7.1.1 How the Security Proxy Server works
The Security Proxy provides token-based access control and encrypted network traffic to and from user workstations.
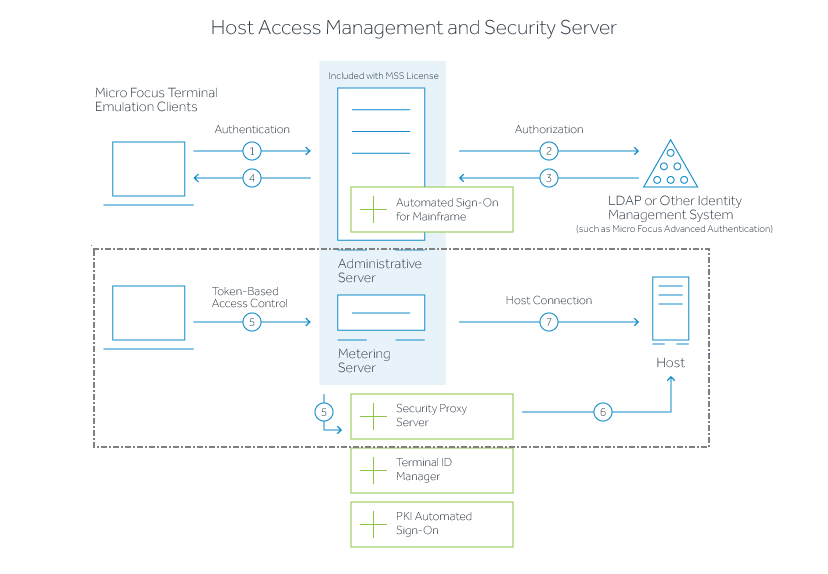
The following diagram highlights the Security Proxy (steps 5 and 6) in the context of the overall Management and Security Server set up.
-
User connects to the Administrative Server.
-
User authenticates to a directory server (LDAP/Active Directory) or other identity management system (optional).
-
The directory server provides user and group identity (optional).
-
The Administrative Server sends an emulation session to the authorized client.
.......................................................................................................................................................
-
When the Security Proxy Server is configured for use by a session, the emulation client makes a TLS connection to Security Proxy and sends it a signed session token.
-
The Security Proxy Server validates the session token and establishes a connection to the specified host:port. The security proxy encrypts the data before forwarding it back to the user.
Note: The connection between the Security Proxy and the host is not encrypted — unless End to end encryption is selected in the session configuration.
.......................................................................................................................................................
-
When no Security Proxy is present or a session is not configured to use it, the authorized user connects directly to the host.
Related topics