Overview
PKI Services Manager provides certificate validation services. One or more centrally managed installations of PKI Services Manager can provide certificate validation services for multiple Micro Focus applications.
Applications that use PKI Services Manager for certificate validation are referred to in this guide as PKI Services Manager clients. A PKI Services Manager client can be a Micro Focus client application authenticating a server host or a Micro Focus server application authenticating a client user. For example:
-
A Reflection for Secure IT UNIX or Windows server verifying a certificate presented by an SSH client.
-
A Reflection for Secure IT UNIX client verifying a certificate presented by an SSH server.
-
A Reflection X Advantage session verifying a certificate presented for authentication by an X application host.
-
A web-based Reflection Security Gateway or Reflection for the Web session that is configured to support TLS 1.2 certificate validation.
-
The pki-client command line utility, which is provided with PKI Services Manager for testing certificate validation.
How it Works
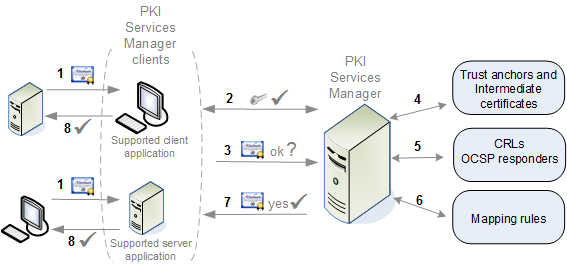
-
During the authentication portion of the connection process, a server host or client user sends a certificate to a Micro Focus application (the PKI Services Manager client application). Before authentication can continue, the Micro Focus application needs to know that the certificate is valid and can be used for authentication by this host or client.
-
The client application connects to PKI Services Manager and uses an installed public key to authenticate the PKI Services Manager server.
-
The client application sends the certificate to PKI Services Manager.
-
PKI Services Manager checks that the certificate has not expired, is valid for the current use, and meets all attribute requirements. If these conditions are met, it verifies the chain of trust using your configured trust anchors and available intermediate certificates.
-
If required by your configuration, or by conditions set within the certificate, PKI Services Manager checks to be sure that the certificate has not been revoked. Depending on configuration, this check may use Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol responders (OCSP).
-
If required by your application, PKI Services Manager uses the mapping rules you have configured to determine which identity or identities are allowed to authenticate using this certificate.
-
PKI Services Manager replies to the client application, letting it know if the certificate is valid and providing information about allowed identities.
-
The PKI Services Manager client application allows or denies authentication of the host or client that presented the certificate based on the information it receives from PKI Services Manager.
More information