Sample Policies Based on Organizational Rules
Suppose that the company LDAP directory has the following organization:
- ou=sales,o=acme
- ou=dev,o=acme
- ou=hr,o=acme
Suppose that this company has the following configuration and requirements:
-
Under each branch of the tree, the system administrator has created users who work in these departments.
-
Each department has its own web resources and other departments must be denied access to these resources.
With this type of configuration, you can use the LDAP context condition to create authorization policies or you can create role policies that are used in conjunction with authorization policies.
LDAP Context Policies
Create a policy that allows or denies access based on the LDAP context of the user’s DN. You can use the LDAP context of the user DN to group users based on their departments and then grant access based on the context match. You need to create protected resources for the web resources of the department, create a policy for each protected resource, and assign a policy to the protected resources.
Perform the following steps to configure a policy for the sales department:
-
Click Policies > Policies > New, specify a name for the policy, select Access Gateway: Authorization as the type, and click OK.
-
For Condition Group 1, click New, then select Credential Profile.
-
Specify the following details:
LDAP Credentials: Select LDAP User DN.
If/If Not: Select If Not.
Comparison: Select Contains Substring.
Mode: Select Case Insensitive.
Value: Select Data Entry Field and specify ou=sales,o=acme.
Result on Condition Error: Select True.
-
In the Actions section, select Deny.
Your policy must look similar to the following:
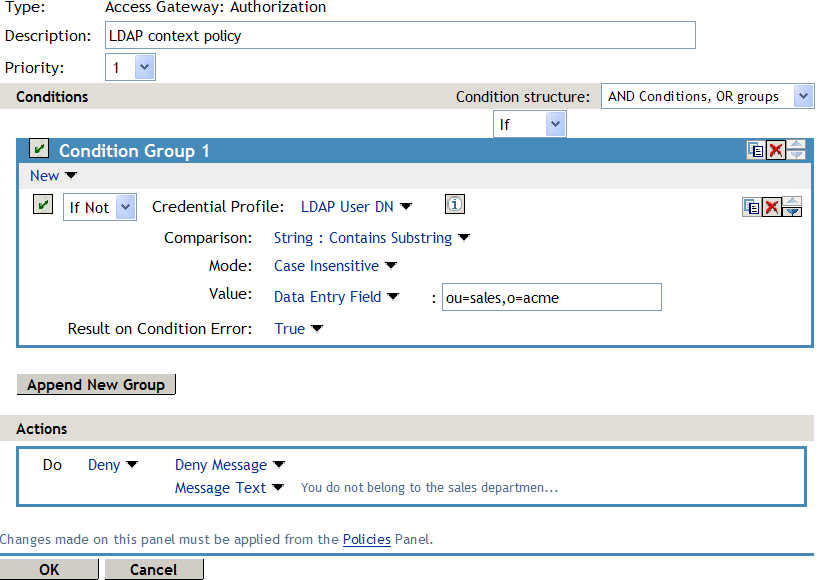
The following are the results of this configuration:
-
When a user does not belong to the sales department, the user is denied access.
-
When a user belongs to the sales department, the user is granted access.
-
When an error occurs evaluating the conditions in the rule, the user is denied access.
-
-
Assign the policy to the protected web resources of the sales department. See Assigning an Authorization Policy to a Protected Resource.
-
Repeat the steps for other two departments and specify the appropriate department in Value.
Role Policies with Authorization Policies
Because of the company’s organization, you need to create three role policies for the following users:
-
Sales users
-
Development users
-
Human resource users.
You can then use these roles as conditions in authorization policies to allow and deny access. The first time you use roles in an authorization policy, there is extra setup because you must create the role policies. However, after the role policies are created, you can use them in multiple authorization policies.
For information about how to create the Sales role, see Creating a Role by Using the Location of the User Objects.
You need to decide on the type of Authorization policy you want to create. For example, you can create a Deny policy that denies access to everyone who does not match the condition (in this case, the Sales role). Alternatively, you can create a two-rule policy that allows access to everyone that matches the condition.
The first rule grants access to everyone who has the Sales role, and the second rule denies access to everyone who did not match the conditions of the first rule. (Other methods are also possible.) Because the proposed Deny policy is very similar to the LDAP Context Policies example, the following procedures explain how to create the two-rule policy:
-
Click Policies > Policies > New.
-
Specify a name for the policy, select Access Gateway: Authorization as the type, then click OK.
-
(Optional) Provide a description for the rule.
-
In Condition Group 1, click New, and select Roles.
-
Specify the following details:
If/If Not: Select If.
Roles: Select [Current].
Comparison: Select String: Equals.
Mode: Select Case Insensitive
Value: Select Roles, then select Sales.
Result on Condition Error: Select False.
-
Under Actions, select Permit, then click OK.
These steps create the Permit rule and set up the condition so that the following occurs:
-
When the user does not match the condition because the user does not belong to the Sales role, the policy engine moves to the next rule in the policy.
-
When the user does match the condition because the user belongs to the Sales role, the user is granted access.
-
If an error occurs when evaluating the condition of the policy, the user does not match the condition and the policy engine moves to the next rule in the policy.
-
-
In the Rule List, click New.
This second rule is for denying access to everyone who does not match the condition in Rule 1. Processing of the policy stops when a user matches a rule; therefore all users who match Rule 1 are granted access and the policy engine does not evaluate the second rule.
-
Set the Priority to be 2 or greater.
You want the Permit rule to be processed first, so it must have a priority of 1. The Deny rule needs to be processed last, so it needs a lower priority than the Permit rule.
-
Leave the Condition Group 1 empty.
The Conditions section is left empty so that everyone who does not match the conditions of the Permit rule is denied access to the resource.
-
In the Actions section, select Deny and either accept the default action or select one of the other actions.
-
Click OK twice.
-
Click Apply Changes on the Policies page.
-
Assign the policy to the protected web resources of the sales department. See Assigning an Authorization Policy to a Protected Resource.