A.3 Sharing Roles
When two Identity Servers are configured to trust each other, one as an identity provider and another as a service provider, they can be configured so that roles are shared. The following instructions are applicable for when both identity provider and service provider are Access Manager Identity Servers. When using a third-party identity or service provider, you need to modify the instructions.
Figure A-3 illustrates a configuration where Identity Server of Site A acts as an identity provider for Site B. When you configure Identity Servers correctly, Access Gateway can use the roles defined for the users of Site A in its policies.
Figure A-3 Two Federated Identity Servers
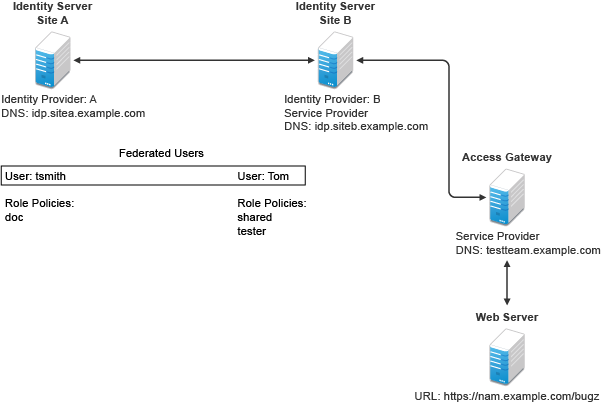
The key to sharing roles is to set up the configuration so that the SAML assertion that the identity provider (Site A) sends to the service provider (Site B) contains the roles that the user has been assigned. Site B evaluates the roles and assigns them to the federated users at Site B. Access Gateway can use these roles in its policy evaluations, and grant or deny access based on the assigned roles.
For example, when user tsmith authenticates to Site A, tsmith is assigned the role of doc. Tom, a user at Site B, is federated with the tsmith user. The doc role is shared with Site B, and Site B contains a policy that assigns users with the shared doc role to the tester role. Access Gateway is configured with an Authorization policy that grants access to a resource when the requester is assigned the tester role. However, Tom does not have the qualifications at Site B to be assigned the tester role.
In this scenario, when Tom requests access to the protected resource at Site B, a login page with a federated link to Site A is displayed. If Tom selects to log in to Site A, Site A assigns him to the doc role. The doc role is sent with tsmith’s authentication credentials to Site B. Site B evaluates the credentials and assigns Tom to the tester role because the following conditions are met:
-
Tom is federated with tsmith.
-
tsmith was assigned the doc role.
-
The shared role and tester policies on Site B qualify the user to be assigned the tester role.
When Access Gateway evaluates the credentials of Tom, Tom is granted access to the protected resource because he now has the tester role.
This section describes how to set up such a configuration. It assumes that the following have already been done:
-
The trusted relationship between the identity provider and service provider is set up. For configuration instructions, see Establishing Trust between Providers.
-
The following policies have been created: the doc role policy at Site A, the tester role policy at Site B, and the Authorization policy (that uses the tester role) for Access Gateway. For information about creating a Role policy, see Role Policies, and for the Authorization policy, see Assigning an Authorization Policy to a Protected Resource. The following instructions explain how to set up the shared policy.
This section explains how to configure Site A and Site B so that Site A shares its roles with Site B.