Integrate with the IIS Reverse Proxy
Integration with an IIS reverse proxy is used for the following purposes:
- Enable IIS access to products like Host Access for the Cloud, Reflection for the Web, or Metering.
- Use SiteMinder for authentication.
- Comply with Common Criteria security requirements.
Note
When integrated with IIS, a common/shared certificate and private key is used to provide security (HTTPS) for the Cluster DNS entrypoint and IIS.
Refer to the Microsoft IIS help documentation for instructions on how to install IIS and its features.
Requirements
- IIS 8.0 or higher
- The IIS URL Rewrite module must be installed. See IIS URL Rewrite for information on how to install this.
- IIS Application Request Routing (ARR) 3.0 or later is required. See IIS Application Request Routing for information on how to install this.
Additional Requirement when using Host Access for the Cloud
- The IIS WebSockets protocol must be enabled. See IIS 8.0 WebSocket Protocol Support for information on how to enable this protocol.
Configure the IIS Reverse Proxy
-
Launch the Internet Information Services (IIS) Manager, navigate to the website you want to use, and open the URL Rewrite feature.
-
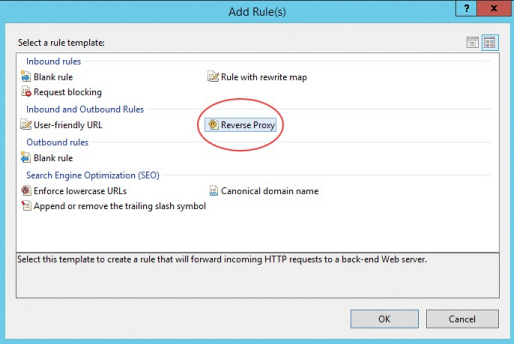
Choose the Add Rule(s) action and add the Reverse Proxy rule.
-
For the inbound rule, enter the Cluster DNS name, and de-select Enable SSL Offloading.
-
Check the outbound rule Rewrite the domain names... and enter the hostname or IP address of the IIS server in the To: box.
-
Click OK to create the new Reverse Proxy Rule.
Configure MSS to use IIS as the front-end
-
Log in to the MSS Admin Console at
https://clusterdns/adminconsole. -
From the drop-down menu, click Cluster Management.
-
Under Services, find the service named
mss-mss-server. -
Click
 Edit Properties, and add this key/value pair:
Edit Properties, and add this key/value pair:management.server.iis.urlhttps://<IIS server NetBIOS hostname>/mss- Example:
https://iishostname/mss
Note
- When using IIS Single Sign-On authentication, use a hostname without dots in the
management.server.iis.urlproperty. This will help your browser recognize the IIS host as part of your intranet and enable transparent Integrated Windows Authentication (IWA). - Alternatively, you can use a hostname with dots, like an FQDN. However, in this scenario, you need to configure your browser to trust the site for transparent Integrated Windows Authentication (IWA) to function properly. Refer to your browser's Help documentation for detailed instructions.
- This note does not apply to SiteMinder authentication.
-
Click
 Redeploy All.
Redeploy All.Note
Be aware that end users may be affected when redeploying a service.
Additional configuration when using Host Access for the Cloud
-
Log in to the MSS Admin Console at
https://clusterdns/adminconsole. -
From the drop-down menu, select Cluster Management.
-
Under Services, find the service named
hacloud-session-server. -
Click
 Edit Properties, and add the following key/value pairs:
Edit Properties, and add the following key/value pairs:websocket.compression.enablefalse
server.compression.enabledfalse
websocket.allowed.originshttps://<IIS server name or IP address>- Example:
https://iishostname
management.server.iis.urlhttps://<IIS server name>/mss- Example:
https://iishostname/mss
Note
- When using IIS Single Sign-On authentication, use a hostname without dots in the
management.server.iis.urlproperty. This will help your browser recognize the IIS host as part of your intranet and enable transparent Integrated Windows Authentication (IWA). - Alternatively, you can use a hostname with dots, like an FQDN. However, in this scenario, you need to configure your browser to trust the site for transparent Integrated Windows Authentication (IWA) to function properly. Refer to your browser's Help documentation for detailed instructions.
- This note does not apply to SiteMinder authentication.
-
Click
 Redeploy All.
Redeploy All.Note
Be aware that end users may be affected when redeploying a service.
Configure the Cluster DNS entrypoint to use IIS as the front-end
-
Set the Cluster DNS name to the IIS server's hostname or FQDN.
-
Set the Cluster certificate to use the same certificate and private key that's used by the IIS website.
-
Add the IIS certificate to the Trusted Root Certificate Authorities in Windows, using the "Manage Computer Certificates" MMC snap-in. This enables IIS to trust the cluster.
After configuring the IIS Reverse Proxy
When using IIS Single Sign-On authentication
Then, refer to the MSS Administrator Guide to configure MSS for Single Sign-on for IIS authentication.
When using SiteMinder authentication
Then, refer to the MSS Administrator Guide to configure MSS for SiteMinder authentication.