1.4 Putting It All Together
When properly configured, eDirectory objects and Linux User Management technology let you manage access to Linux resources on the network. Here's how it works:
-
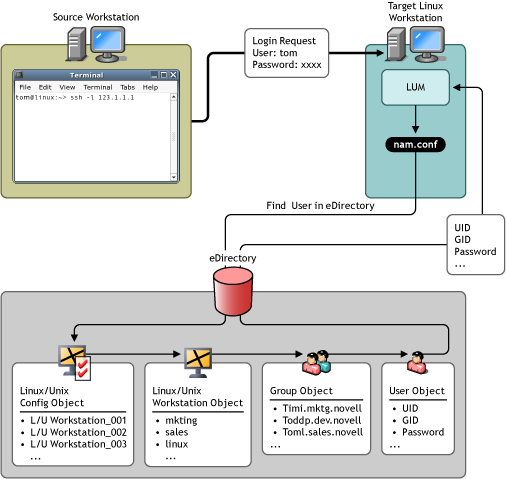
At a source workstation, the user launches a program (such as SSH or FTP) that provides login access to another computer.
-
When prompted by the login program, the user enters his or her username and identifies the name or address of a target workstation. For example, the user might launch SSH, enter tom as the username, and the address of a target workstation with the following command:
ssh -l tom 10.10.1.1
-
The target workstation receives the login request, but before granting access, it must find the requester's full context username and verify that the password is correct. This login information is stored in eDirectory instead of on the target workstation.
-
To find the requester's login information, the target workstation (configured with Linux User Management) performs the following actions:
-
Finds the location of the Linux/UNIX Workstation object in eDirectory as listed in the local nam.conf file.
-
Searches the groups approved for access listed in the Linux/UNIX Workstation object to find the requester's username.
For example, if the login request is from a user named Tom, the list of groups is searched until a User object with the username Tom is found.
-
Submits the requester's password for verification against the user information stored in eDirectory.
-
Grants the login request by using eDirectory login information, such as UID, GID, home directory, and preferred shell.
The following illustration shows how Linux User Management, eDirectory, and PAM all work together to let users log in to target workstations on the network.
Figure 1-1 Logging In to Target Workstations
-