Exploring Deployment Options
The Reflection Deployment Guide includes best practices, instructions, and other information for a number of deployment environments.
Some content may apply to you regardless of your deployment environment. You may be interested in:
Finding Information Specific to your Deployment Environment
Use these guidelines to find the sections that pertain to your deployment environment.
| If you are using... | See |
|---|---|
| A share that users install from | Setting up a simple deployment in this guide. |
| A reference image | Information about how to select installation options and how to customize settings in the Reflection Help: Installation Get Started How Do I? |
| Group Policy | Information about how to install and use templates for locking down Reflection and instructions for publishing: Control Access to Settings and Controls with Microsoft Group Policy Publish with Active Directory |
| Setup.exe | Information about setup and instructions for deploying on the Setup command line: Setting up the Reflection Administrative Tools Deploy with the Reflection Setup program |
| MSI Command line | Information about prerequisites when deploying with MSI directly. Deploy with MSI |
| Host Access Management Server | Information about setting up Reflection to use centrally managed sessions. Use a Centralized Management Server |
Creating and Customizing Reflection Sessions
Reflection stores the information required to connect to hosts in configuration files called session document files. You can create session document files that have connection information and other settings and then deploy them independently of your installation.
You can also customize session document files to use custom keyboard maps, controls, themes, and other settings. To customize these settings, see Create and Customize Session Documents.
Using Compound Session Document Files
By default, Reflection saves custom settings for QuickPads, keyboard maps, themes, mouse maps, hotspots, and ribbons in separate configuration files that you will need to deploy along with the session document files that reference them. But you can simplify your deployment by saving your session documents as compound session files, which include all of these settings.

Compound Session Document files include all of the customized settings for QuickPads, keyboard maps, themes, mouse maps, hotspots, and ribbons. These files allow you to deploy your sessions without having to deploy dependant files for these settings.
Session Document files save these settings in separate files. If you save sessions using this default, you'll need to make sure that you deploy the custom files to the correct locations as shown in Customized Files that Must be Deployed to Specific Locations.
Compound files are easier to deploy because you don't have to deploy the supporting files. Regular session files offer more flexibility for sharing common configurations. For example, you can reference one custom keyboard map from several regular session files. With compound session documents, you have to recreate the custom settings in each file.
note
Not all custom settings are saved in compound session files. For example, settings such as ssh_config and ssh_known_hosts required for Secure Shell connections are not saved in these files.
Creating Custom Templates
Templates provide default configurations for connecting to specified file types. Micro Focus Reflection Desktop ships with default templates for each of the supported session types included with your product. You can also create and deploy custom templates designed to meet the needs of your users. See Set up Session Templates.
Customizing Reflection
You can customize Reflection by changing it's appearance and functionality and by locking down access to settings and controls.
You can change the appearance and basic functionality of the main Reflection window in a variety of ways, including specifying startup macros and actions.
You can also change the appearance of the window (for example, by opening Reflection in TouchUx mode).
For more, see Customize the Reflection Workspace.
Locking Down Settings and Controls
You can lock down Reflection to limit access to settings and controls so that they are not available to users. This allows you to simplify support requirements and resolve security concerns.
To prevent a user from changing a setting, you set the permission level for that setting or control to Restricted. For example, you could restrict the users' ability to modify security settings.
As shown below, the restricted settings are grayed out. The security shield and the Change currently disabled settings link indicate administrative access is required to change them.
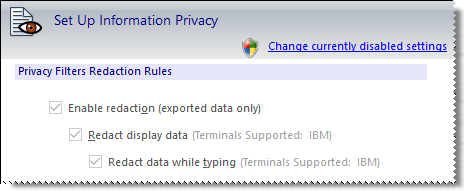
For more about locking down settings and controls, see:
-
Control Access to Settings and Controls with Reflection Administrative Tools
-
Control Access to Settings and Controls with Microsoft Group Policy
Designing and Creating Secure Solutions
Reflection provides support for a number of secure solutions. You can set up Reflection to protect your working environment from information theft, and your data from potential damage caused by opening documents from non-trusted sources, using the following methods:
-
Creating secure sessions for data in motion enables secure, encrypted connections using secure protocols such as SSH or TLS.
-
Setting up Information Privacy to mask sensitive data helps enable compliance with PCI-DSS requirements.
-
Defining trusted locations from which you can safely open (and store) documents protects data from potential damage caused by opening documents from non-trusted sources.
-
Setting up macro and API security controls access to the Reflection API.
Creating secure sessions for data in motion
Set up secure sessions for a number of secure protocols including FIPS 140-2 validation, TLS encryption, SSH, Kerberos, SOCKS, and PKI. See Create TLS or SSH Session Documents.
Setting up Information Privacy
Set up Information Privacy to help comply with PCI-DSS requirements, including redaction of sensitive data such as credit card or social security numbers.

You can also set up the Reflection API to log access to unredacted data.
See Set up Information Privacy.
Defining trusted locations
Define Trusted Locations to differentiate safe files from potentially harmful files. When a file is in a trusted location, it's files are assumed to be safe. If you try to save a file in a location that is not trusted, Reflection warns that it will not be able to reopen the file.

Reflection enforces trusted locations by default, so if you want to save sessions in directories that are not default trusted locations, you'll have to define these locations or disable the Trusted Locations feature. See Add Trusted Locations.
Setting up macro and API security
You can enable or disable the Reflection .NET API, determine whether Reflection legacy macros are supported, and determine which legacy API has preference for the GetObject() method used to retrieve API COM objects.
You can also specify whether to run restricted actions that are initiated through a macro or API call without elevating permissions.
Packaging Custom Files
After you customize session files or the Reflection workspace, you can bundle the customized session and settings files into a deployable companion installer package (.msi) to make it easier to deploy to your users. You can deploy companion installer packages separately or you can add them to a customized installation. You can also create and install packages at any time after the initial installation. See Package Sessions and Custom Settings Files.
Customizing the Installation
Create and deploy a transform to customize how Reflection is installed on user workstations. As defined by Microsoft, "a transform is a collection of changes applied to an installation. By applying a transform (*.mst) to a base installation package, the installer can add or replace data in the installation database."
For example, by deploying the transform with the Reflection base installation package, you can select which features to install.
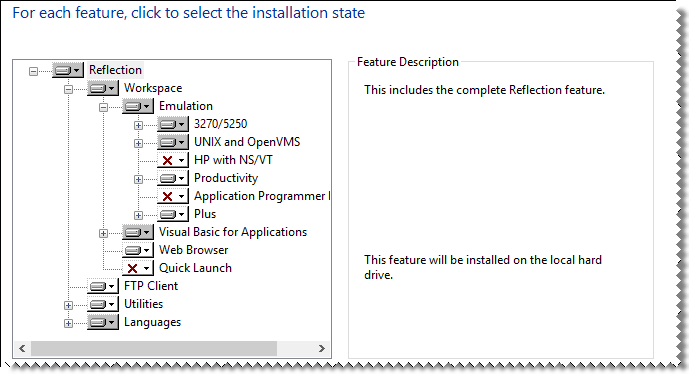
You can also specify the installation directory or the user data location, change the Remove or Add commands from the Windows Uninstall or change a program list, and change other default settings.
For more about creating transforms, see Modify the Installation