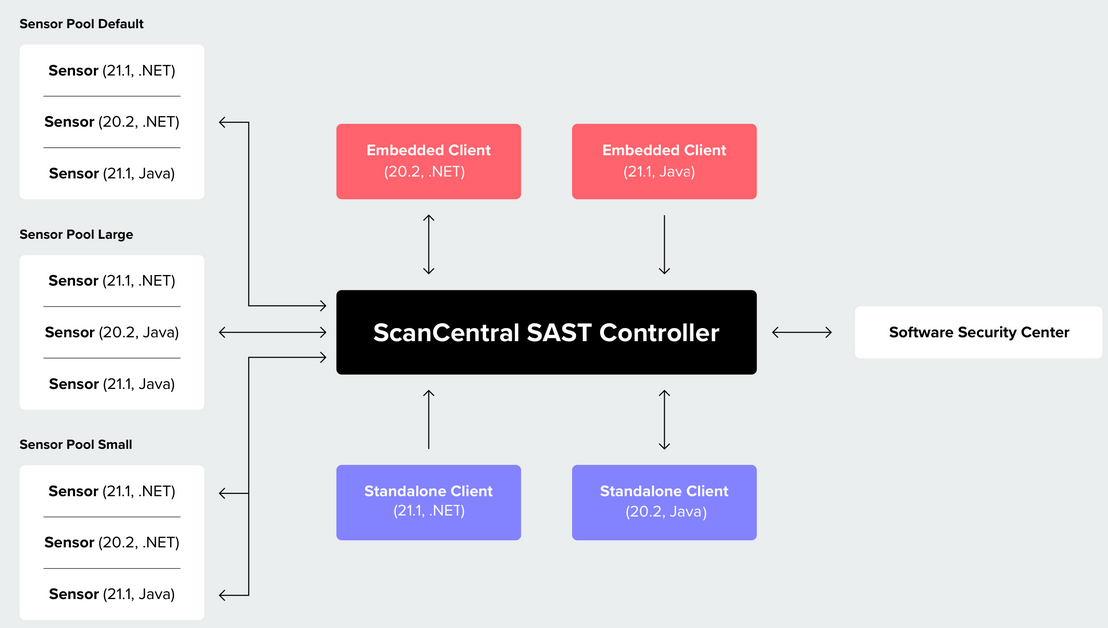
A Fortify ScanCentral SAST deployment includes the following three components:
Note: The minimum deployment requires three physical or virtual machines: a Fortify ScanCentral SAST client![]() Requesting program or user in a client/server relationship. For example, the user of a web browser is effectively making client requests for pages from servers all over the web. The browser itself is a client in its relationship with the computer that is getting and returning the requested HTML file. The computer handling the request and sending back the HTML file is a server., a sensor, and a Controller. A Fortify Software Security Center server is optional.
Requesting program or user in a client/server relationship. For example, the user of a web browser is effectively making client requests for pages from servers all over the web. The browser itself is a client in its relationship with the computer that is getting and returning the requested HTML file. The computer handling the request and sending back the HTML file is a server., a sensor, and a Controller. A Fortify Software Security Center server is optional.
- ScanCentral Controller
 Server that receives the Fortify Static Code Analyzer mobile build sessions and scan instructions from the ScanCentral SAST clients (or project packages with translation and scan instructions), routes the information to ScanCentral SAST sensors, and (optionally) uploads scan results (FPR files) to Fortify Software Security Center.: A standalone web application
Server that receives the Fortify Static Code Analyzer mobile build sessions and scan instructions from the ScanCentral SAST clients (or project packages with translation and scan instructions), routes the information to ScanCentral SAST sensors, and (optionally) uploads scan results (FPR files) to Fortify Software Security Center.: A standalone web application A customer codebase evaluated by Fortify software. The top-level container for one or more application versions. When you work with a new codebase, the application and first application version are automatically created. An application includes one or more application versions that users create and configure. that receives the Fortify Static Code Analyzer mobile build sessions (MBS
A customer codebase evaluated by Fortify software. The top-level container for one or more application versions. When you work with a new codebase, the application and first application version are automatically created. An application includes one or more application versions that users create and configure. that receives the Fortify Static Code Analyzer mobile build sessions (MBS A mobile build session (MBS file) created in the Fortify Static Code Analyzer translation phase includes the files required for analysis and enables you to scan a project on a different machine (than the translation phase).) and scan instructions from ScanCentral SAST clients (or project packages with translation and scan instructions), routes the information to sensors, and (optionally) uploads scan results (FPR
A mobile build session (MBS file) created in the Fortify Static Code Analyzer translation phase includes the files required for analysis and enables you to scan a project on a different machine (than the translation phase).) and scan instructions from ScanCentral SAST clients (or project packages with translation and scan instructions), routes the information to sensors, and (optionally) uploads scan results (FPR Fortify project results. The Fortify Static Code Analyzer output file format. files) to Fortify Software Security Center. For more detail, see About the Controller.
Fortify project results. The Fortify Static Code Analyzer output file format. files) to Fortify Software Security Center. For more detail, see About the Controller.
-
ScanCentral SAST client: A build machine on which Fortify Static Code Analyzer translates your code and generates Fortify Static Code Analyzer mobile build sessions (MBS). The translated source code, along with optional and required data, such as custom rules
 Rules that extend the functionality of Fortify Static Code Analyzer and the Secure Coding Rulepacks. Custom rules enable you to enforce proprietary security guidelines or analyze a project that uses third-party libraries or other pre-compiled binaries that are not already covered by the Secure Coding Rulepacks. and Fortify Static Code Analyzer command-line arguments, are uploaded to the ScanCentral Controller. For more detail, see About Clients.
Rules that extend the functionality of Fortify Static Code Analyzer and the Secure Coding Rulepacks. Custom rules enable you to enforce proprietary security guidelines or analyze a project that uses third-party libraries or other pre-compiled binaries that are not already covered by the Secure Coding Rulepacks. and Fortify Static Code Analyzer command-line arguments, are uploaded to the ScanCentral Controller. For more detail, see About Clients. - ScanCentral sensors: Distributed network of computers set up to receive scan requests and analyze code using Fortify Static Code Analyzer. A sensor accepts either a mobile build session
 A mobile build session (MBS file) created in the Fortify Static Code Analyzer translation phase includes the files required for analysis and enables you to scan a project on a different machine (than the translation phase). (MBS) file and performs a scan, or it accepts a prepared package that contains sources and dependencies, which it translates and scans. For more detail, see About Sensors.
A mobile build session (MBS file) created in the Fortify Static Code Analyzer translation phase includes the files required for analysis and enables you to scan a project on a different machine (than the translation phase). (MBS) file and performs a scan, or it accepts a prepared package that contains sources and dependencies, which it translates and scans. For more detail, see About Sensors.
-
Sensor pools: To scan code, sensors must belong to a sensor pool
 A group of ScanCentral sensors, grouped based on any criteria, which you can then target for scan requests. Example: A sensor pool consisting of machines with a lot of physical memory is used for scan requests that require a lot of memory.. A sensor pool consists of one or more sensors, grouped based on any criteria, which you can then target for scan requests. Example: You can create a sensor pool that consists of machines with a lot of physical memory to use for scan requests that require a lot of memory. If you do not specifically add a sensor to a sensor pool, it is automatically assigned to the default sensor pool.
A group of ScanCentral sensors, grouped based on any criteria, which you can then target for scan requests. Example: A sensor pool consisting of machines with a lot of physical memory is used for scan requests that require a lot of memory.. A sensor pool consists of one or more sensors, grouped based on any criteria, which you can then target for scan requests. Example: You can create a sensor pool that consists of machines with a lot of physical memory to use for scan requests that require a lot of memory. If you do not specifically add a sensor to a sensor pool, it is automatically assigned to the default sensor pool.
To successfully deploy Fortify ScanCentral SAST, in addition to installing Fortify Static Code Analyzer, complete the following tasks in the order listed here:
- (Recommended, but not required) Deploy a (or connect to an existing) Fortify Software Security Center instance
- Install the Fortify ScanCentral SAST Controller
- Create ScanCentral SAST sensors
 Distributed network of computers set up to receive Fortify Static Code Analyzer mobile build sessions and scan instructions (or project packages with translation and scan instructions) from the ScanCentral SAST clients and scan code using Fortify Static Code Analyzer. If your applications are written in a supported language, the sensors can also perform the translation phase.
of the analysis.
Distributed network of computers set up to receive Fortify Static Code Analyzer mobile build sessions and scan instructions (or project packages with translation and scan instructions) from the ScanCentral SAST clients and scan code using Fortify Static Code Analyzer. If your applications are written in a supported language, the sensors can also perform the translation phase.
of the analysis.
Instructions for completing these tasks are provided in the following sections. For information about hardware and software requirements for these components, see the Micro Focus Fortify Software System Requirements document.