Selecting Conditions
Create a role by selecting the appropriate conditions that qualify a user to be assigned to a role.
Authenticating IDP Condition
The Authenticating IDP condition allows you to assign a role based on the identity provider that authenticated the current user. To use this condition, you must have set up a trusted relationship with more than one identity provider. See Section 2.8.3, Managing Trusted Providers.
The most common way to use this condition is when you have a service provider that has been configured to trust two identity providers and you want to assign a role based on which identity provider authenticated the user. To configure such a policy:
-
Set the Authenticating IDP field to [Current]
-
Set the Value field to Authenticating IDP
-
Select the name of an identity provider
For the condition to evaluate to True, the identity provider specified in the policy must be the one that the user selected for authentication.
Comparison: Specify how the contract is compared to the data in Value. Select a string comparison or a regular expression:
-
Comparison: String: Specifies that you want the values compared as strings and how you want the string values compared. Select one of the following:
-
Equals: Indicates that the values must match, letter for letter.
-
Starts with: Indicates that the Authenticating IDP value must begin with the letters specified in Value.
-
Ends with: Indicates that the Authenticating IDP value must end with the letters specified in Value.
-
Contains Substring: Indicates that the Authenticating IDP value must contain the letters, in the same sequence, as specified in Value.
-
-
Comparison: Regular Expression: Matches: Specifies that you want the values compared as regular expressions.
Mode: Select the mode appropriate for the comparison type:
-
Comparison: String: Select Case Sensitive or Case Insensitive.
-
Comparison: Regular Expression: Matches: Select one or more of the following:
- Canonical Equivalence
- Case Insensitive
- Comments
- Dot All
- Multi-Line
- Unicode
- Unix Lines
For regular expression syntax information, see the Javadoc for java.util.regex.Pattern.
Value: Specify the value you want to compare with the Authenticating IDP value. If you select a static value for the Authenticating IDP value, select Authenticating IDP and Current. If you select Current for the Authenticating IDP value, select Authenticating IDP, then select the name of an identity provider.
Other value types are possible if you selected Current for the Authenticating IDP value. Your policy requirements determine whether they are useful.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select either False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
Authentication Contract Condition
The Authentication Contract allows you to assign a role based on the contract the user used for authentication. Identity Server has the following default contracts:
|
Name |
URI |
|---|---|
|
Name/Password - Basic |
basic/name/password/uri |
|
Name/Password - Form |
name/password/uri |
|
Secure Name/Password - Basic |
secure/basic/name/password/uri |
|
Secure Name/Password - Form |
secure/name/password/uri |
To configure other contracts, click Devices > Identity Servers > Edit > Local > Contracts.
The most common way to use this condition is to select [Current] for Authentication Contract and to select Authentication Contract and the name of a contract for Value.
To specify an Authentication Contract condition, specify the following details:
Authentication Contract: To compare the contract that the user used with a static value, select Current. To compare a static value with what the user used, select a contract from the list.
If you have created more than one Identity Server configuration, select the configuration, then select the contract. The name of the contract is displayed. When you select this name, the configurations that contain a definition for this contract are highlighted.
For example, the following policy has selected Name/Password - Basic as the contract.
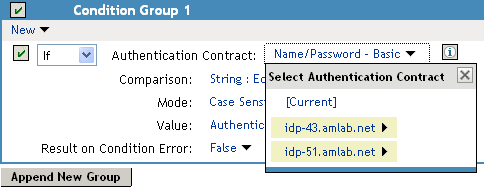
Two Identity Server configurations have been defined (idp-43.amlab.net and idp-51.amlab.net). Both configurations are highlighted because Name/Password - Basic is a contract that is automatically defined for all Identity Server configurations.
If the contract you are selecting for a condition is a contract with ORed credentials, you need to use multiple conditions to set up a rule. See Creating a Rule for a Contract with ORed Credentials.
Comparison: Specify how the contract is compared to the data in the Value field. Select either a string comparison or a regular expression:
-
Comparison: String: Specifies that you want the values compared as strings and how you want the string values compared. Select one of the following:
-
Equals: Indicates that the values must match, letter for letter.
-
Starts with: Indicates that the Authentication Contract value must begin with the letters specified in the Value field.
-
Ends with: Indicates that the Authentication Contract value must end with the letters specified in the Value field.
-
Contains Substring: Indicates that the Authentication Contract value must contain the letters, in the same sequence, as specified in the Value field.
-
-
Comparison: Regular Expression: Matches: Specifies that you want the values compared as regular expressions.
Mode: Select the mode appropriate for the comparison type:
-
Comparison: String: Specify whether case is important by selecting Case Sensitive or Case Insensitive.
-
Comparison: Regular Expression: Matches: Select one or more of the following:
- Canonical Equivalence
- Case Insensitive
- Comments
- Dot All
- Multi-Line
- Unicode
- Unix Lines
For regular expression syntax information, see the Javadoc for java.util.regex.Pattern.
Value: Specify the value you want to compare with the Authentication Contract value. If you select a static value for the Authentication Contract value, select Authentication Contract and Current. If you select Current for the Authentication Contract value, select Authentication Contract, then select the name of a contract.
Other value types are possible if you selected Current for the Authentication Contract value. For example:
-
You can select Data Entry Field. The value specified in the text box must be the URI of the contract for the conditions to match. For a list of these values, click Devices > Identity Servers > Edit > Local > Contracts.
-
If you have defined a Liberty User Profile attribute for URI of the authentication contract, you can select Liberty User Profile, then select the attribute.
-
If you have defined an LDAP attribute for URI of the authentication contract, you can select LDAP Attribute, then select the attribute.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select either False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
Authentication Method Condition
The Authentication Method allows you to assign a role based on the method the user used for authentication.
Authentication Method: To compare the method that the user used with a static value, select Current. To compare a static value with what the user used, select a method from the list.
If you have created more than one Identity Server configuration, select the configuration, then select the method. The name of the method is displayed. When you select this name, the configurations that contain a definition for this method are highlighted.
Comparison: Specify how the method is compared to the data in the Value field. Select either a string comparison or a regular expression:
-
Comparison: String: Specifies that you want the values compared as strings and how you want the string values compared. Select one of the following:
-
Equals: Indicates that the values must match, letter for letter.
-
Starts with: Indicates that the Authentication Method value must begin with the letters specified in the Value field.
-
Ends with: Indicates that the Authentication Method value must end with the letters specified in the Value field.
-
Contains Substring: Indicates that the Authentication Method value must contain the letters, in the same sequence, as specified in the Value field.
-
-
Comparison: Regular Expression: Matches: Specifies that you want the values compared as regular expressions.
Mode: Select the mode appropriate for the comparison type:
-
Comparison: String: Specify whether case is important by selecting Case Sensitive or Case Insensitive.
-
Comparison: Regular Expression: Matches: Select one or more of the following:
- Canonical Equivalence
- Case Insensitive
- Comments
- Dot All
- Multi-Line
- Unicode
- Unix Lines
For regular expression syntax information, see the Javadoc for java.util.regex.Pattern.
Value: Specify the value you want to compare with the Authentication Method value. If you select a static value for the Authentication Method value, select Authentication Method and Current. If you select Current for the Authentication Method value, select Authentication Method, then select the name of a method.
Other value types are possible if you selected Current for the Authentication Method value. Your policy requirements determine whether they are useful.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select either False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
Authentication Type Condition
The Authentication Type condition allows you to assign a role based on the authentication types used to authenticate the current user. The [Current] selection represents the current set of authentication types used to authenticate the user. The other selections represent specific authentication types that can be used to compare with [Current]. The Authentication Type condition returns true if the selected Authentication Type is contained in the set of Authentication Types for [Current]. For example, if the current user was required to satisfy the Authentication Types of Basic and SmartCard, then a selected Authentication Type of either Basic or SmartCard would match.
Authentication Type: To compare the type that the user used with a static value, select Current. To compare a static value with what the user used, select a type from the list.
Comparison: Specify how the type is compared to the data in the Value field. Select either a string comparison or a regular expression:
-
Comparison: String: Specifies that you want the values compared as strings and how you want the string values compared. Select one of the following:
-
Equals: Indicates that the values must match, letter for letter.
-
Starts with: Indicates that the Authentication Type value must begin with the letters specified in the Value field.
-
Ends with: Indicates that the Authentication Type value must end with the letters specified in the Value field.
-
Contains Substring: Indicates that the Authentication Type value must contain the letters, in the same sequence, as specified in the Value field.
-
-
Comparison: Regular Expression: Matches: Specifies that you want the values compared as regular expressions.
Mode: Select the mode appropriate for the comparison type:
-
Comparison: String: Specify whether the case is important by selecting Case Sensitive or Case Insensitive.
-
Comparison: Regular Expression: Matches: Select one or more of the following:
- Canonical Equivalence
- Case Insensitive
- Comments
- Dot All
- Multi-Line
- Unicode
- Unix Lines
For regular expression syntax information, see the Javadoc for java.util.regex.Pattern.
Value: Specify the value you want to compare with the Authentication Type value. If you select a static value for the Authentication Type value, select Authentication Type and Current. If you select Current for the Authentication Type value, select Authentication Type, then select a type.
Other value types are possible if you selected Current for the Authentication Type value. Your policy requirements determine whether they are useful.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select either False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
Credential Profile Condition
The Credential Profile condition allows you to assign a role based on the credentials the user entered when authenticating to the system. Only values used at authentication time are available for this comparison.
To set up the matching for this condition, specify the following details:
Credential Profile: Specify the type of credential your users are using for authentication. If you have created a custom contract that uses a credential other than the ones listed below, do not use the Credential Profile as a Role condition.
-
LDAP Credentials: If you prompt the user for a username, select this option, then select LDAP User Name (the cn of the user) or LDAP User DN (the fully distinguished name of the user), or LDAP Password.
The default contracts assign the cn attribute to the Credential Profile. If your user store is an Active Directory server, the SAMAccountName attribute is used for the username and stored in the cn field of the LDAP Credential Profile.
-
X509 Credentials: If you prompt the user for a certificate, select this option, then select one of the following:
-
X509 Public Certificate Subject: Retrieves the subject field from the certificate, which can match the DN of the user, depending upon who issued the certificate.
-
X509 Public Certificate Issuer: Retrieves the issuer field from the certificate, which is the name of the certificate authority (CA) that issued the certificate.
-
X509 Public Certificate: Retrieves the entire certificate, Base64 encoded.
-
X509 Serial Number: Retrieves the serial number of the certificate.
-
-
SAML Credential: If your users authenticate with a SAML assertion, select this option.
Comparison: Select one of the following types:
-
Comparison: String: Specifies that you want the values compared as strings and indicates how you want the string values compared. Select one of the following:
-
Equals: Indicates that the values must match, letter for letter.
-
Starts with: Indicates that the Credential Profile value must begin with the letters specified in Value.
-
Ends with: Indicates that the Credential Profile value must end with the letters specified in Value.
-
Contains Substring: Indicates that the Credential Profile value must contain the letters, in the same sequence, as specified in Value.
-
-
Comparison: Regular Expression: Matches: Specifies that you want the values compared as regular expressions.
Mode: Select the mode appropriate for the comparison type:
-
Comparison: String: Specify whether case is important by selecting Case Sensitive or Case Insensitive.
-
Comparison: Regular Expression: Matches: Select one or more of the following:
- Canonical Equivalence
- Case Insensitive
- Comments
- Dot All
- Multi-Line
- Unicode
- Unix Lines
For regular expression syntax information, see the Javadoc for java.util.regex.Pattern.
Value: Specify the second value for the comparison. Select one of the following data types:
-
LDAP Attribute: If you have an LDAP attribute that corresponds to the Credential Profile you have specified, select this option and the attribute.
-
Liberty User Profile: If you have a Liberty User Profile attribute that corresponds to the Credential Profile you have specified, select this option and the attribute.
-
Data Entry Field: Specify the string you want matched. Be aware of the following requirements:
-
If you selected LDAP User DN as the credential, you need to specify the DN of the user in the Value text box. If the comparison type is set to Contains Substring, you can match a group of users by specifying a common object that is part of their DNs, for example ou=sales.
-
If you selected X509 Public Certificate Subject as the credential, you need to specify all elements of the Subject Name of the certificate in the Value text box. Separate the elements with a comma and a space, for example, o=novell, ou=sales. If the comparison type is set to Contains Substring, you can match a group of certificates by specifying a name that is part of the Subject Name, for example ou=sales.
-
Other values are possible. Your policy requirements determine whether they are useful.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
LDAP Group Condition
The LDAP Group condition allows you to assign a role based on whether the authenticating user is a member of a group. The value, an LDAP DN, must be a fully distinguished name of a group.
LDAP Group: Select [Current].
Comparison: Specify how you want the values compared. Select one of the following:
-
LDAP Group: Is Member of: Specifies that you want the condition to determine whether the user is member of a specified group.
-
Comparison: Regular Expression: Matches: Specifies that you want the values compared as regular expressions.
Mode: If you selected Regular Expression: Matches as the comparison type, select one or more of the following:
- Canonical Equivalence
- Case Insensitive
- Comments
- Dot All
- Multi-Line
- Unicode
- Unix Lines
For regular expression syntax information, see the Javadoc for java.util.regex.Pattern.
Value: Specify the second value for the comparison. If you select LDAP Group > Name of Identity Server Configuration > User Store Name, you can browse to the name of the LDAP group.
If you have more than 250 groups in your tree, you are prompted to enter an LDAP query string. In the text box, you need to add only the <strFilter> value for the query.
For example:
|
<strFilter> Value |
Description |
|---|---|
|
admin* |
Returns all groups that begin with admin, such as adminPR, adminBG, and adminWTH. |
|
*test |
Returns all groups that end with test, such as doctest, softtest, and securtest. |
|
*low* |
Returns all groups that have “low” in the name, such as low, yellow, and clowns. |
For more information about the <strFilter> parameter, see RFC 2254 “LDAP Search Filter.”
If you select Data Entry Field as the value, you can specify the DN of the group in the text field. For example:
cn=managers,cn=users,dc=bcf2,dc=provo,dc=novell,dc=com
cn=manager,o=novell
Other values are possible. Your policy requirements determine whether they are useful.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select either False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
LDAP OU Condition
The LDAP OU condition allows you to assign a role based on a comparison of the DN of an OU against the DN of the authenticated user. If the user’s DN contains the OU, the condition matches.
LDAP OU: Select [Current].
Comparison: Specify how you want the values compared. Select one of the following:
-
Contains: Specifies that you want the condition to determine whether the user is contained by a specified organizational unit.
-
Comparison: Regular Expression: Matches: Specifies that you want the values compared as regular expressions.
Mode: Select the mode appropriate for the comparison type.
-
Contains: Select whether the user must be contained in the specified OU (One Level) or whether the user can be contained in the specified OU or a child container (Subtree).
-
Comparison: Regular Expression: Matches: Select one or more of the following:
- Canonical Equivalence
- Case Insensitive
- Comments
- Dot All
- Multi-Line
- Unicode
- Unix Lines
For regular expression syntax information, see the Javadoc for java.util.regex.Pattern.
Value: Specify the second value for the comparison. If you select LDAP OU > Name of Identity Server Configuration > User Store Name, you can browse to the name of the OU.
If you have more than 250 OUs defined in your tree, you are prompted to enter an LDAP query string. In the text box, you need to add only the <strFilter> value for the query. For example:
|
<strFilter> Value |
Description |
|---|---|
|
admin* |
Returns all OUs that begin with admin, such as adminPR, adminBG, and adminWTH. |
|
*test |
Returns all OUs that end with test, such as doctest, softtest, and securtest. |
|
*low* |
Returns all OUs that have “low” in the name, such as low, yellow, and clowns. |
For more information about the <strFilter> parameter, see RFC 2254 “LDAP Search Filter.”
If you select Data Entry Field, you can specify the DN of the OU in the text field. For example:
cn=users,dc=bcf2,dc=provo,dc=novell,dc=com
ou=users,o=novell
If you have defined a Liberty User Profile or an LDAP attribute for the OU you want to match, select this option, then select your attribute.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select either False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
LDAP Attribute Condition
The LDAP Attribute condition allows you to assign a role based on a value in an LDAP attribute defined for the inetOrgPerson class or any other LDAP attribute you have added. You can have the user’s attribute value retrieved from your LDAP directory and compared to a value of the following type:
-
Roles from an identity provider
-
Authenticating IDP or user store
-
Authentication contract, method, or type
-
Credential profile
-
LDAP attribute, OU, or group
-
Liberty User Profile attribute
-
Static value in a data entry field
To set up the matching for this condition, specify the following details:
LDAP Attribute: Specify the LDAP attribute you want to use in the comparison. Select from the listed LDAP attributes. To add an attribute that isn’t in the list, click New LDAP Attribute, then specify the name of the attribute.
Comparison: Specify how you want the values compared. All data types are available. Select one that matches the value type of your attribute.
Mode: Select the mode, if available, that matches the comparison type. For example, if you select to compare the values as strings, you can select either a Case Sensitive mode or a Case Insensitive mode.
Value: Specify the second value for the comparison. All data types are available. For example, you can select to compare the value of one LDAP attribute to the value of another LDAP attribute. Only you can determine if such a comparison is meaningful.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select either False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
Liberty User Profile Condition
The Liberty User Profile condition allows you to assign a role based on a value in a Liberty User Profile attribute. The Liberty attributes must be enabled before you can use them in policies (click Identity Servers > Edit > Liberty > Web Service Provider, then enable one or more of the following: Employee Profile or Personal Profile).
These attributes can be mapped to LDAP attributes. Click Identity Servers > Edit > Liberty > LDAP Attribute Mapping. When mapped, the actual value comes from your user store. If you are using multiple user stores with different LDAP schemas, mapping similar attributes to the same Liberty User Profile attribute allows you to create one policy with the Liberty User Profile attribute rather than multiple policies for each LDAP attribute.
The selected attribute is compared to a value of the following type:
-
Roles from an identity provider
-
Authenticating IDP or user store
-
Authentication contract, method, or type
-
Credential profile
-
LDAP attribute, OU, or group
-
Liberty User Profile attribute
-
Static value in a data entry field
To set up the matching for this condition, specify the following details:
Liberty User Profile: Select the Liberty User Profile attribute. These attributes are organized into three main groups: Custom Profile, Corporate Employment Identity, and Entire Personal Identity. By default, the Common Last Name attribute for Liberty User Profile is mapped to the sn attribute for LDAP. To select this attribute for comparison, click Entire Personal Identity > Entire Common Name > Common Analyzed Name > Common Last Name.
Comparison: Select the comparison type that matches the data type of the selected attribute and the value.
Mode: Select the mode, if available, that matches the data type. For example, if you select to compare the values as strings, you can select a Case Sensitive mode or a Case Insensitive mode.
Value: Select one of the values that is available from the current request or select Data Entry Field to enter a static value. The static value that you can enter depends on the comparison type you selected.
Result on Condition Error: Specify what the condition returns when the comparison of two values returns an error rather than the results of the comparison. Select False or True. For example, if you do not want the action applied when an error occurs, select False.
Roles from Identity Provider Condition
The Roles from Identity Provider condition allows you to assign a role based on a role assigned by another identity provider (Liberty, SAML 2.0, WS Federation). Configure a condition to match the role sent by the identity provider, then set the action to assign a new role.
This condition uses the mapped attribute All Roles. All roles that are assigned to the user can be mapped to attributes and assigned to a trusted identity provider. For information about enabling All Roles, see Selecting Attributes for a Trusted Provider.
For an example of using Roles from Identity Provider to create a Role policy, see Mapping Roles between Trusted Providers. For examples of procedures required to share roles, see Sharing Roles.
To configure a Roles from Identity Provider condition, specify the following details:
Roles from Identity Provider: If you have configured your system for multiple identity providers, select the identity provider. If you have only one, it is selected.
Comparison: Select one of the following types:
-
Comparison: String: Specifies that you want the values compared as strings, and how you want the string values compared. Select one of the following:
-
Equals: Indicates that the values must match, letter for letter.
-
Starts with: Indicates that the Roles from Identity Provider value must begin with the letters specified in Value.
-
Ends with: Indicates that the Roles from Identity Provider value must end with the letters specified in Value.
-
Contains Substring: Indicates that the Roles from Identity Provider value must contain the letters in the same sequence, as specified in Value.
-
-
Comparison: Regular Expression: Matches: Specifies that the values compared as regular expressions.
Mode: Select the mode appropriate for the comparison type:
-
Comparison: String: Select Case Sensitive or Case Insensitive.
-
Comparison: Regular Expression: Matches: Select one or more of the following:
- Canonical Equivalence
- Case Insensitive
- Comments
- Dot All
- Multi-Line
- Unicode
- Unix Lines
For regular expression syntax information, see the Javadoc for java.util.regex.Pattern.
Value: Select Data Entry Field, then specify the name of an identity provider role. Other value types are possible. Your policy requirements determine whether they are useful
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select either False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
User Store Condition
The User Store condition allows you to assign a role based on the user store that was used to authenticate the current user. The [Current] selection represents the user store from which the user was authenticated. The other selections represent all of the configured user stores that can be used to compare with [Current].
For example, if the configured user stores are eDir1 and AD1 and the current user is authenticated from eDir1, then a selected user store of eDir1 would match and a selected user store of AD1 would not match.
User Store: To compare the user store that the user used for authentication with a static value, select Current. To compare a static value with what the user used, select a user store from the list.
If you have created more than one Identity Server configuration, select the configuration, then select the user store. The name of the user store is displayed.
Comparison: Specify how the user store is compared to the data in the Value field. Select either a string comparison or a regular expression:
-
Comparison: String: Specifies that you want the values compared as strings and how you want the string values compared. Select one of the following:
-
Equals: Indicates that the values must match, letter for letter.
-
Starts with: Indicates that the User Store value must begin with the letters specified in the Value field.
-
Ends with: Indicates that the User Store value must end with the letters specified in the Value field.
-
Contains Substring: Indicates that the User Store value must contain the letters, in the same sequence, as specified in the Value field.
-
-
Comparison: Regular Expression: Matches: Specifies that you want the values compared as regular expressions.
Value: Specify the value you want to compare with the User Store value. If you select a static value for the User Store value, select User Store and Current. If you select Current for the User Store value, select User Store, then select the name of a user store.
If you have created more than one Identity Server configuration, select the configuration, then select the user store. The name of the user store is displayed.
Other value types are possible if you selected Current for the User Store value. Your policy requirements determine whether they are useful.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
Virtual Attribute Condition
The Virtual Attribute condition allows you to assign a role based on a value in an Virtual attribute. You can have the user’s attribute value retrieved from an external source and compared to a value of the following type:
-
Roles from an identity provider
-
Authenticating IDP or user store
-
Authentication contract, method, or type
-
Credential profile
-
LDAP attribute, OU, or group
-
Liberty User Profile attribute
-
Static value in a data entry field
-
Virtual Attribute
To set up the matching for this condition, specify the following details:
Virtual Attribute: Specify the virtual attribute you want to use in the comparison. Select a virtual attribute from the list.’
Comparison: Specify how you want the values compared. All data types are available. Select one that matches the value type of your virtual attribute.
Mode: Select the mode, if available, that matches the comparison type. For example, if you select to compare the values as strings, you can select a Case Sensitive mode or a Case Insensitive mode.
Value: Specify the second value for the comparison. All data types are available. For example, you can select to compare the value of one virtual attribute to the value of another virtual attribute. Only you can determine if such a comparison is meaningful.
Result on Condition Error: Specify what the condition returns when the comparison of the two values returns an error rather than the results of the comparison. Select either False or True. If you do not want the action applied when an error occurs, select False. If you want the action applied when an error occurs, select True.
Condition Extension
If you have loaded and configured a role condition extension, this option specifies a condition that is evaluated by an outside source. See the documentation that came with the extension for information about what is evaluated.
Data Extension
If you have loaded and configured a role data extension, this option specifies the value that the extension retrieves. You can then select to compare this value with an LDAP attribute, a Liberty User Profile attribute, a Data Entry Field, or another Data Extension. For more information, see the documentation that came with the extension.