7.4 NURM (OES User Rights Map)
The OES User Rights Map (NURM) utility is used by administrators to map the Access Control List (ACL) of NSS resource that is owned by an identity in eDirectory to an identity in Active Directory. It maps the users and groups from eDirectory to Active Directory using a common name or any other field that is selectable by the tool. With this utility, the administrators can:
-
Create User Maps: Map eDirectory and Active Directory users and groups.
-
Leverage Existing IDM-based User Maps: Leverage NetIQ Identity Manager 4.5 or later maps that are created using IDM Designer (but not the IDM iManager plug-in).
-
Map User Rights: Assign rights to Active Directory users on NSS resources.
-
View Rights: View the rights of Active Directory and eDirectory users on a given volume.
-
Synchronizing Rights: Synchronize the rights of Active Directory and eDirectory users using the user-rights-map command line utility.
7.4.1 Prerequisites
-
Ensure that the universal password is enabled for the eDirectory user who is accessing NURM. This utility uses CIFS to fetch the volume information. Hence, when a user who is not universal-password-enabled accesses NURM, the volumes are not listed under the View Rights and Map Rights pages. For more information on enabling Universal Password Policy, see
CIFS and Universal Password
in the OES 2018 SP3: OES CIFS for Linux Administration Guide. -
The eDirectory user managing NURM must have read and write access on the /_admin/Manage_NSS/manage.cmd.
-
Ensure that CIFS user context is configured for the eDirectory user who is accessing NURM. For more information, see
Configuring a CIFS User Context
in the OES 2018 SP3: OES CIFS for Linux Administration Guide. -
If you are to use NURM in an environment where eDirectory and Active Directory are synchronized using NetIQ IDM, ensure that DirXML-ADContext attribute is populated in eDirectory server.
7.4.2 Accessing OES User Rights Map Utility (NURM)
Along with the installation and configuration of NSS AD, the NURM utility gets installed.To access the NURM:
-
Open the OES server welcome page, then click Management Services > OES User Rights Map.
OR
Point your browser to https://<OES server IP address or the host name>/storm.
-
Specify the user name or the FQDN of the eDirectory administrator in the User Name, specify the password, then click Login.
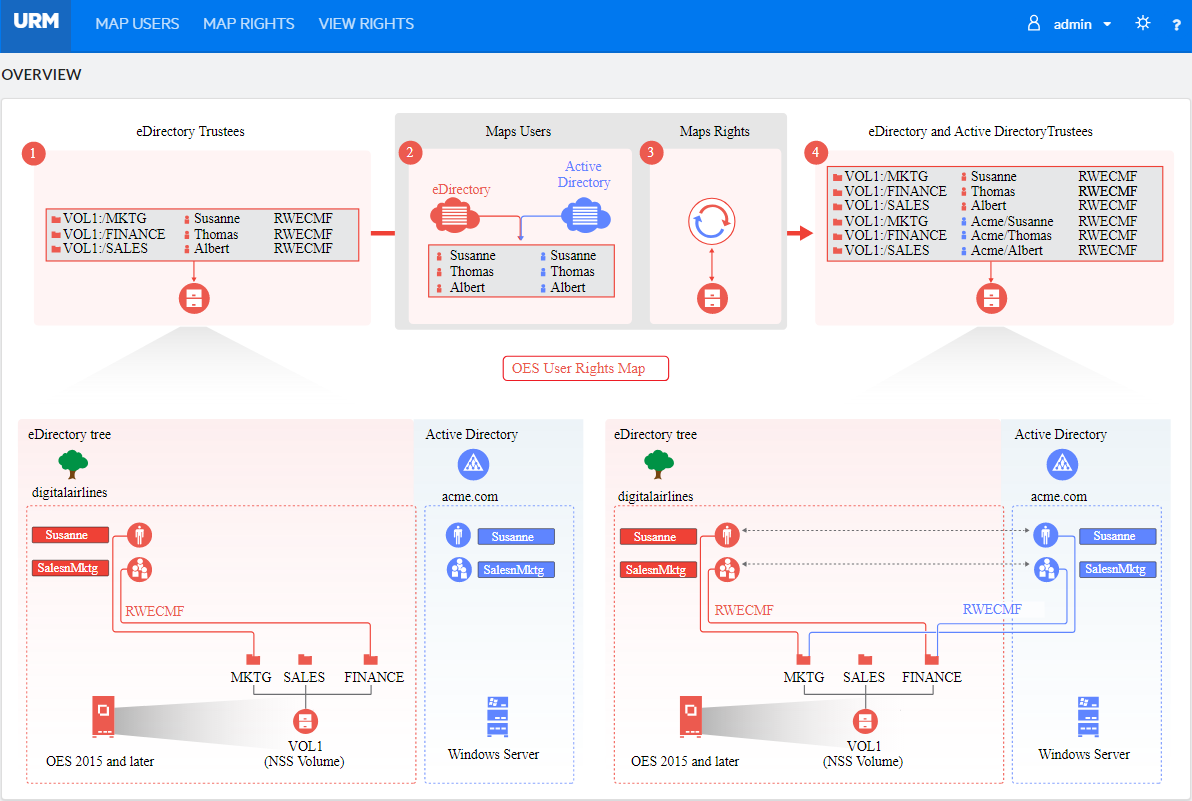
The NURM welcome page should look similar to the following:
NURM is also available as a command line utility (user-rights-map). For more information on the CLI utility, see Section 7.4.7, NURM Command Line Utility.
7.4.3 Mapping Users
In an NSS AD environment, OES servers are joined to an Active Directory domain to provision AD users and groups native NSS resources access. To aid this, identities from Active directory will have to be mapped with identities on eDirectory and assigned the same rights as that of the eDirectory identities. NURM helps in creating this identity map, which is called a user map
. User maps are used to assign rights to AD identities on the NSS resources.
Using the Map Users feature, administrators can do the following:
-
Create new user maps: Map eDirectory and Active Directory (AD) users and groups.
-
Import user maps
-
Export user maps
-
Refresh user maps
-
Delete user maps
Before creating user maps, ensure that you are connected to an AD server.
Connecting to an Active Directory Server
Whenever an authentication is required, Connect to Active Directory pop-up window is displayed. For example: In Map Users page, click  icon and specify the following details, then click Connect to connect to the target AD server.
icon and specify the following details, then click Connect to connect to the target AD server.
-
User Name: Specify the AD Administrator user name or the FQDN.
-
Password: Specify the AD Administrator password.
-
Domain Name: Specify the realm of the AD domain.
-
Port: Specify the port with which you would like to connect to the AD server. If you would like this connection to be secure, select Use SSL. Some of the standard LDAP ports for Active Directory are 389, 636, 3268, and 3269.
NOTE:
-
NURM supports multiple AD forests. Login to the respective forest before generating the user map.
-
When connecting to Active Directory, specify the credentials of the respective domain (PDC or CDC) where the users or groups exists.
Creating a New User Map
-
Click
 , then specify the following details:
, then specify the following details:-
Match Type: Select an object mapping (user to user, group to group, or container to group). In the Target Matching Pattern, specify the wildcard-based search criteria.
For example, if you want to match a group from the source identity store with a group on the target identity store that differs in naming conventions, you can use the Target Matching Pattern.
For example, assume that you have the following groups on the source identity: eng-group-acme, sales-group-acmeUS, and so on; and technology-acme, sales-acmeUS, and so on in the target identity. In the Target Matching Pattern, specifying *-acme finds the match from eng-group-acme and technology-acme groups.
-
LDAP Attributes: Select Common Name to Common Name (CN to CN), Common Name to SAM-Account-Name (CN to SAM), or Custom Attributes matching criteria.
If you choose custom attributes, you will have to specify the eDirectory and Active Directory object attributes.
Examples of eDirectory object attributes include User Name (uid), Common Name (cn), Last Name (sn), First Name (givenName), Full Name (fullName), and Internet E-mail address (mail).
Examples of Active Directory object attributes include Common Name (cn), Full Name (name), SamAccount Name (sAMAccountName), First Name (givenName), Last Name (sn), Display Name (displayName), Internet E-mail address (mail), UserPrincipleName.
-
eDirectory Context: Specify or browse and select the eDirectory tree search base context. The Search Subtree option is enabled by default.
-
Active Directory Context: Specify or browse and select the AD server context. The Search Subtree option is enabled by default.
-
-
Click Show to generate and view the user map. To propose a usermap of your choice, go to Step 3.
OR
Click Save to generate and store the user map on the server.
NOTE:If you choose to store the user map on the server, you can validate and modify the user map only after it gets listed in the Map Users page.
-
Validate the user mapping. If you need to modify any user mapping:
-
Click on selected Active Directory context and browse to the appropriate AD server context, then click Select.
-
To replace or add an AD user in the proposed user map, select a row in the proposed user map, then click
 .
. -
To remove a user from the proposed user map, click
 . To undo the deletion, click
. To undo the deletion, click  .
. -
Click Save Map to save all the changes.
HINT:
-
To modify an existing user mapping, click the user map name in the Map Users page, then follow the instructions in Step 3.
-
Sorting: Click
 icon next to Sort By to sort the user map based on the Name, Type, eDirectory Context, and Active Directory Context.
icon next to Sort By to sort the user map based on the Name, Type, eDirectory Context, and Active Directory Context.
-
Importing a User Map
-
Click
 , then select the user map XML file using the Browse button.
, then select the user map XML file using the Browse button. -
Specify an appropriate name for the user map, then click Import.
Exporting a User Map
Select the user map of your choice, click  , to download the user map file.
, to download the user map file.
Refreshing a User Map
If you feel that the mapping have changed since the time you have created a user map, you could refresh them using the same conditions that were used while creating them.
To refresh an old user map, go to the desired user map and then click  . If there are any differences since the time they were created, those entries are highlighted with the
. If there are any differences since the time they were created, those entries are highlighted with the  icon. If you would like to revert changes, click Revert. After verifying the changes, click Save Map.
icon. If you would like to revert changes, click Revert. After verifying the changes, click Save Map.
If the user map is not modified for a time interval specified in the Usermap Refresh Interval (days), a 'Refresh Required' tag is displayed on the user map. For more information, see Changing the NURM Settings.
If scheduled refresh on the user map is enabled, then the 'Last Updated: date and time' tag is displayed on the user map. For more information on user map scheduled refresh, see Usermap Settings.
To view the modified user maps based on the scheduled refresh time, click SHOW SCHEDULED REFRESH LOGS. You can hover the cursor over the user map name to view the users added or removed from that user map.
Deleting a User Map
Select the user maps that you want to delete, then click  .
.
7.4.4 Mapping Rights
Using this feature, you can map rights to AD users on a specific NSS volume. While doing so, you can choose to remove eDirectory trustees from the NSS file system and migrate the eDirectory IDs (owner, modifier, archiver, metadata modifier, and deletor) to AD users.
To map rights:
-
Click
 .
. -
Select a volume on which you want to map rights to AD users, then select the source of user mapping:
-
NetIQ IDM: If you select this option, then directly go to Step 3.
NOTE:When IDM is used, the connection to eDirectory is established with secure SSL port 636. For information on creating user map using IDM, see the NetIQ Identity Manager 4.7 Documentation.
-
User Map: If you select this option, choose the appropriate user map name, then click Show. The user map is displayed along with the rights that will be assigned to the AD users. You can hide the user map and rights details using the Hide button. You can also select multiple user maps and apply rights.
-
-
Enable the following options as needed:
-
Apply to Salvage: Applies rights to AD users on the salvaged files and folders.
-
Remove eDirectory Trustees: After assigning AD users as trustees, the eDirectory users will be removed from the NSS file system as trustees.
-
Migrate IDs: Assign eDirectory trustee IDs (owner, modifier, archiver, metadata modifier, and deletor) to AD users.
-
-
Click Apply.
In the Map Rights page, you can delete, view status, view logs, and download logs of a mapped rights.
-
Delete: Select the map rights to be deleted, then click
 .
.NOTE:After deletion, you can no longer synchronize rights on the volume using the deleted map rights. Resynching of mapped rights is possible only using the user-rights-map command line utility
-
View Status: Select the map rights, then point the cursor to progress to view the updated status of the map rights.
-
View and Download Log: Select the map rights, click View under the Log column. The Log Viewer page is displayed, click Download to copy the log file.
7.4.5 Viewing Rights
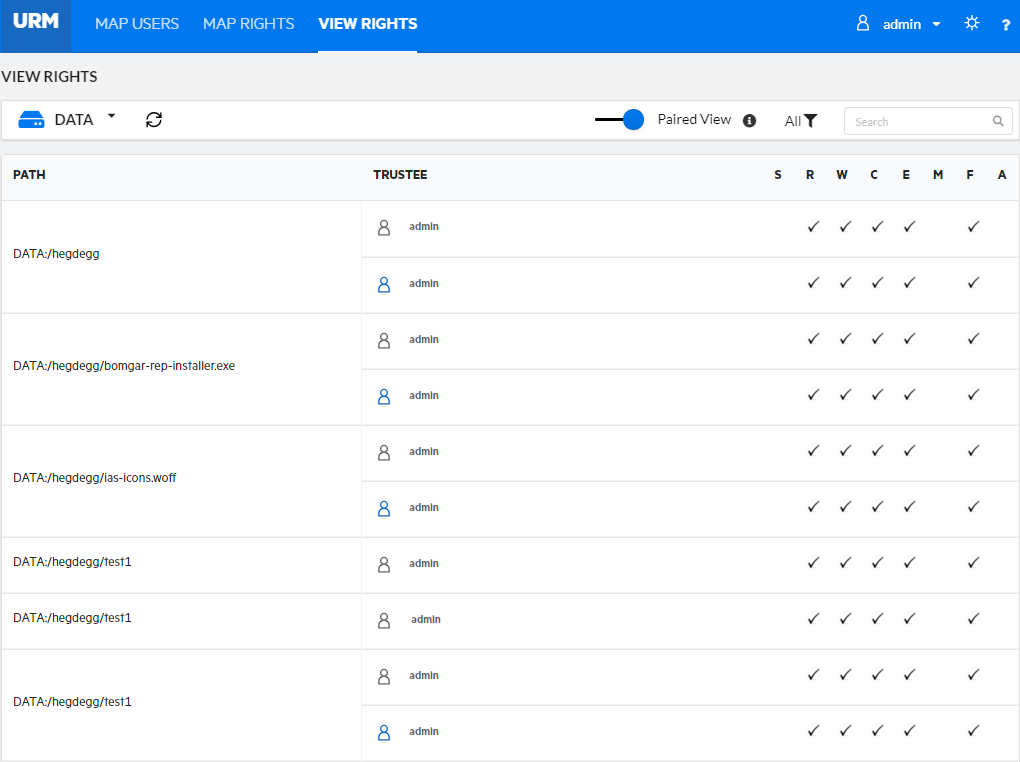
Using this feature, an administrator can view the explicit rights of both eDirectory and Active Directory users on the selected volume. This is the only tool that allows the administrators to view the rights of both AD and eDirectory users in a consolidated view.
To view rights:
-
Select the volume name from the drop-down list. The explicit rights are displayed along with the path, trustee, and rights information.
The trustees with the same path are grouped together for better understanding of the view rights.
-
Enable the Paired View option to display the eDirectory and Active Directory trustee paired view (with common path). Point your browser to
 icon to view the mapping (IDM or User Map) selected for viewing rights.
icon to view the mapping (IDM or User Map) selected for viewing rights.
In View Rights page, you can refresh, filter, and search the rights of both eDirectory and Active Directory users.
-
Refresh: Click
 icon to view the updated list of explicit rights for both eDirectory and Active Directory users on the selected volume.
icon to view the updated list of explicit rights for both eDirectory and Active Directory users on the selected volume. -
Filter: Click
 icon to filter the view rights based on Users-Mapped, Users-Not Mapped, Groups-Mapped, Groups-Not Mapped, ACL-Matched, and ACL-Not Matched. This filter option is available only for the paired view.
icon to filter the view rights based on Users-Mapped, Users-Not Mapped, Groups-Mapped, Groups-Not Mapped, ACL-Matched, and ACL-Not Matched. This filter option is available only for the paired view. -
Search: Use this option to display only the required path or trustee name in the View Rights page. This option can be used with the Filter to perform a search on the filtered trustees.
HINT:Click the Trustee column title to sort the data either in ascending or descending order.
7.4.6 Changing the NURM Settings
Click  icon at the top right to go to NURM settings page. It includes:
icon at the top right to go to NURM settings page. It includes:
-
Language: Select the appropriate language to be displayed on the NURM page.
-
Log Level: Select the required log level. The supported log levels are Debug, Information, Warning, Error and Fatal. The logs are stored at /var/opt/novell/log/nurm/user-rights-map.log.
-
Contextless Login for eDirectory: Enables or disables the contextless login. By default, this option is enabled. If you would like to always use the FQDN while logging on to NURM, ensure to disable this option.
-
Usermap Refresh Interval (days): Specify the number of days after which the user maps are considered as old and requires a refresh. For example, when you set the value to 6 days: In Map Users page, a 'Refresh Required' tag is displayed only on those user maps that are not modified for 6 days.
-
Select the required mapping to use for View Rights: IDM or User Map. If you have selected User Map, select the appropriate user map name. You can select multiple user maps too.
After changing the NURM settings, click Save.
Usermap Settings
This section provides information on the scheduled refresh, which can be used to refresh the user maps automatically if there are changes in the user maps.
It displays:
-
Whether the scheduled refresh is enabled or disabled
-
If enabled, the time and frequency of the user map refresh
You can enable or disable the Scheduled Refresh option only by using the map-users command-line utility. For more information, see map-users.
NOTE:Before enabling, ensure that the 'OESCommonProxy' user has 'Read' permission on the All Attributes Rights property in the same tree.
7.4.7 NURM Command Line Utility
map-users
Use this utility to generate a user map after specifying the necessary match type, context and so on.
Syntax
map-users
map-users -u <specify the user map name> -a <eDirectory Username> -w <eDirectory password> -s <eDirectory Server IP> -p <eDirectory Connection Port> -l <y|n> -c <eDirectory context> -st <y|n> -t <specify the match type as user2user, group2group, or container2group> -m <specify the matching attribute as cn2sam> -A <AD username> -W <AD user password> -S <specify the AD server IP or domain name> -P <specify the AD server connection port> -L <y|n> -C <specify the Active Directory context> -ST <y|n>
Options
- -u, --usermap-file <user map file name>
-
Specify the name of the user map. After a successful execution of the map-users command the user map file is saved with the name that you specify here.
- -a, --user <eDirectory username>
-
Specify the eDirectory username to connect to NURM.
- -w, --password <eDirectory user password>
-
Specify the eDirectory user password.
- -s, --server-ip <eDirectory server IP>
-
Specify the name IP of the eDirectory server.
- -p, --port <eDirectory server connection port>
-
Specify the port number to be used to connect to the eDirectory server.
- -l y|n, --use-ssl-eDir y|n
-
Enables or disables secure connection. Enable this option if you would like a secure connection to the eDirectory server.
- -c, --context <specify the eDirectory server context>
-
Specify the eDirectory server context. For example, ou=users,o=novell.
- -st y|n, --subtree-search y|n
-
Enables or disables subtree search. Enable this option if you would like to consider all the users in the subtree.
- -t, --match-type <specify the match type>
-
Specify the user match type. For example, user2user, group2group, or container2group.
- -m, --matching-attribute <attributes>
-
Specify the match attributes. For example, cn2sam. As of now only cn2sam is supported.
- -sr enable|disable, --scheduled-refresh enable|disable
-
Enables or disables the schedule refresh of user maps. If you enable this option, it is mandatory to use --scheduled-refresh-time with this option.
- -srt, --scheduled-refresh-time <MM(0-59) HH(0-23) DD(0-31)>
-
Specify the time in which the user maps need to be refreshed. This option should be used only with --scheduled-refresh.
- -A, --USER <specify the AD user name>
-
Specify the fully qualified domain name (FQDN) of the AD user.
- -W, --PASSWORD <AD user password>
-
Specify the AD user password.
- -S, --SERVER-IP <specify the AD server IP or domain name>
-
Specify the IP address or domain name of the AD server that you would like to connect to.
- -P, --PORT <specify the AD server connection port>
-
Specify connection port with which you would like to connect to the AD server.
- -L y|n, --USE-SSL-AD y|n
-
Enables or disables secure connection. Enable this option if you would like a secure connection to the AD server.
- -C, --CONTEXT <specify the AD server context>
-
Specify AD server context.
- -ST y|n, --SUBTREE-SEARCH y|n
-
Enables or disables subtree search. Enable this option if you would like to consider all the users in the subtree.
- -h, --help
-
Displays the usage information of the command.
Examples
-
For an interactive user map generation, use the following command and follow the on screen instructions:
map-users
-
To map users by providing all the arguments:
map-users -u mkt-usr-map -a root -w pa55word -s 192.168.1.1 -p 636 -l y -c ou=users,o=mkt -st y -t user2user -m cn2sam -A cn=administrator,cn=users,dc=acme,dc=com -W Pa55word@@ -S 192.168.1.2 -P 636 -L y -C cn=users,dc=acme,dc=com -ST y
This command creates a user map with the following details:
-
Saves the user map as “mkt-usr-map”
-
Connects to the eDirectory server (192.168.1.1) with root credentials, context as ou=users,o=mkt, match type as user to user, matching attributes as CN to SAM, and searches the entire subtree while generating the user map. The connection type used is SSL using port 636.
-
Connects to the AD server (192.168.1.2) using the administrative credentials, context as cn=users,dc=acme,dc=com, and searches the entire subtree while generating the user map. The connection type used is SSL using port 636.
-
-
To schedule a refresh of all user maps available in the OES tree:
map-users --scheduled-refresh enable --scheduled-refresh-time "30 9 4"
This command schedules a cron job (scheduled refresh) to execute at 9:30 AM on every 4 days.
user-rights-map
Use this utility to map the rights of the mapped eDirectory and Active Directory users, groups, and containers. The mapped rights information is stored in a file and assigned an ID. Using this id, you can synchronize the rights of the users.
The User Rights Map GUI runs as a wwwrun user and user-rights-map utility runs as a root user. Do not use GUI or CLI alternatively for mapping rights, it might cause issues with the assigned ACLs.
Syntax
user-rights-map -l
user-rights-map -L
user-rights-map -v <volume name> [[-u <User Map name 1 or the User Map 1 XML file path>,<User Map name 2 or the User Map 2 XML file path>,...,<User Map name n or the User Map n XML file path> |-i <-U username -P password>]][-a -m -r]
user-rights-map -S -M <map rights id> -O <ad | edir>
Options
- -l, --list-map-rights
-
Lists the id, name of the user map, and the volume for which the rights are mapped.
- -L, --list-usermaps
-
Lists the name of the user map, object mapping type (user to user, group to group, or container to group), eDirectory tree context, and Active Directory server context.
- -v, --volume <VOLUME_NAME>
-
Specify the NSS volume on which rights will be provisioned for the mapped users. The volume name should always be specified in upper case.
- -u, --usermap <user map name or path of the user map xml file>
-
Specify the name of the user map or the path of the user map (.xml) file that contains the mapping details of the eDirectory and Active Directory users, groups, or containers.
NOTE:If you need to perform a sync, you must pass the name of the user map as an input parameter. Whereas, if the sync operation is performed using the user map (.xml) file, it cannot be synced later.
- -i, --use-IDM <-U username -P password>
-
Specify the eDirectory admin credentials (in LDAP format) to authenticate to eDirectory. The user map created using IDM is used for mapping the rights. This option is used only to create a rights map.
- -a, --apply-to-salvage
-
Performs rights mapping on files and folders in the salvage system.
- -m, --migrate-ids
-
Migrates the IDs [owner, archiver, metadata modifier, deletor] of files and folders to the mapped Active Directory users. This operation might take a while to complete.
- -r, --remove-old-trustee
-
Removes the eDirectory user as a trustee on the files and folders after successfully mapping the user rights. Removes the Active Directory or eDirectory user as a trustee on the files and folders when used with -S, -O and -m options. This operation is irreversible.
- -d, --delete-trustee
-
Deletes the eDirectory or Active Directory user as a trustee from the VIEW RIGHTS page, if the corresponding paired Active Directory or eDirectory trustee rights are removed on the selected path.
- -S, --sync
-
Synchronizes the rights for both the eDirectory and Active Directory trustees. It is mandatory to use the sync option with the -M and -O options.
NOTE:The sync operation only synchronizes rights (applicable to salvage option). When creating the user map, if the options migrate-ids or remove-old-trustee are passed, they are ignored.
- -M, --map-rights-id <arg>
-
Specify the id of the map rights operation. It also works with IDM rights map, but requires -U and -P options to provide eDirectory admin credentials. This option is used only with the sync option.
- -O, --overwrite-with <ad | edir>
-
You must either pass ad or edir as an input parameter. When the ad parameter is passed, the rights of the eDirectory trustees are overwritten with the rights of the Active Directory trustees. When the edir is passed, the rights of the Active Directory trustees are overwritten with the rights of the eDirectory trustees. This option is used only with the sync option.
- -h, --help
-
Displays the usage information of the command.
NOTE:The user rights map log information is located at /var/opt/novell/log/nurm/userrights-map.log.
Examples
-
Provision the rights on all files and folders of the volume MKTVOL, including the ones in the salvage system.
user-rights-map -v MKTVOL -u /root/temp/UserMap.xml -a -m -r
After successful execution of the user-rights-map operation, all the files and folders are provisioned with rights, all the ids are migrated, and the eDirectory user is removed as a trustee.
NOTE:You can pass multiple user map names, multiple user map (xml) files, or both user map names and user map (xml) files as an input parameter (with comma separated). For example, user-rights-map -v MKTVOL -u /root/temp/UserMap.xml,/root/temp/Map2.xml,usermap2 -a -m -r.
-
To list the user maps:
user-rights-map -L or
user-rights-map --list-usermaps
-
To list the user rights map ids:
user-rights-map -l or
user-rights-map --list-map-rights
-
After the sync, the rights of the AD trustees are overwritten with the rights of eDirectory trustees. The rights of the Active Directory user2 are RWF and the rights of eDirectory user2 are FMA on file2:
user-rights-map -S -M 11 -O edir -U cn=admin,o=novell -P novell
After successful execution of the command, the rights of Active Directory user2 are FMA and the rights of eDirectory user2 are FMA on file2.
-
After the sync, the rights of the eDirectory trustees are overwritten with the rights of Active Directory trustees. The rights of the eDirectory user2 are RWF and the rights of Active Directory user2 are FMA on file2:
user-rights-map -S -M 1 -O ad
After successful execution of the command, the rights of eDirectory user2 are FMA and the rights of Active Directory user2 are FMA on file2.
-
To synchronize rights between eDirectory and AD trustees (two way sync):
user-rights-map -S -M 2 -O edir -m -r
Synchronizes the rights of eDirectory trustees with AD trustees using the map rights job id “2”. During the sync process, it overwrites the Active Directory trustees with eDirectory trustees, migrates all the IDs, and the eDirectory trustee information is removed from the source after the sync process.
user-rights-map -S -M 2 -O ad -m -r
Synchronizes the rights of AD trustees with eDirectory trustees using the map rights job id “2”. During the sync process, it overwrites the eDirectory trustees with AD trustees and migrates all the IDs, and the AD trustee information is removed from the source after the sync process.
-
To delete the rights of eDirectory or Active Directory trustees:
user-rights-map -S -M 2 -O edir -d
Deletes the rights of all eDirectory trustees (whose corresponding paired Active Directory trustee rights are removed) using the map rights job id “2”.
user-rights-map -S -M 2 -O ad -d
Deletes the rights of all Active Directory trustees (whose corresponding paired eDirectory trustee rights are removed) using the map rights job id “2”.