6.2.1 Understanding RBAC in Access Manager
Role-based access control (RBAC) provides a convenient way to assign a user to a particular job function or set of permissions within an enterprise, to control access. As an administrator, you probably have defined a set of roles for your needs. Your roles might include Employee, Student, Administrator, Manager, and so on. You might have web resources that you want available to all employees, or only to managers, as shown in Figure 6-1.
Figure 6-1 Traditional RBAC
Access Manager supports core RBAC functionality by providing user role mapping and the mapping of roles to resource rights and permissions. User role mapping is a primary function of a Role policy. Role mapping to resource rights is accomplished through Authorization policies. When creating a role, you assign users to the role, based on attributes of their identities. You also specify the constraints to place on the role.
Figure 6-2 RBAC Using a Policy
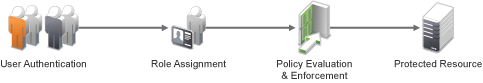
As shown in Figure 6-2, during user authentication, the system checks the existing Role policy to determine which roles that a user must be assigned to. After authentication, assigned roles can be used as evaluated conditions of an Authorization policy.
Web server applications can also be configured to use roles for access control. For these applications you can use Access Manager to assign the users to the required roles. You can use Access Gateway Identity Injection policies to inject the assigned roles into the HTTP header that is sent to the web server.
The following examples describe ways to use roles in Access Manager: