This chapter shows how to configure the user programs (clients and servers) to use firewalls and GateKeeper. The settings are configured through the client and server properties. See “Appendix GateKeeper properties” for information on how to set the properties.
If you specify the exportFirewallPath property, you do not need to add a firewall policy when creating a POA and therefore, you do not have to modify the source code.
This property defaults to false. Setting it to true is necessary for both the C++ client and C++ server when using a firewall with GateKeeper.
|
•
|
Java: Clients communicate to servers through the HTTP-tunneled or HTTPS-tunneled channel
|
Applets should set vbroker.orb.alwaysTunnel if the client will be performing HTTP tunneling. Applet clients must set the property vbroker.orb.gatekeeper.ior to get the GateKeeper's IOR using URL naming or using a stringified IOR. In addition, the applet clients must not set the vbroker.locator.ior property.
|
•
|
The vbroker.orb.proxyPassthru property sets the value of the ORB-level PROXY_MODE_POLICY property. If set to true, all objects using a proxy on the client will request pass-through connections. You can also set the PROXY_MODE_POLICY on specific objects so that only those particular objects request pass-through connections.
|
|
•
|
The vbroker.gatekeeper.enablePassthru property instructs GateKeeper to accept pass-through connections. This property is global to GateKeeper and affects GateKeeper's behavior only.
|
The vbroker.orb.proxyPassthru property tells the client to attempt to acquire pass-through connections from GateKeeper. GateKeeper, however, grants pass-through connections only if the vbroker.gatekeeper.enablePassthru property is set to true. See “Enabling pass-through connections” for other GateKeeper pass-through properties.
If the vbroker.gatekeeper.enablePassthru property is set to false, GateKeeper does not allow pass-through connections to be established and clients can only obtain normal (non-pass-through) connections to the server. GateKeeper then examines the messages exchanged between the client and server for routing and binding purposes. The connection will fail if GateKeeper cannot provide an SSL authentication for an SSL message.
The following properties specify the listener port of the client for servers to establish VisiBroker 3.x style callback connection. The listener type is set to Callback-IIOP to differentiate it from a normal IIOP listener.
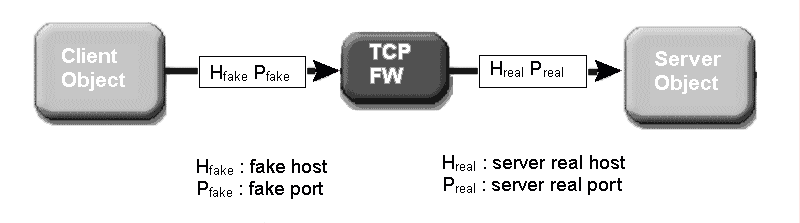
The above settings tell the server to listen to the real port while clients send messages to the fake port. The default value of the proxyPort property is 0 (zero), which means no proxy port is used.
|
Figure 9
|
The first property defines the firewall components found in the path named x. The second and fourth properties specify the types of the component named a and b, respectively. Both component types are defined as PROXY, which identifies GateKeeper as an IIOP proxy server to forward all IIOP requests. The third property defines the IOR of GateKeeper a using URL naming. The fifth property defines the IOR of GateKeeper b using a stringified IOR.
The first property defines the firewall components found in the path named y. The second property defines the type of component named c as TCP, which provides a predefined port to forward all IIOP, SSL and IIOP over HTTP messages on a router or other network device. The third property defines the fake host of the server. The remaining last three properties define the fake port for the following message types: IIOP, SSL and HTTP.
|
Figure 10
|