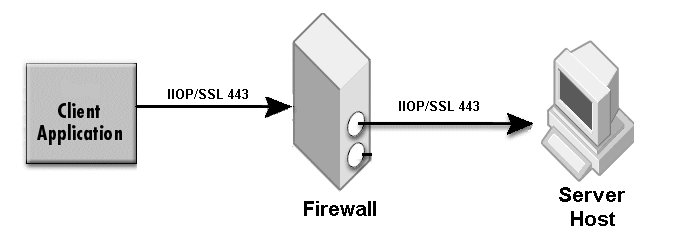
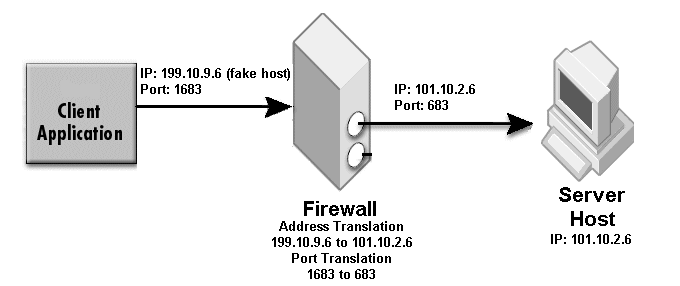
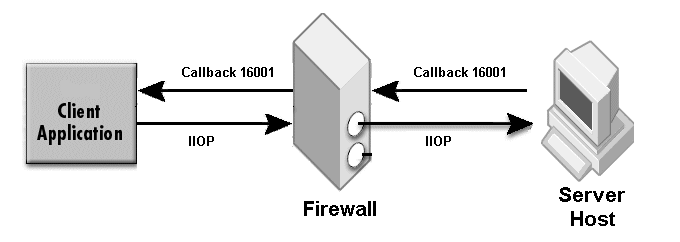
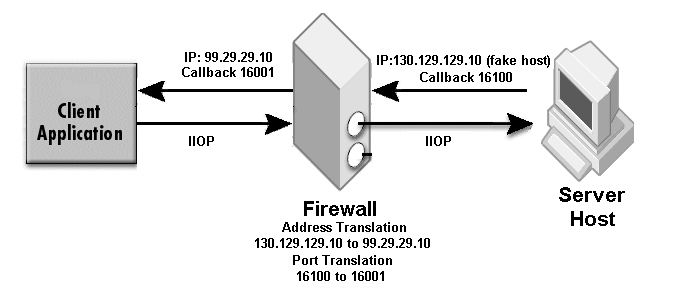
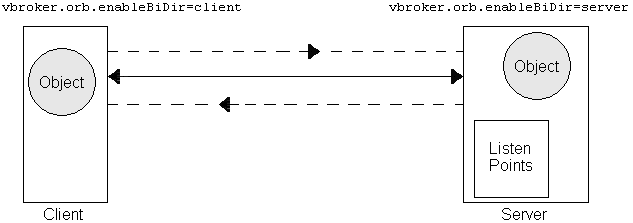
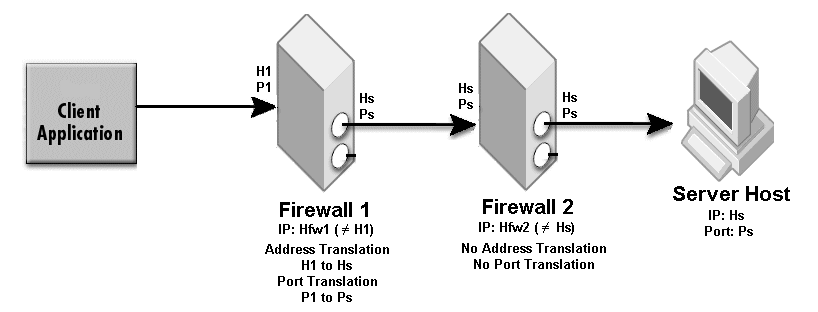
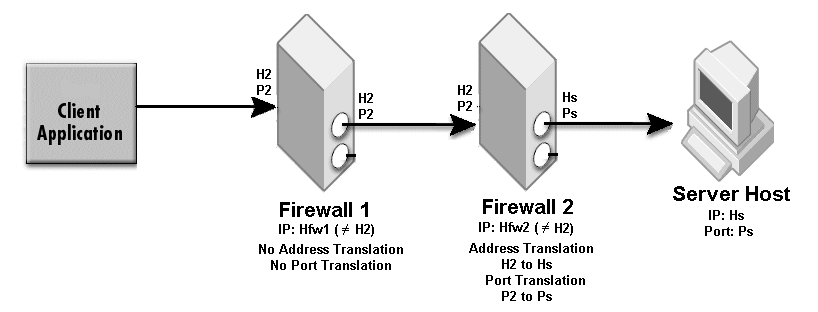
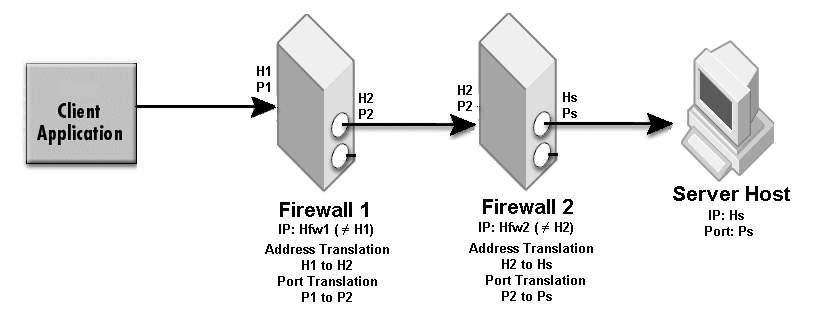
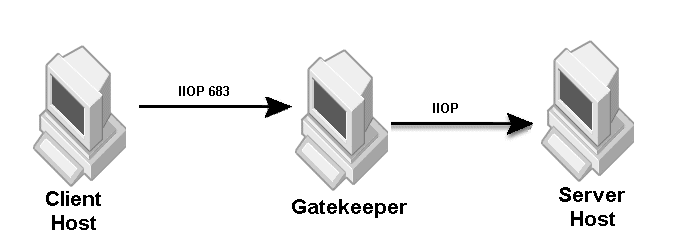
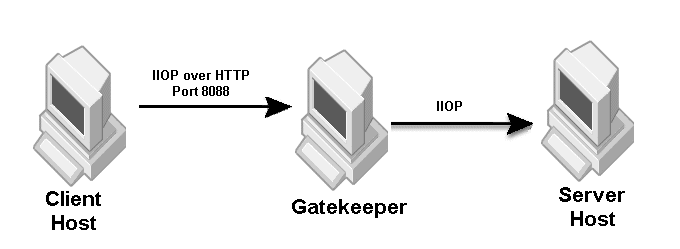
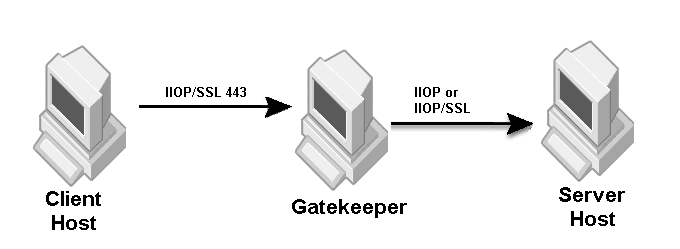
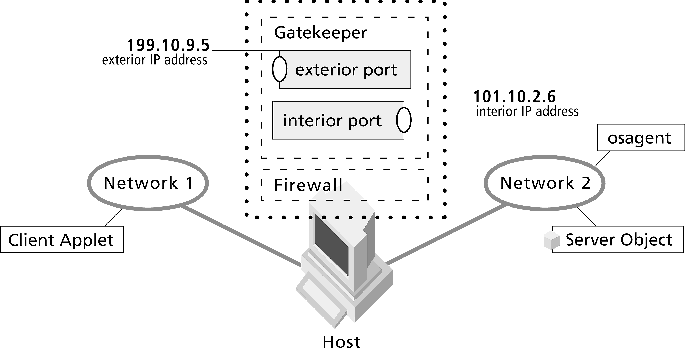
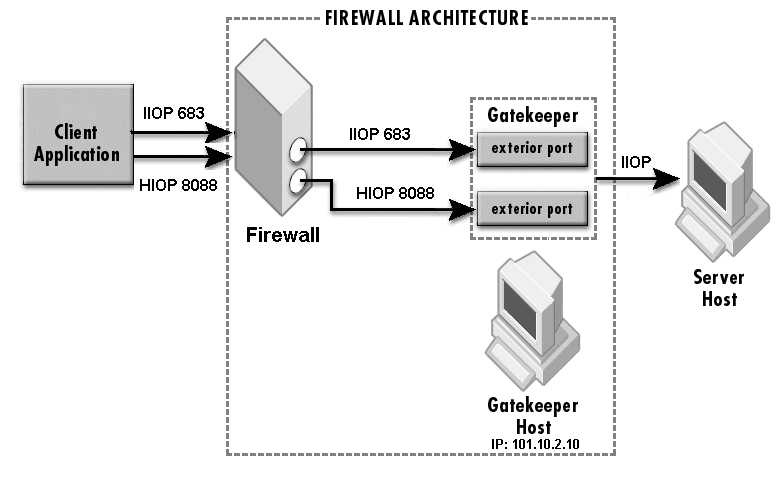
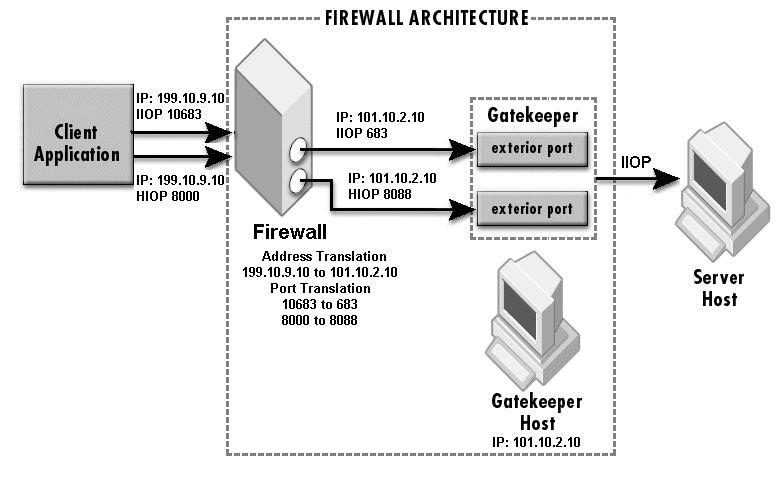
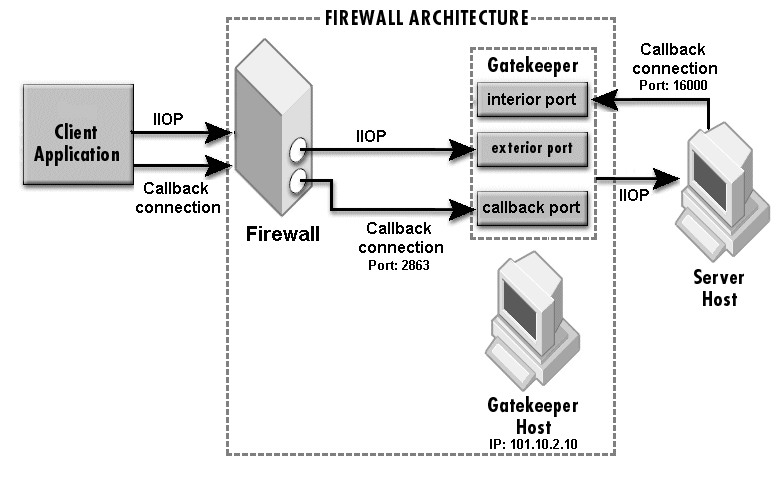
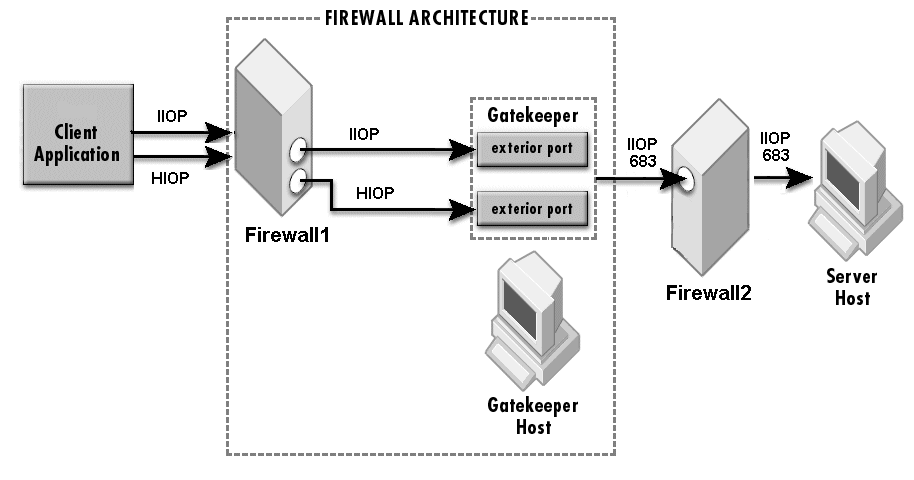
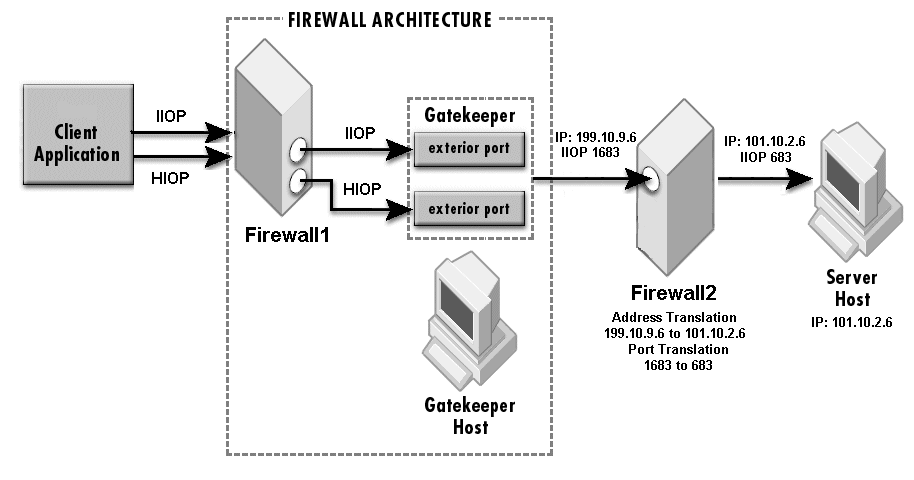
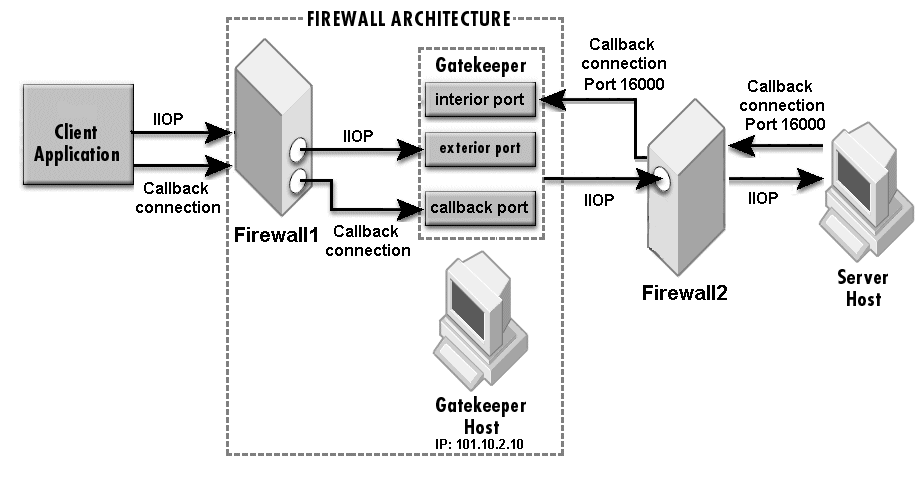
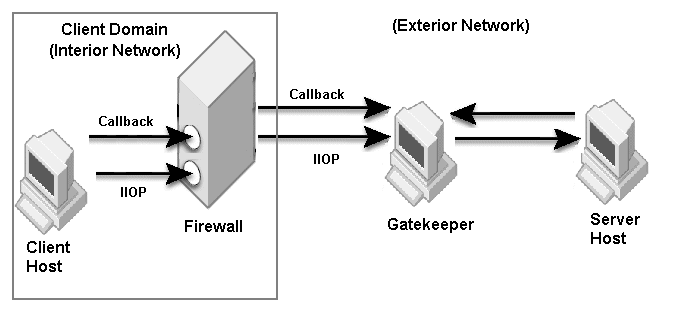
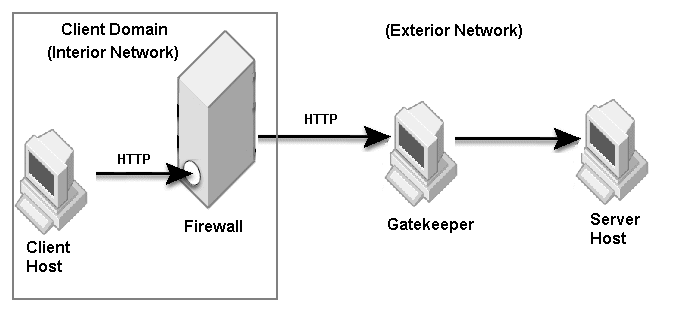
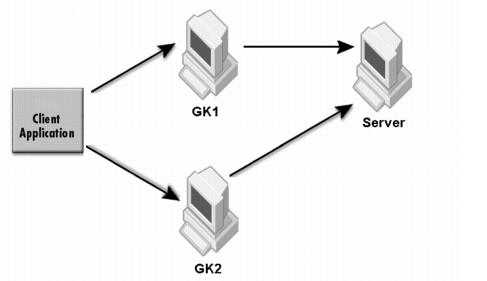
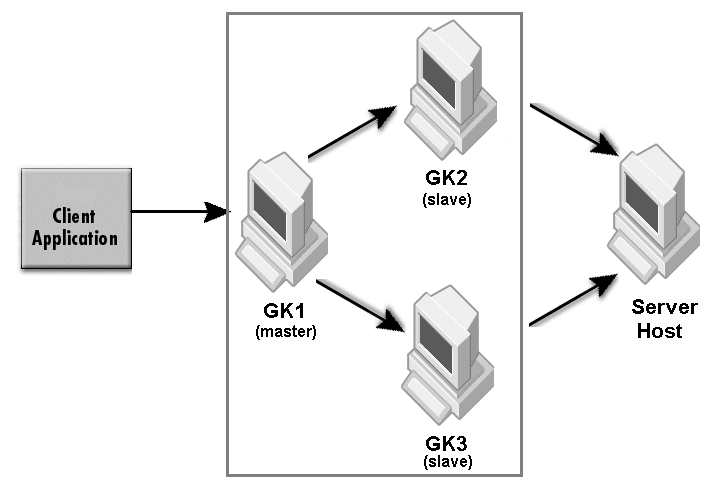
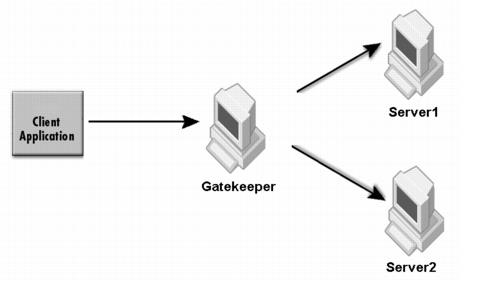
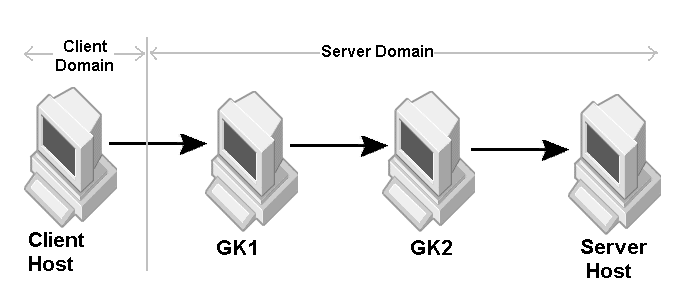
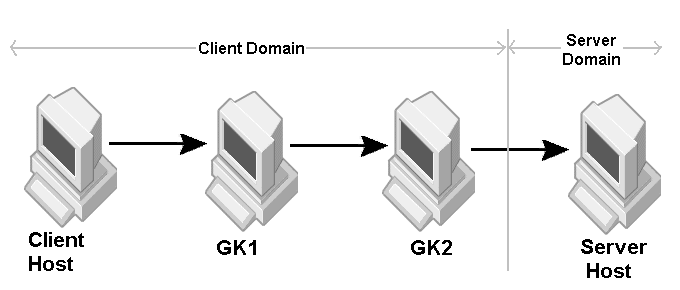
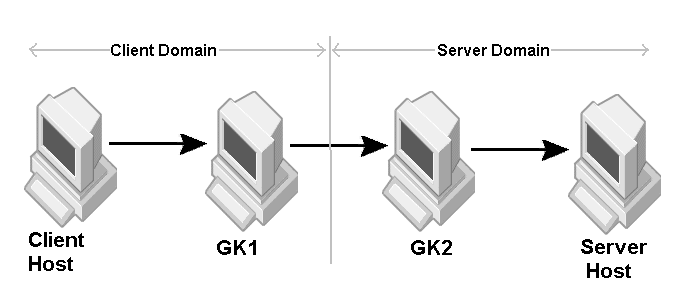
The sample properties assume that valid certificate information has already been loaded into both the secured client and the secured server as in the <install_dir>/examples/vbroker/security/bank_ssl example.
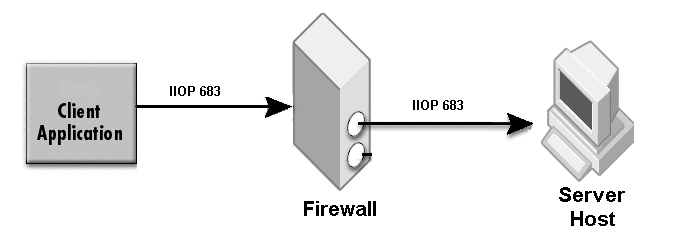
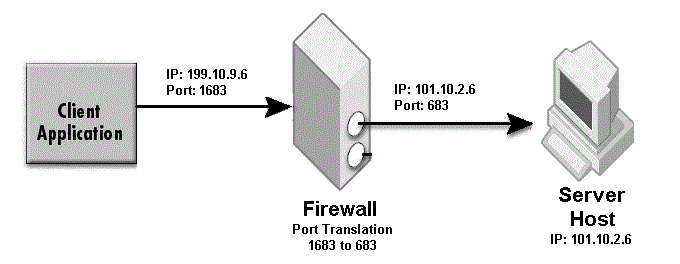
Specify a real port (for example, iiop_port=683) when there is no port translation, and 0 (for example, hiop_port=0) if the listener port is disabled.
Server's properties: Use only one of the following two methods.
Server's properties: Use only one of the following two methods.
Server's properties: Use only one of the following two methods.
The NAT information of Firewall2 does not need to be configured. The proxyHost and proxyPort specify only the first NAT fake host and fake port. For the firewall component and the firewall path, only specify the first NAT device.
If the client is an applet that wants to use IIOP instead of HTTP Tunneling, use the following configuration, do not specify the property <param name=”vbroker.orb.alwaysTunnel” value=”true”>:
vbroker.orb.gatekeeper.ior=http://gatekeeper:8088/gatekeeper.ior
Use the client and server settings in Scenario 2.4 and add the following to the client's properties:
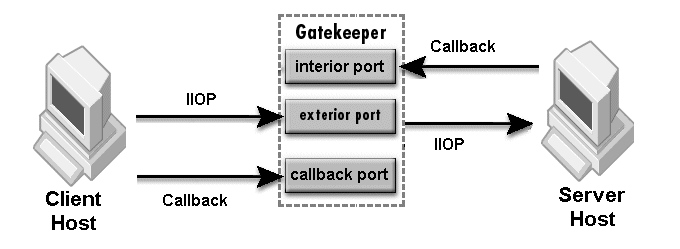
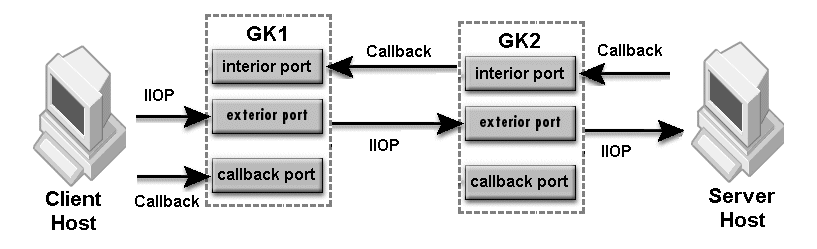
The interior port in-iiop is automatically enabled when callback is enabled. Only for secured callback, you need to add the SCM for in-ssl, ex-ssl and ex-hiops as required.
|
•
|
Allow routing of TCP packets on port range <in_min_port> to <in_max_port> from the client host to the GateKeeper. The firewall must not perform port translation on this range of ports.
Configure Firewall1 to allow routing of TCP packets in port range <in_min_port> to <in_max_port> from the client host to the GateKeeper. Configure Firewall2 to allow routing of TCP packets in port range <out_min_port> to <out_max_port> from the GateKeeper to the server host. The firewalls must not perform port translation on these ports.
where N must be less than the number of slave GateKeepers.
The value of <server IIOP port> must fall in the range of <out_min_port> and <out_max_port> of GK2. The range of <in_min_port> and <in_max_port> of GK2 must fall in the range of <out_min_port> and <out_max_port> of GK1.
|
•
|
Normal mode: Used when the firewalls can allow at least one port for the GIOP Proxy Server (such as GateKeeper). It is an automatic mode which can switch to HTTP tunneling if required.
|
|
•
|
Pass through mode: Used when the firewalls can allow a range of ports and packets exchanged between the client and server that is not to be interpreted by GateKeeper. In such a scenario, GateKeeper will act as a resource manager only. GateKeeper acts as a resource manager because it allocates IP ports to be used by the clients.
|
|
•
|
HTTP tunneling: Used when the firewalls allow only HTTP traffic. In such a scenario, the GIOP Proxy Server cannot be run in the firewall. Instead, an HTTP proxy server sits before GateKeeper. The client ORB has a built in mechanism to convert GIOP messages into HTTP messages which will be sent to the HTTP proxy server or the firewall. Then, the HTTP proxy server (or the applicable firewall) forwards the HTTP messages to GateKeeper. Additionally, GateKeeper converts the HTTP messages into GIOP messages and forwards it to the required target (such as server or another GateKeeper). This configuration is also useful in a client-side configuration when outgoing HTTP traffic is allowed by the firewall, but other types of TCP connections are not allowed.
|
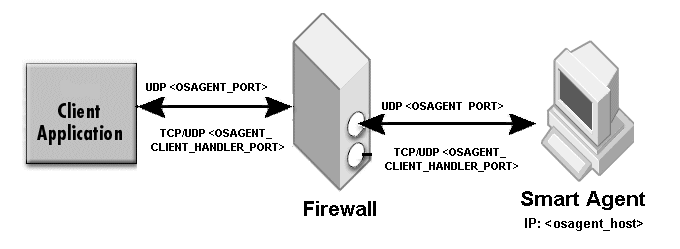
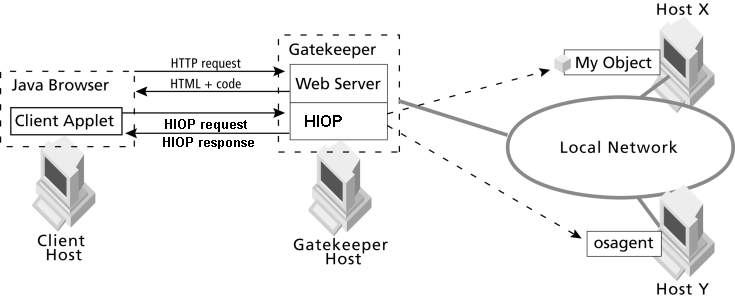
The VisiBroker-ORB requires the OSAGENT_PORT environment variable to be set to register and query CORBA objects using the Smart Agent. The default value of OSAGENT_PORT is 14000. By setting OSAGENT_PORT to an appropriate TCP/IP port, you can define a virtual domain. One can run any number of Smart Agents in a given subnet. Setting different OSAGENT_PORT values will create different domains, which means CORBA objects registered in one Smart Agent domain will not be visible to CORBA client querying from a different domain.
GateKeeper can use only one Smart Agent domain at a time. The Smart Agent domain is determined by setting the OSAGENT_PORT value or the vbroker.agent.port property. All servers accessible through GateKeeper should register to the same Smart Agent domain or to the Naming Service. It is recommended to run the Smart Agent on the same subnet as GateKeeper in the internal network.
|
1
|
OSAGENT_PORT (UDP type)
|
|
2
|
OSAGENT_CLIENT_HANDLER_PORT (UDP type)
|
|
3
|
OSAGENT_CLIENT_HANDLER_PORT (TCP type)
|
The OSAGENT_PORT used by the ORB applications is a UDP port. The only TCP type of port (also known as the OSAGENT_CLIENT_HANDLER_PORT) used by the Smart Agent is assigned to the Location Service. The OSAGENT_CLIENT_HANDLER_PORT of the UDP type is used by the Smart Agent itself. Please note that OSAGENT_CLIENT_HANDLER_PORT should be set only on those hosts where the Smart Agent is running.
The Smart Agent has some built-in fail-over and load-balancing capabilities. The domain of the Smart Agent is defined by the OSAGENT_PORT in use. If an ORB application (such as a server) is registered to one of the Smart Agents in a given domain (the Smart Agent domain), other ORB applications (such as a client program) can query the server objects in that domain from any of Smart Agents in the same domain. Thus, Smart Agents can query within a domain to locate a server object without making the client application aware of the process. Therefore, if one Smart Agent fails, the ORB application can find another Smart Agent in the same domain, register itself again, and proceed.
|
1
|
Open the OSAGENT_PORT and OSAGENT_CLIENT_HANDLER_PORT on the firewall. Certain firewalls may require that you set static forwarding routes so that the packets can reach the Smart Agent. All the intermediate firewalls between the applications should open these ports as well. Since firewalls may be on a multi-homed host, edit the localaddr (located, for example, in the <instal_dir>var/defaults/adm/properties/services/osagentfile folder) and set OSAGENT_LOCAL_ADDR_FILE to specify all the interfaces Smart Agent should bind to listen for request packets.
|
|
2
|
Set the Smart Agent IP address in the agentaddr file to allow the Smart Agent on one network to contact a Smart Agent on another network.
|
|
3
|
Set OSAGENT_PORT and OSAGENT_CLIENT_HANDLER_PORT on all hosts from where ORB applications may be launched. Please note that these ports should be the same as those opened on the firewalls.
|
If the Smart Agent fails, the ORB application is expected to switch to another Smart Agent in the same subnet. Because the Smart Agent OSAGENT_PORT is already fixed, the ORB application sends a UDP broadcast to locate another Smart Agent. If there is a firewall, the ORB application should have access to reach another host where the Smart Agent is running. The ORB application may not have the knowledge of the location of an alternative Smart Agent, so it can't do much. If the Smart Agent starts up again on the same host, the client may be able to contact it. Basically, it is important to understand that the Smart Agent uses a UDP broadcast-based technology. Some firewalls and routers may not forward UDP broadcasts and this is one of the reasons why the Smart Agent cannot be used across firewalls. Another Smart Agent, however, can be used if a Smart Agent in the same subnet fails.
In a server-side configuration, the server can be configured to specify the firewall component in its IOR which is identified by the client ORB and is used only when required. In such cases, the client fails over to bind to the server using GateKeeper only if a direct connection could not be established. Assuming that iiop_tp is the default server-engine used by the server, the following example shows a typical set of properties for a firewall configuration:
vbroker.se.exterior.proxyHost=142.186.142.21
vbroker.se.exterior.scm.ex-hiop.listener.proxyPort=32001
vbroker.se.exterior.scm.ex-hiop.listener.proxyPort=32001
|
•
|
|
•
|
|
•
|
GateKeeper can have more than one server connection manager (SCM) or listener for a given type of service. Usually, an SCM provides a specific type of service, such as IIOP, SSL, HIOP, HIOPS, and so forth. Each SCM is bound to a server engine, such as exterior or interior. To configure an SCM, you must assign a logical name (for example, myscm), and append this name to the following property:
|
•
|
web.xml - the deployment descriptor for gatekeeper to be deployed as a servlet.
|
|
•
|
Client.properties - the properties needed to set the bank_agent client to connect to the bank server via the GateKeeper embedded inside a web server as a servlet.
|
At the end of this section there are screen dumps of web.xml and Client.properties (see web.xml and Client.properties) which you can copy, paste, and save to designated files in specified directories.
|
1
|
Download a free copy of Tomcat web server from http://jakarta.apache.org/tomcat/, and follow the instructions to install it. A properly functioning installation can be verified by launching a web browser for http://localhost:8080.
|
|
2
|
Copy, paste, and save web.xml to <Tomcat root install>/webapps/gatekeeper_servlet/WEB-INF/web.xml. Create sub-directories as needed.
|
<?xml version=”1.0” encoding=”ISO-8859-1”?>
<!DOCTYPE web-app PUBLIC ”-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN” ”http://java.sun.com/dtd/web-app_2_3.dtd”>
<web-app>
<display-name>GateKeeper Servlet</display-name>
<description>GateKeeper as a servlet example</description>
<servlet>
<servlet-name>GateKeeperServlet</servlet-name>
<servlet-class>
com.inprise.vbroker.gatekeeper.servlet.Servlet
</servlet-class>
<load-on-startup />
<init-param>
<param-name>
vbroker.se.exterior.scm.ex-hiop.listener.path
</param-name>
<param-value>
/gatekeeper_servlet/servlet
</param-value>
</init-param>
<init-param>
<param-name>vbroker.agent.port</param-name>
<param-value>PUT YOUR OSAGENT PORT</param-value>
</init-param>
<!-- Some setups may not allow UDP broadcast to locate osagent
In that case, uncomment and set the following correctly
<init-param>
<param-name>vbroker.agent.address</param-name>
<param-value>
PUT IP OF THE MACHINE, ON WHICH OSAGENT IS RUNNING
</param-value>
</init-param>
-->
<init-param>
<param-name>vbroker.gatekeeper.referenceStore</param-name>
<param-value>
webapps/gatekeeper_servlet/gatekeeper.ior
</param-value>
</init-param>
<init-param>
<param-name>vbroker.se.exterior.scms</param-name>
<param-value>ex-iiop,ex-hiop</param-value>
</init-param>
<!-- If you want Visibroker log messages, uncomment this. Log messages will
go to the specified file below, relative to Tomcat root install dir
<init-param>
<param-name>vbroker.orb.debug</param-name>
<param-value>true</param-value>
</init-param>
<init-param>
<param-name>vbroker.orb.logLevel</param-name>
<param-value>7</param-value>
</init-param>
<init-param>
<param-name>vbroker.orb.warn</param-name>
<param-value>2</param-value>
</init-param>
<init-param>
<param-name>vbroker.orb.logger.output</param-name>
<param-value>webapps/gatekeeper_servlet/log.txt</param-value>
</init-param>
-->
<init-param>
<param-name>
vbroker.se.exterior.scm.ex-iiop.listener.type
</param-name>
<param-value>Disabled-IIOP</param-value>
</init-param>
<init-param>
<param-name>
vbroker.se.exterior.scm.ex-hiop.listener.port
</param-name>
<param-value>8080</param-value>
</init-param>
<init-param>
<param-name>
vbroker.se.exterior.scm.ex-iiop.listener.port
</param-name>
<param-value>0</param-value>
</init-param>
</servlet>
<servlet-mapping>
<servlet-name>GateKeeperServlet</servlet-name>
<url-pattern>/servlet</url-pattern>
</servlet-mapping>
</web-app>
<!DOCTYPE web-app PUBLIC ”-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN” ”http://java.sun.com/dtd/web-app_2_3.dtd”>
<web-app>
<display-name>GateKeeper Servlet</display-name>
<description>GateKeeper as a servlet example</description>
<servlet>
<servlet-name>GateKeeperServlet</servlet-name>
<servlet-class>
com.inprise.vbroker.gatekeeper.servlet.Servlet
</servlet-class>
<load-on-startup />
<init-param>
<param-name>
vbroker.se.exterior.scm.ex-hiop.listener.path
</param-name>
<param-value>
/gatekeeper_servlet/servlet
</param-value>
</init-param>
<init-param>
<param-name>vbroker.agent.port</param-name>
<param-value>PUT YOUR OSAGENT PORT</param-value>
</init-param>
<!-- Some setups may not allow UDP broadcast to locate osagent
In that case, uncomment and set the following correctly
<init-param>
<param-name>vbroker.agent.address</param-name>
<param-value>
PUT IP OF THE MACHINE, ON WHICH OSAGENT IS RUNNING
</param-value>
</init-param>
-->
<init-param>
<param-name>vbroker.gatekeeper.referenceStore</param-name>
<param-value>
webapps/gatekeeper_servlet/gatekeeper.ior
</param-value>
</init-param>
<init-param>
<param-name>vbroker.se.exterior.scms</param-name>
<param-value>ex-iiop,ex-hiop</param-value>
</init-param>
<!-- If you want Visibroker log messages, uncomment this. Log messages will
go to the specified file below, relative to Tomcat root install dir
<init-param>
<param-name>vbroker.orb.debug</param-name>
<param-value>true</param-value>
</init-param>
<init-param>
<param-name>vbroker.orb.logLevel</param-name>
<param-value>7</param-value>
</init-param>
<init-param>
<param-name>vbroker.orb.warn</param-name>
<param-value>2</param-value>
</init-param>
<init-param>
<param-name>vbroker.orb.logger.output</param-name>
<param-value>webapps/gatekeeper_servlet/log.txt</param-value>
</init-param>
-->
<init-param>
<param-name>
vbroker.se.exterior.scm.ex-iiop.listener.type
</param-name>
<param-value>Disabled-IIOP</param-value>
</init-param>
<init-param>
<param-name>
vbroker.se.exterior.scm.ex-hiop.listener.port
</param-name>
<param-value>8080</param-value>
</init-param>
<init-param>
<param-name>
vbroker.se.exterior.scm.ex-iiop.listener.port
</param-name>
<param-value>0</param-value>
</init-param>
</servlet>
<servlet-mapping>
<servlet-name>GateKeeperServlet</servlet-name>
<url-pattern>/servlet</url-pattern>
</servlet-mapping>
</web-app>