1.8.3 Sample Configurations
Access Gateway and Identity Server in DMZ
First Firewall
If you place a firewall between browsers and Access Gateway and Identity Server, you need to open ports so that the browsers can communicate with Access Gateway and Identity Server and Identity Server can communicate with other identity providers.
See, Figure 1-10
Table 1-11 Ports to Open in the First Firewall
|
Port |
Purpose |
|---|---|
|
TCP 80 |
For HTTP communication. |
|
TCP 443 |
For HTTPS communication. |
|
Any TCP port assigned to a reverse proxy or tunnel. |
|
|
TCP 8080 |
For HTTP communication with Identity Server. For information about redirecting Identity Server to use port 80, see Translating Identity Server Configuration Port. |
|
TCP 8443 |
For HTTPS communication with Identity Server. For information about redirecting Identity Server to use port 443, see Translating Identity Server Configuration Port. |
|
TCP 8445 |
For HTTP Identity Provider introductions. If you do not enable Identity Provider introductions, you do not need to open this port. |
|
TCP 8446 |
For HTTPS Identity Provider introductions. If you do not enable Identity Provider introductions, you do not need to open this port. |
Second Firewall
The second firewall separates web servers, LDAP servers, and Administration Console from Identity Server and Access Gateway. You need the following ports opened in the second firewall:
Table 1-12 Ports to Open in the Second Firewall
|
Port |
Purpose |
|---|---|
|
TCP 80 |
For HTTP communication with web servers. |
|
TCP 443 |
For HTTPS communication with web servers. |
|
Any TCP connect port assigned to a web server or to a tunnel. |
|
|
TCP 1443 |
For communication from Administration Console to the devices. |
|
TCP 8444 |
For communication from the devices to Administration Console. |
|
TCP 1290 |
For communication from the devices to the Syslog server installed on Administration Console. If you do not enable auditing, you do not need to open this port. |
|
TCP 524 |
For NCP certificate management in NPKI. The port needs to be opened so that both the device and Administration Console can use the port. |
|
TCP 636 |
For secure LDAP communication of configuration information. |
A Firewall Separating Access Manager Components from the LDAP Servers
You can configure Access Manager components so that your Administration Console is on the same side of the firewall as your Access Manager components and have a firewall between them and the LDAP servers.
Figure 1-11 A Firewall Separating Administration Console and the LDAP Server
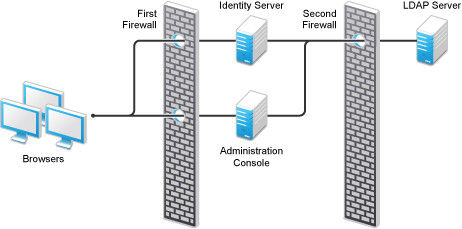
In this configuration, you need to open the following ports in the second firewall for Administration Console and Identity Server:
Table 1-13 Ports to Open in the Second Firewall
|
Ports |
Purpose |
|---|---|
|
TCP 636 |
For secure LDAP communication. This is used by Identity Server and Administration Console. |
|
TCP 524 |
For configuring eDirectory as a new User Store. NCP is used to enable SecretStore by adding a SAML authentication method and storing a public key for Administration Console. During day-to-day operations, this port is not used. If your LDAP server is Active Directory, this port does not need to be opened. |