Configuring Policies to Process Received Roles
Create a shared Role policy for each role sent to the service provider. This policy defines how the role must be processed.
For each role that is sent from Site A, you need to create a Role policy that specifies the role that must be activated on Site B. For example, suppose the tsmith user from Site A is assigned the doc role at authentication. You can create a Role policy on Site B that assigns the tester role to anyone with the doc role from Site A.
-
Log in to Administration Console for Site B.
-
Click Policies > Policies > New.
-
Specify a name for the policy, select Identity Server: Roles for the type, then click OK.
-
In the Condition Group 1 section, click New, then select Roles from Identity Provider.
-
(Conditional) If you have federated with more than one identity provider, select the provider. If you have federated with only one identity provider, the provider is selected for you.
In this example, you have federated with only the identity provider at Site A, and it is selected for you.
-
For the value, select Data Entry Field, then specify the name of a role that is assigned by Site A, for example doc.
If you leave Mode set to Case Sensitive, ensure that you specify the case correctly.
-
In the Actions section, specify the role to activate on Site B for the role received from Site A.
Your policy must look similar to the following:
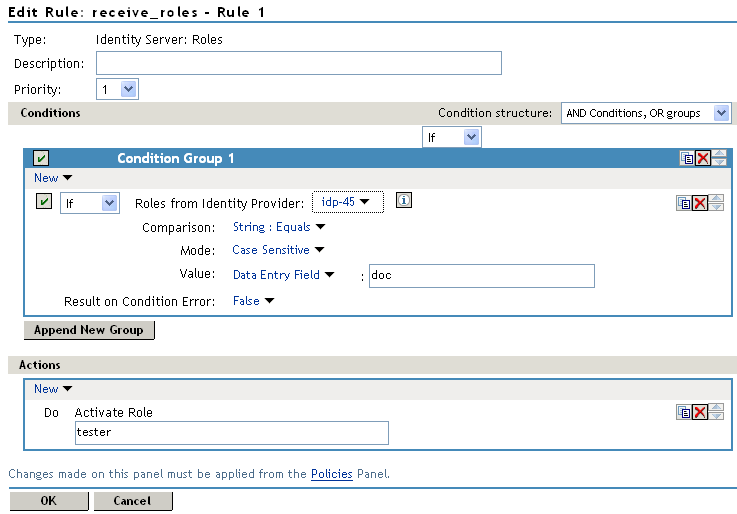
-
Click OK > OK, then click Apply Changes.
-
To enable the role for Identity Server, click Identity Servers > Edit > Roles.
-
Select the role, then click Enable.
-
(Optional) Repeat Step 2 through Step 10 for other roles assigned at Site A.
If you have other Role policies at Site A, you need to set up Role policies at Site B to have the roles activated. For example, if Site A had a Tester Role policy and you wanted users assigned to the Tester Role policy to also be assigned to the Tester Role policy at Site B, you could create a separate policy for this activation, or you could add an Or condition group with a value field of tester to the policy in Step 7. The policy would assign federated users who belonged to the doc or tester roles at Site A, to the tester role at Site B.
-
To test role sharing:
-
Enter the URL of a protected resource that requires a role for access. For the policy above, it would be a resource requiring the tester role.
-
Click the federated link to Site A.
-
Log in with the credentials of a user who is assigned the doc role.
You are granted access to the resource. If you are denied access, continue with Verifying the Configuration to discover the problem.
-