1.5 Designing and Creating Secure Solutions
Reflection provides support for a number of secure solutions, including secure sessions for data in motion, Information Privacy features that support PCI-DSS, and enforcement of Trusted Locations. Using Reflection, you can:
Creating secure sessions for data in motion
Set up secure sessions for a number of secure protocols including FIPS 140-2 validation, SSL/TLS encryption, SSH, Kerberos, SOCKS, and PKI. See Create SSL/TLS or SSH Session Documents in the Deployment Guide.
Setting up Information Privacy
Set up Information Privacy to help comply with PCI-DSS requirements, including redaction of sensitive data such as credit card or social security numbers.

You can also set up the Reflection API to log access to unredacted data. See Configure Information Privacy in the Deployment Guide.
Defining trusted locations
Define Trusted Locations to differentiate safe files from potentially harmful files. When a file is in a trusted location, it’s files are assumed to be safe. If you try to save a file in a location that is not trusted, Reflection warns that it will not be able to reopen the file.
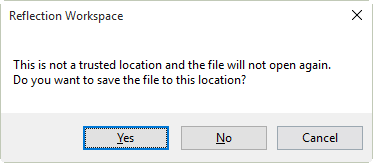
Reflection enforces trusted locations by default, so if you want to save sessions in directories that are not default trusted locations, you’ll have to define these locations or disable the Trusted Locations feature. See Add Trusted Locations.