Configure Access Rights (ACLs) for a Repo
Note: This section is for system administrators only.
GitCentric implements a group-based ACLs security model derived from
Gerrit Code Review. This is a powerful tool for defining who can do what with
Git repositories under
GitCentric control. You will need to have a solid understanding of these group-based ACLs and do some planning before implementing them,
so be sure to first read the following section:
GitCentric Group-Based ACLs, and the
Gerrit Code Review documentation for details.
Use the following general procedure for settings ACLs on your repos.
-
Click the
Administration button and then click the
Repositories menu.
The Repositories page appears. See Administration for more information.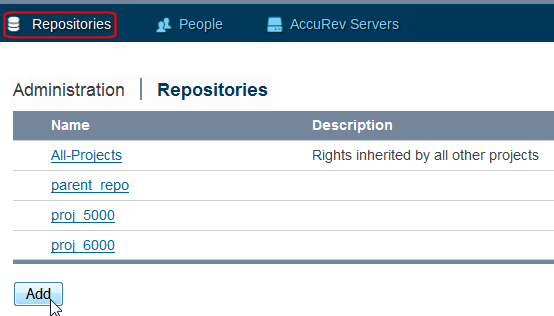
-
Click the repository you want to configure. Selecting
All-Projects will cause all other repositories to inherit whatever ACLs you apply.
Note: Only the All-Projects system-defined repo has a Global Capabilities section with an Administrate Server permission which gives Administrators broad powers across all repos. Be extremely careful when editing this permission.)
-
On the
Repositories page, click the
Access button. For more information, see
Access Page.
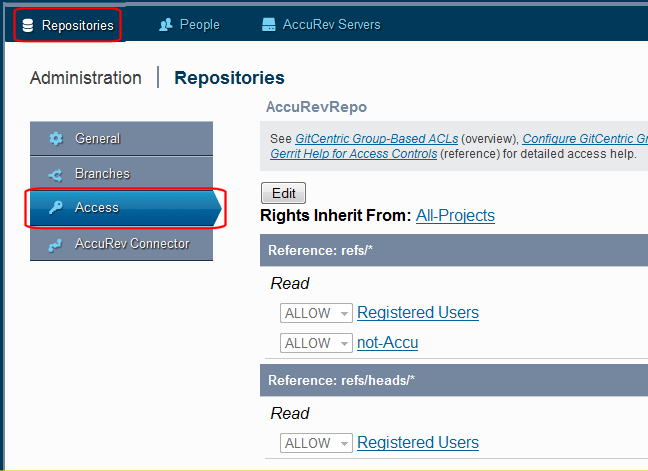
- Use the Rights Inherit From: link to specify the repository from which you want the new repository to inherit its access settings. (By default, all repositories inherit access rights from the system-defined All-Projects. You can create a parent-only repository to easily apply settings such as this to all child repositories. See Create a Repository for GitCentric for more information.)
- Click Edit, then Add Reference. In the Reference field, you can accept the default value (refs/ heads/*) to apply the access setting to all branches in repository, or modify it to apply to a specific branch. Specifying refs/* applies the ACL to everything in the repo.
-
Select the permission that you want to apply to this repository from the list.
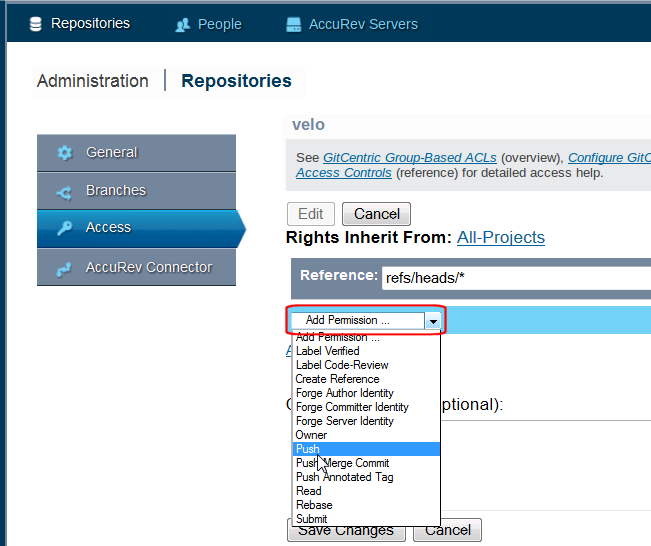
-
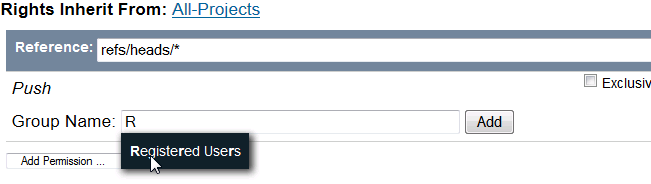
After selecting the permission, complete the
Group Name field for whom this permission applies in the this repository. The field supports type-ahead, so, for instance, entering
R will provide
Registered Users as a possible completion.
- Optionally enter a commit message. An admin user can view this when performing a git log refs/meta/config command on the repository.
- When done, click the Save Changes button.