OpenText NetIQ Identity Governance
Protect all data with simplified compliance and user access review processes

Overview
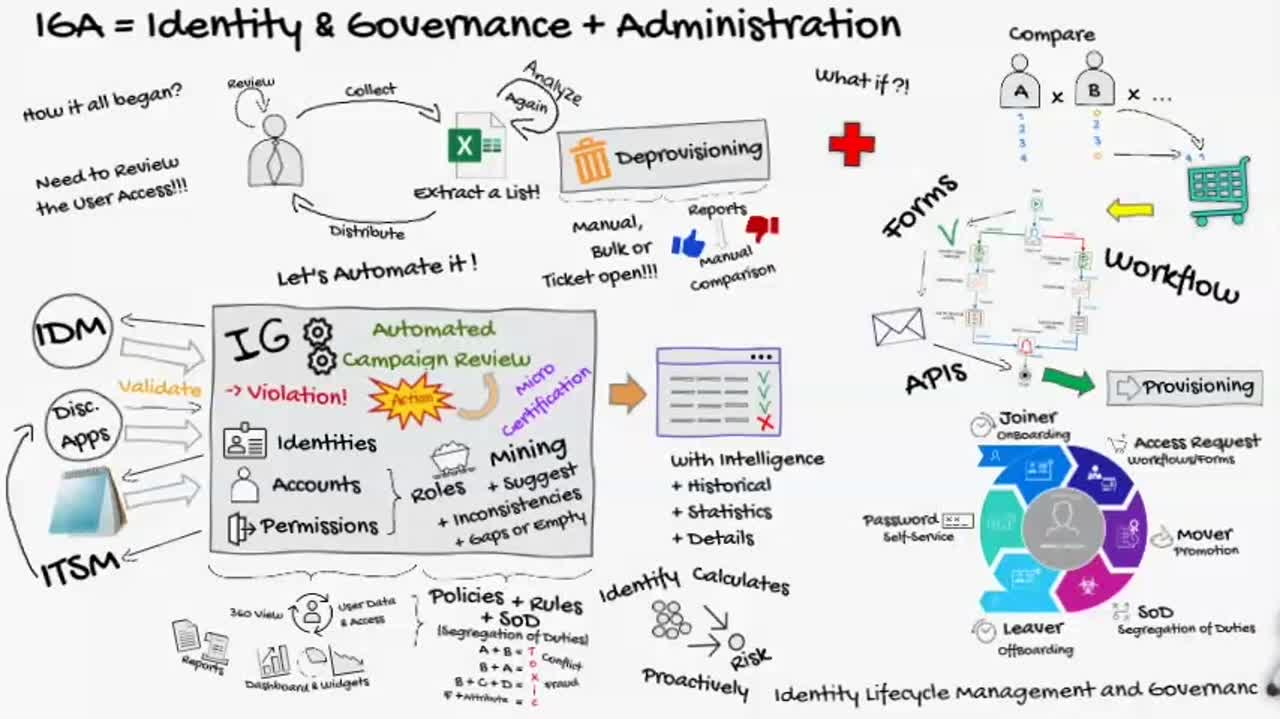
Why choose NetIQ Identity Governance?
-
Identity-powered governance
Accelerate access certification, reduce the risk of inappropriate access, provide analytics for users in technical and business roles, and satisfy auditors.
-
Automated access certifications
Ensure access certifications stay on schedule with automatic reminders and progress updates, including decision support for approvers and issue escalation for administrators.
-
Real-time adaptive governance
Enable continuous risk mitigation, adapt to real-time changes and events, and automatically initiate compliance reviews.
-
Business insight access
Inform decisions about user access by delivering crucial business insights through the review and approval interfaces.
-
Centralized platform
Save time and money managing secured services and resources through a central point of access.
How NetIQ Identity Governance can benefit business
Minimize risk and boost efficiency by easily governing application and data access and automating access review and recertification processes.
-
Achieve compliant access levels
Boost compliance, optimize resource allocation, and mitigate the risk and cost of data breaches.
-
Automate administrative tasks
Eliminate manual, error-prone processes to enhance operational efficiency, establish new business models, and prevent compliance violations.
-
Adhere to government mandates
Navigate evolving government mandates related to your digital services while ensuring compliance with your organization’s privacy and segregation of duties requirements.
-
Optimize resource allocation
Easily govern access to sensitive information so information handlers can focus on their primary responsibilities, reducing the cost and risk of potential data breaches.
Features
-
Access governance
Governs access to all resources across your environment, whether you choose to deploy on premises or via SaaS.
-
Entitlement collection
Collects and visualizes identities and entitlements across your entire environment.
-
Approval management
Automates application fulfillment with a user-friendly, self-service access request and approval system.
-
Analytics access
Reduces rubber stamping with analytics that provide business context and risks associated with each request.
-
Continuous governance
Triggers access reviews on high-risk changes, with interventions needed only for exceptions.
Explore the advantages of OpenText and partner services
Professional Services
OpenText Consulting Services combines end-to-end solution implementation with comprehensive technology services to help improve systems.
- Plan, govern, and execute your journey to IT valueIT Professional Services
Partners
OpenText helps customers find the right solution, the right support and the right outcome.
- Search OpenText's partner directoryFind a Partner
- Industry leading organizations that enhance OpenText products and solutionsStrategic Partners
- Build better software productsOEM Solutions
- Explore OpenText's Partner solutions catalogApplication Marketplace
Training
OpenText Learning Services offers comprehensive enablement and learning programs to accelerate knowledge and skills.
- Meet the demands of all types of users for effective adoptionLearning Services
- Get expertise as neededFlexible Credits
Communities
Explore our OpenText communities. Connect with individuals and companies to get insight and support. Get involved in the discussion.
- Explore ideas, join discussions and networkOpenText Community
Leaders trust OpenText
See how customers are succeeding with NetIQ Identity Governance.
See more success stories
KMD deploys adaptive identity governance to deliver transparency and major productivity gains
Learn moreNetIQ Identity Governance resources
What is identity governance and administration?
Learn moreWhat is identity and access management?
Learn moreWhat is data access governance?
Learn moreIdentity governance: The power of data policy (1 of 3)
Watch the videoIdentity governance: Workflow as remediation (2 of 3)
Watch the videoIdentity governance: Microcertifications as remediation (3 of 3)
Watch the videoBusiness roles | NetIQ Identity Governance
Watch the videoRisk scoring | NetIQ Identity Governance
Watch the videoData policy | NetIQ Identity Governance
Watch the videoDepartment of defense contractor stays competitive with identity governance
Read the blogClosing the door on access mistakes: The role of identity governance
Read the blogScaling identity governance and administration to cover the whole enterprise
Read the blogKuppingerCole Leadership Compass for identity governance and administration
Read the report

