Contracts Assigned to a SAML 2.0 Service Provider
During federation, when a service provider initiates an authentication request, contract information might not be available. If the contract information is not available, Identity Server executes a default contract for validating the user. You can use the step-up authentication to assign a default contract for service providers in such scenarios.
The following scenario explains the execution of contracts assigned to a SAML 2.0 service provider:
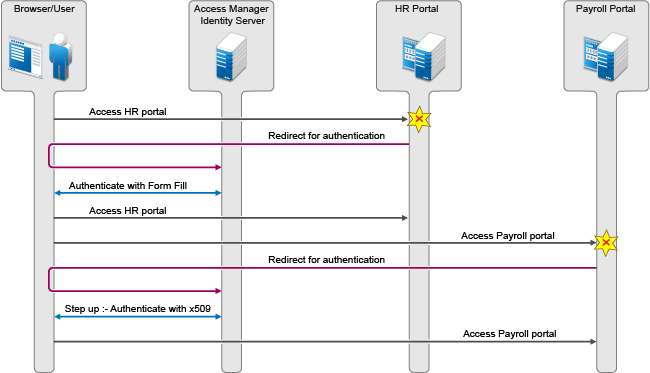
Two web applications, Payroll Portal and HR Portal, protected through different service providers, use Access Manager Identity Server as an identity provider. A user wants to use the name/password form contract to access HR Portal and wants to use the higher level contract X509 for Payroll Portal. Identity Server provides an ability to execute the appropriate contract that has been assigned to the service provider instead of executing the default contract.
Figure 5-13 Step-up authentication example with two applications
Perform the following steps to assign a specific contract to a service provider:
-
Click Devices > Identity Servers > Edit > SAML 2.0 > [service provider].
-
Go to Options > Step Up Authentication contracts and select contracts from Available contracts.
The following table lists the behavior of a service provider request:
Service Provider Request
Result
(Identity Server response if the user is not authenticated)
Service provider request has no contract information to be executed at Identity Server
1. Identity Server has no contracts set for this service provider as in Step 2.
Execute default contract for validating the user and default contract name is sent in the response.
2. Identity Server has contract C1 set for this service provider as in Step 2.
C1 is executed for validating the user and C1 is sent in the response.
Service provider requests execution of contract C1 at Identity Server
1. Identity Server has no contracts set for this service provider as in Step 2.
C1 is executed for validating the user and C1 is sent in the response.
2. Identity Server has contract C1 set for this service provider as in Step 2.
C1 is executed for validating the user and C1 is sent in the response.
3. Identity Server has contract C2 set for this service provider. C2 has trust level check disabled.
C2 is executed for validating the user and C2 is sent in the response.
NOTE:C1 is not considered to be executed in this case.
4. Identity Server has contract C2 set for this service provider. C2 has trust level check enabled.
If trust level of C2 >= trust level of C1, then C2 is executed and C2 is sent in the response.
If trust level of C2 < trust level of C1, then C1 is executed and C1 is sent in the response.
If C1 is not available at Identity Server, then C2 is executed and C2 is sent in the response.
NOTE:When using the service provider (SP) initiated login with a SAML 2.0 SP federation, the SP configuration can impact the selection of the Access Manager contract for authentication depending on the values sent in the SAML authentication request. To make it work, define your Access Manager contract URI to match with the request sent by the SP.
For more information, see Allowable Class
in Configuring Authentication Contracts.