1.2 Access Manager Versus Access Manager Appliance
Both Access Manager and Access Manager Appliance deployment models use a common code base. However, a few differences exist between both models.
The following table provides details to help you determine which solution fits your business:
Table 1-1 Access Manager Versus Access Manager Appliance
|
Feature |
Access Manager Appliance |
Access Manager |
|---|---|---|
|
Virtualization Support |
Supported on the virtual servers based on SUSE Linux Enterprise Server (SLES) 12 SP5 with 64-bit operating system x86-64 hardware. |
Supported on the virtual servers based on SLES 12 SP5 or SLES 15 SP2 with 64-bit operating system x86-64 hardware. |
|
Host Operating System |
A soft appliance that includes a pre-installed and configured SUSE Linux operating system. NetIQ maintains both the operating system and Access Manager patches through the patch update channel. |
Operating System choice is more flexible. Install Administration Console, Identity Server, and Access Gateway on a supported operating system (SUSE or Red Hat). The patch update channel maintains patches for Access Manager. You must purchase, install, and maintain the underlying operating system. |
|
Component Installation Flexibility |
Access Manager components such as Administration Console, Identity Server, and Access Gateway cannot be selectively installed or uninstalled. |
Each Access Manager component such as Administration Console, Identity Server, and Access Gateway are installed on independent host servers. Although the ability to install multiple components on a single host server exists, it is very limited and not recommended. A typical highly available deployment requires 6-8 or more virtual or physical servers (2 Administration Consoles, 2 Identity Servers, 2 Access Gateways). |
|
Administration Console Access |
Administration Console is installed on Access Manager Appliance along with all other components. If you use two network interfaces, access to Administration Console can be limited to the private IP network bound to the internal network. The public interface is bound to an externally accessible network. |
Administration Console can be installed on an independent host inside your private network but can still securely manage Access Manager components that reside in your DMZ or external network. |
|
Scalability and Performance |
Scales vertically on adding CPU and memory resources to each node. |
Scales both vertically and horizontally on adding nodes.See NetIQ Access Manager Performance and Sizing Guidelines. |
|
High Availability |
Supported |
Supported |
|
Upgrade |
You can upgrade from one version of Access Manager Appliance to another version. However, upgrading from Access Manager to Access Manager Appliance is not supported. |
You can upgrade from one version of Access Manager to another version. However, upgrading from Access Manager Appliance to Access Manager is not supported. |
|
Disaster Recovery |
You can use the backup and restore process to save your Access Manager Appliance configuration. |
You can use the backup and restore process to save your Access Manager configuration. |
|
Time to Value |
Automates several configuration steps to quickly set up the system. |
Requires more time to install and configure as the components are on different servers. |
|
User Input required during installation |
Access Manager Appliance is a software appliance that takes only a few basic parameters as input. Several options assume default values. |
More flexibility during installation in terms of selectable parameters. |
|
Installation and Configuration Phases |
The installer takes care of configuration for each component. The system is ready for use after it is installed. |
Separate installation and configuration phases for each component. After installation, each Access Manager component is separately configured. |
|
Mode of release |
Access Manager Appliance is released as a software appliance. |
Access Manager is delivered in the form of multiple operating system- specific binaries. |
|
NIC Bonding |
IP address configuration is done through Administration Console. So, NIC bonding is not supported. |
NIC bonding can be done through the operating system and Access Manager in turn uses this configuration. |
|
Networking: Port Details |
Administration Console and Identity Server are accelerated and protected by Access Gateways. Only HTTPS port 443 is required to access Access Manager Appliance through a firewall. |
Multiple ports need to be opened for deployment. |
|
Networking: General |
Administration Console must be in DMZ, but access can be restricted through the private interface. |
As Administration Console is a separate device, access can be restricted or Administration Console can be placed in an internal network. |
|
Certificate Management |
Certificate management is simplified. All certificates and key stores are stored at one place making replacing or renewing certificates easier. |
Changes are required at multiple places to replace or renew certificates. |
|
SAML Assertion Signing |
Same certificate is used for all communication. (signing, encryption, and transport). |
As there are multiple key stores, you can configure different certificates for the communication. |
|
Associating different signing certificates for each service provider |
Not supported |
A unique signing certificate can be assigned to each service provider. In environments with a large number of trust relationships, this feature eases the process of replacing expiring certificates. |
|
Associating different certificates to Identity Server |
Not applicable because Identity Server is accelerated by Access Gateway. |
Supported. You can place Identity Server behind Access Gateway or place it separately in DMZ. |
|
Ready-made Access Manager |
The following configuration is automatically done after Access Manager Appliance installation:
As the inter-component configuration is automated, the administrator only needs to add the existing user store and accelerate, protect, sso-enable existing web applications. |
Each component requires manual configuration and setup before web applications can be federation enabled, accelerated, and protected. |
|
Updating Kernel with Security Patches |
Supports installation of latest SLES operating system security patches. |
You are fully responsible for all operating system maintenance including patching. |
|
Clustering |
For additional capacity and for failover, cluster a group of Access Manager Appliances and configure them to act as a single server. You can cluster any number of Identity Servers and Access Gateways, and up to three of Administration Consoles. The first three nodes of Access Manager Appliance contain Administration Console, Identity Server, and Access Gateway. Fourth installation onwards, the node does not contain Administration Console. A typical Access Manager Appliance deployment in a cluster is described in Figure 1-3. |
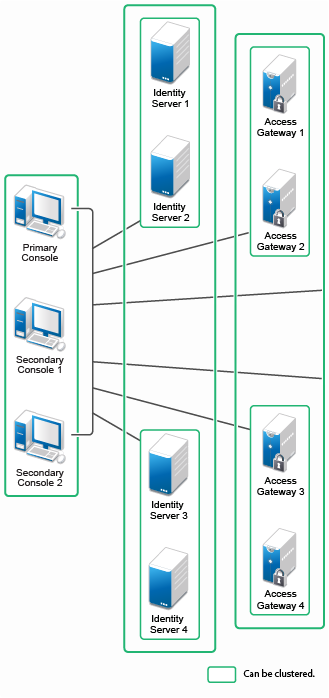
For additional capacity and for failover, cluster a group of Identity Servers and configure them to act as a single server. You can create a cluster of Access Gateways and configure them to act as a single server. Fault tolerance can be achieved by installing up to two secondary consoles. To deploy the existing solution in a cluster mode, at least 6 systems are required. A typical Access Manager deployment in a cluster is described in Figure 1-4. |
Figure 1-3 Access Manager Appliance Cluster
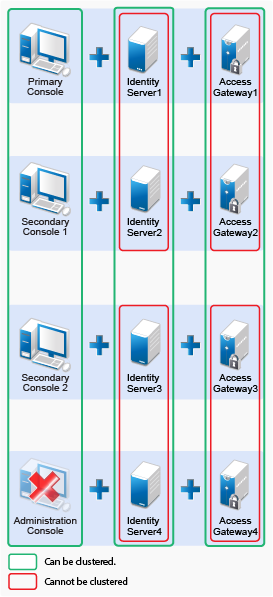
Figure 1-4 Access Manager Cluster
General Guidelines
-
Adding an Access Gateway Service or Access Gateway Appliance to an Access Manager Appliance cluster is not possible.
-
Deploying Administration Console in a DMZ network limits access from a private interface or network.
-
It is recommended to not change the primary IP Address of Access Manager. This might result in corruption of the configuration store. However, you can modify the listening IP address of reverse proxy or the outbound IP address used to communicate with the web server. For more information, see Changing the IP Address of Access Manager Devices in the NetIQ Access Manager 5.0 Administration Guide.
-
You cannot have different certificates for signing and encryption in a federation setup.
-
You cannot install any monitoring software to monitor statistics in Access Manager Appliance.
-
Clustering between Access Manager and Access Manager Appliance is not supported.
When to Choose Access Manager Appliance
The following are common usage patterns when you can deploy Access Manager Appliance:
-
You are interested in deploying Access Manager, but need fewer servers.
-
You are still on iChain because you prefer a single-server solution.
-
You are new to Access Manager and are interested in providing secure access, but want to avoid the long process of designing, installing, and configuring a full-fledged web access management solution.
-
You do not have a web access management or federation solution and you are considering moving to a web access management solution.
-
You represent a division of a large organization (for example, the Marketing division) that wants secure single sign-on access to a SaaS application such as Salesforce.
-
You want to reduce server hardware and management costs by consolidating Access Manager services on fewer servers.
-
You want to quickly set up a test environment to verify changes.
-
You want to quickly set up and evaluate Access Manager.