5.1 Authentication Framework
To guard against unauthorized access, Access Manager supports a number of ways for users to authenticate. You configure authentication at Identity Server by creating authentication contracts that Access Manager components (such as an Access Gateway) can use to protect a resource.
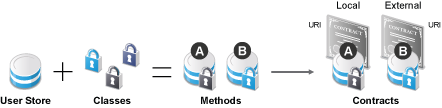
Figure 5-1 illustrates the components of a contract.
Figure 5-1 Local Authentication
|
User stores |
User stores to which users authenticate in the back-end. You set up your user store while creating an Identity Server cluster configuration. See Configuring Identity User Stores. |
|
Classes |
Implements a particular authentication type (name/password, RADIUS, X.509) or means of obtaining credentials. It specifies how Identity Server requests for the authentication information and what it must do to validate credentials. See Creating Authentication Classes. |
|
Methods |
The pairing of an authentication class with one or more user stores, and whether the method identifies a user. See Configuring Authentication Methods. |
|
Contracts |
The basic unit of authentication. Contracts can be local (executed at the server) or external (satisfied by another Identity Server). Contracts are identified by a unique URI that can be used by Access Gateways and agents to protect resources. Contracts are comprised of one or more authentication methods used to uniquely identify a user. You can associate multiple methods with one contract. See Configuring Authentication Contracts. |
This section explains the following topics: