Generating Authentication Tokens
You can generate authentication![]() Identity verification, typically with passwords. Authentication precedes authorization. tokens from either the ADMINISTRATION view in Fortify Software Security Center, or from the command-line interface. Only you can see the details of your tokens. The Fortify Software Security Center administrator can extend the life of the tokens you create. but cannot see detailed information about your tokens.
Identity verification, typically with passwords. Authentication precedes authorization. tokens from either the ADMINISTRATION view in Fortify Software Security Center, or from the command-line interface. Only you can see the details of your tokens. The Fortify Software Security Center administrator can extend the life of the tokens you create. but cannot see detailed information about your tokens.
Note: Be aware that you can create a token of any type, but if you do not have the permission required to perform the action that the token is designed to perform, you will not be able to use the token.
Generating a Token from the ADMINISTRATION View
To generate an authentication token![]() Unique keys that enable users to automate actions within Fortify Software Security Center without using passwords. The user requests a token, authenticates to the Fortify Software Security Center server, and receives back a string that is permissioned for a small set of time-limited actions. Fortify Scan Analytics also generates authentication tokens that are required to configure a connection between Scan Analytics and Fortify Software Security Center. from the Fortify Software Security Center user interface:
Unique keys that enable users to automate actions within Fortify Software Security Center without using passwords. The user requests a token, authenticates to the Fortify Software Security Center server, and receives back a string that is permissioned for a small set of time-limited actions. Fortify Scan Analytics also generates authentication tokens that are required to configure a connection between Scan Analytics and Fortify Software Security Center. from the Fortify Software Security Center user interface:
- On the Fortify page header, select ADMINISTRATION.
- In the left panel of the ADMINISTRATION view, expand the Users section, and then select Token Management.
-
On the Token Management toolbar, click NEW.
The Create Token dialog box opens.
-
From the Token Type list, select the type of token you want to create.
To see a list of available token types, see the table in Generating a Token from the Command Line.
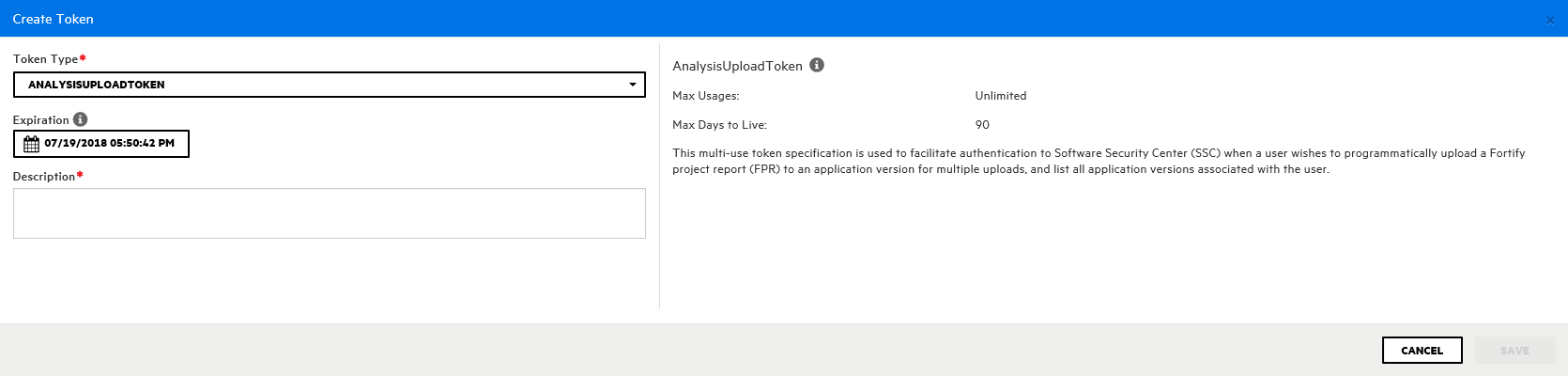
The Create Token dialog box displays a description of the selected token type in the right panel.
-
Use the Expiration calendar control to specify the date on which the token is to expire. (The expiration time is set to the current time on the specified date.)
Note: By default, the expiration date value is set to the maximum number of days to live for the selected token type. You can set this to an earlier date to give the token a shorter life. You can also extend the life of the token later.
- In the Description box, type a description of the intended use of the new token.
-
Click SAVE.
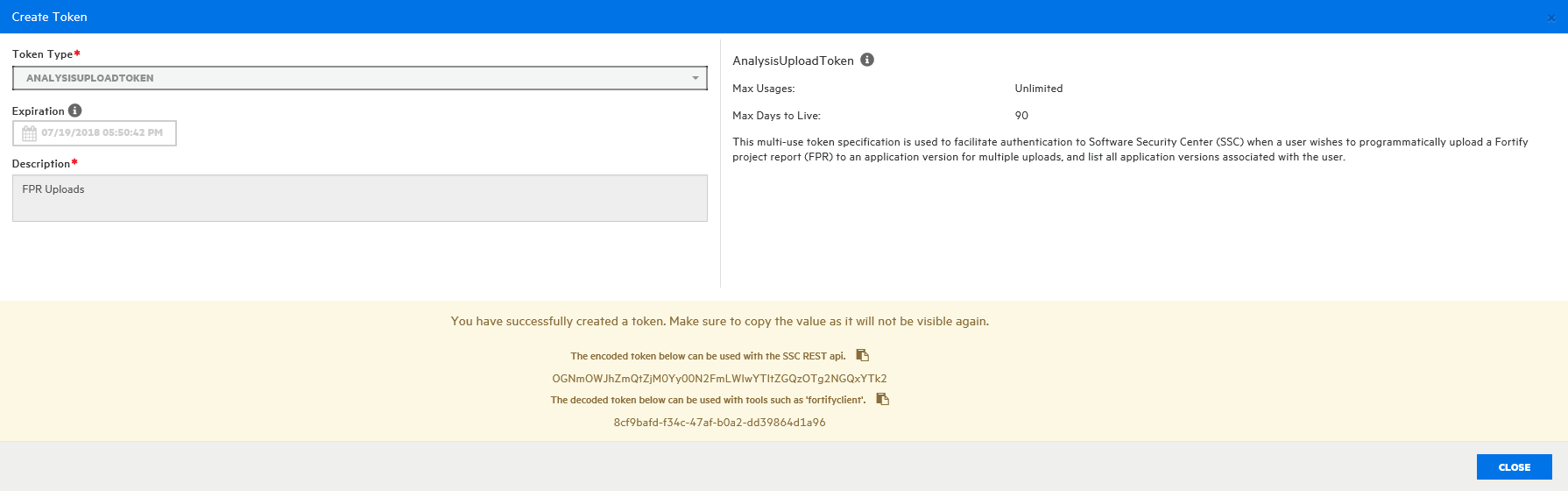
The Create Token dialog box displays a message to let you know the token was successfully created.
- At the bottom of the message, copy either the encoded or decoded token string and save it. (Software Security Center will not display these again.)
-
Click CLOSE
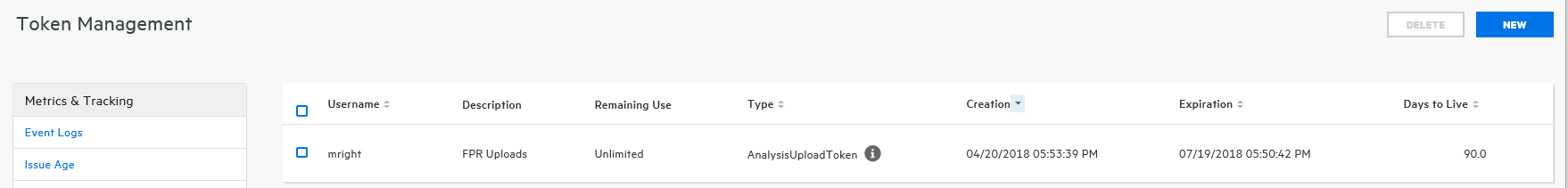
The Token Management page now lists the new token.
Generating a Token from the Command Line
To generate a token from the command line, run the following:
fortifyclient token -gettoken <token_name> -url SSC_URL -user USERNAME ‑password
The following table lists the available token_name options.
|
Option |
Description |
|---|---|
| AnalysisDownloadToken | Download merged result files |
|
AnalysisUploadToken |
Upload scan results to Fortify Software Security Center and list applications |
|
AuditToken |
Load details about current security issues and apply analysis tags |
| CIToken | Enables integration of Software Security Center with continuous integration plugins |
| CloudCtrlToken | Obsolete - replaced with ScanCentralCtrlToken |
| CloudOneTimeJobToken | Obsolete - replaced with ScanCentralOneTimeJobToken |
| DownloadFileTransferToken | Typically created programmatically by automation scripts using the /fileTokens endpoint to support a file download within an authenticated session |
| PurgeProjectVersionToken | Provides the capability to programmatically request a list of all application |
| ReportFileTransferToken | Typically created programmatically by automation scripts using the /fileTokens endpoint to support downloading an existing report within an authenticated session |
|
ReportToken |
Enables users to: Request list of saved reports Request saved report based on the report ID Delete saved reports Return list of saved reports associated with a specific application version Generate new reports |
| ScanCentralCtrlToken |
For ScanCentral communications using the Fortify ScanCentral |
| ScanCentralOneTimeJobToken |
Single-use token specification typically created programmatically by the ScanCentral client |
| UnifiedLoginToken | Enables access to most of the REST API. It is intended for short-run automations that last less than a day |
| UploadFileTransferToken | Typically created programmatically by automation scripts using the /fileTokens endpoint to support a file upload within an authenticated session |
| VSTSExtensionToken | Multi-use token specification used by the Fortify Azure DevOps extension to upload FPR(s) to Fortify Software Security Center and, optionally, submit a scan to Fortify ScanCentral. |
| WIESystemToken | Internal token specification created programmatically by Fortify WebInspect Enterprise |
| WIEUserToken | Internal token specification created programmatically by Fortify WebInspect Enterprise. (Not for individual use.) |
Authentication tokens are defined at runtime in WEB-INF/internal/serviceContext.xml.
See Also
Specifying DaysToLive for fortifyclient Authentication Tokens.